

| Allow 30 Minutes |
 |
|
Enabling Digi-Access™ client certificates for two factor authentication will take 30 minutes (or less). Configure the 2X Application Server by following these simple steps (for full detailed instructions and screenshots, read the IIS Support [1] pages):
|
1. Download and save these two certificates:
Digi-Sign CA Digi-Access™ Xs [3] 2. On the server, click the Start button, select Run and type MMC, before clicking the 'OK' button 3. You should now be in the Microsoft Management Console and should follow these steps: 4. Now all you need to do is import the Digi-Access™ Root certificate, following these steps: 5. Then import the Digi-Access™ intermediate CA certificate, as follows: 6. Go to Windows Administrative Tools and open the properties window for the website that you have enabled SSL on. Open the Directory Security by right clicking on the Directory Security tab and then follow these steps: 7. Start Internet Services Manager, or open the MMC that contains the IIS snap-in. |
Read these instructions to find the OU Codes [4] for your customer.
| Allow 5 Minutes |
 |
|
For every 2X Digi-Access™ customer, a unique Digi-Access™ RA is activated so that the customer can manage the end users Digi-Access™ certificates. Once the order [6] for your customer has been approved, the Digi-Access™ RA is activated and you are notified automatically.
To complete the 2X Application Server configuration you require the two unique organizationalUnitName [OU [7]] codes. These are provided automatically in the Digi-Access™ tab of the Digi-CA™ Control Centre (Digi-Access™):
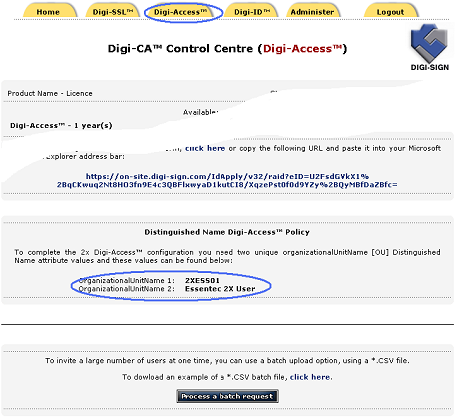
1. will have access to the Digi-Access™ RA because you are managing and issuing certificates to the end users; or
2. your customer's Administrator is managing the certificates and therefore you do not have access to the Digi-Access™ RA
In the case where you do not have access the to Digi-Access™ RA, ask your customer's Administrator to provide the organizationalUnitName 1 and organizationalUnitName 2 cosdes as shown on the Digi-Access™ tab of the Digi-CA™ Control Centre (Digi-Access™)
Links:
[1] http://www2.digi-sign.com/support/digi-access/iis
[2] http://www.digi-sign.com/downloads/certificates/dsroot/Digi-Sign_Root_CA.cer
[3] http://www.digi-sign.com/downloads/certificates/digi-access/Digi-Sign_CA_Digi-Access_Xs.cer
[4] http://www2.digi-sign.com/arp/2x/help/ou
[5] http://www2.digi-sign.com/digi-access/distribute
[6] http://www2.digi-sign.com/arp/ordering
[7] http://www2.digi-sign.com/arp/2x/help/configure#ou