- Do I need to install all the certificates that I received?



This is the main Digi-SSL™ Support page and provides all the main support pages you require to own and use your Digi-SSL™ Certificates.
Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
You can browse this Support Directory or you can view the Digi-SSL™ KnowledgeBase [2] that contains specific Questions & Answers [Q&A](this is free today but will be a 'Subscription Only' service soon).
Alternatively, you may wish to search all of the Digi-SSL™ pages using the search facility below.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
The first part of enrolling for your Digi-SSL™ [5] Certificate is to generate a Certificate Signing Request [CSR]. CSR generation is wholly dependent on the software you use on your webserver. Select your webserver software from the list below after reading the following general points:
The Common Name field should be the Fully Qualified Domain Name [FQDN] or the web address for which you plan to use your Certificate, e.g. the area of your site you wish customers to connect to using SSL. For example, a Digi-SSL™ Certificate issued for digi-sign.com will not be valid for secure.digi-sign.com. If the web address to be used for SSL is secure.digi-sign.com, ensure that the common name submitted in the CSR is secure.digi-sign.com
If your webserver software does not appear on the list, please contact support [6] with full details of your webserver software and we will contact you with further instructions.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
A CSR is a file containing your certificate application information, including your Public Key. Generate your CSR and then copy and paste the CSR file into the web form in the enrollment process:
Generate keys and certificate:
To generate a pair of private key and public Certificate Signing Request (CSR) for a webserver, replace "server" below and "myserver" with the total hostname you are using in the following command:
This creates two files. The file myserver.key contains a private key; do not disclose this file to anyone. Carefully protect the private key.
In particular, be sure to backup the private key, as there is no means to recover it should it be lost. The private key is used as input in the command to generate a Certificate Signing Request (CSR).
You will now be asked to enter details to be entered into your CSR.
What you are about to enter is what is called a Distinguished Name or a DN.
For some fields there will be a default value, If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]: GB
State or Province Name (full name) [Some-State]: York
Locality Name (eg, city) []: York
Organization Name (eg, company) [Internet Widgits Pty Ltd]: MyCompany Ltd
Organizational Unit Name (eg, section) []: IT
Common Name (eg, YOUR name) []: mysubdomain.mydomain.com
Email Address []:
Please enter the following 'extra' attributes to be sent with your certificate request
A challenge password []:
An optional company name []:
-----
Use the name of the web server as Common Name (CN). If the domain name is mydomain.com append the domain to the hostname (use the fully qualified domain name).
The fields email address, optional company name and challenge password can be left blank for a web server certificate.
Your CSR will now have been created. Open the server.csr in a text editor and copy and paste the contents into the online enrollment form when requested.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
A CSR is a file containing your certificate application information, including your Public Key. Generate your CSR and then copy and paste the CSR file into the web form in the enrollment process:
Generate keys and certificate:
To generate a pair of private key and public Certificate Signing Request (CSR) for a web server, "server", use the following commands:
256-bit Certificate:
Openssl req -new -newkey rsa: 2048 -keyout myserver.key -nodes -out server.csr
This creates two files. The file myserver.key contains a private key; do not disclose this file to anyone. Carefully protect the private key.
In particular, be sure to backup the private key, as there is no means to recover it should it be lost. The private key is used as input in the command to generate a Certificate Signing Request (CSR).
You will now be asked to enter details to be entered into your CSR.
What you are about to enter is what is called a Distinguished Name or a DN.
For some fields there will be a default value, If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]: GB
State or Province Name (full name) [Some-State]: York
Locality Name (eg, city) []: York
Organization Name (eg, company) [Internet Widgits Pty Ltd]: MyCompany Ltd
Organizational Unit Name (eg, section) []: IT
Common Name (eg, YOUR name) []: mysubdomain.mydomain.com
Email Address []:
Please enter the following 'extra' attributes to be sent with your certificate request
A challenge password []:
An optional company name []:
-----
Use the name of the web server as Common Name (CN). If the domain name is mydomain.com append the domain to the hostname (use the fully qualified domain name).
The fields email address; optional company name and challenge password can be left blank for a webserver certificate.
Your CSR will now have been created. Open the server.csr in a text editor and copy and paste the contents into the online enrollment form when requested.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
To enable SSL on a virtual site:
Go to the Server Management screen.
Click the green icon (Wrench for RaQ4, Pencil for XTR) next to the virtual site on which you want to enable SSL. The Site Management screen appears.
Click Site Settings on the left side.
(Then 'General' for XTR)
Click the check box next to Enable SSL.
Click Save Changes.
The RaQ4/XTR saves the configuration of the virtual site.
Generate a self-signed certificate:
Once SSL is enabled, the user must now create a self-signed certificate. An external authority will sign the self-signed certificate later.
Go to the Server Management screen.
Click the green icon (Wrench for RaQ4, Pencil for XTR) next to the SSL enabled virtual site
Click SSL Settings on the left side.
The Certificate Subject Information table appears.
Enter the following information:
Country Enter the two-letter country code
State Enter the name of the state or County
Locality Enter the city or locality
Organization Enter the name of the organization
Organizational Unit As an option, enter the name of a department
Select Generate self-signed certificate from the pull-down menu at the bottom.
Click Save Changes.
The RaQ4/XTR processes the information and regenerates the screen with the new self-signed certificate in the Certificate Request and Certificate windows.
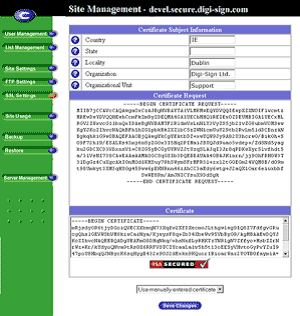
Copy the entire contents of the certificate request, including:
-----BEGIN CERTIFICATE REQUEST-----
and
-----END CERTIFICATE REQUEST-----
for use during the purchasing process.

Cobalt User Guide available at:
http://www.sun.com/hardware/serverappliances/documentation/manuals.html [7]

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
Login to the Site Administrator or Appliance Administrator and select the site to administer.
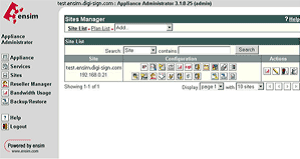
Select Services
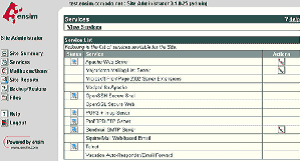
Select the Actions box next to Apache Web Server and then select SSL Settings
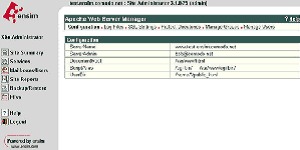
Select Generate and fill in the required details, the site name will automatically be entered into the Common Name field, ensure this is correct and contains the Fully Qualified Domain Name (e.g. secure.digi-sign.com, www.digi-sign.com [8], support.digi-sign.net
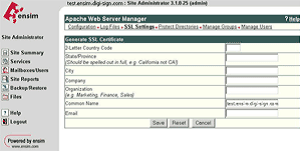
Select Save and you are presented with the RSA Key and the Certificate Request (CSR)
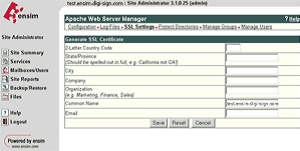
Copy the Certificate Request into a text editor; this will be required when you purchase your certificate. Do not delete this request, as it will be needed during the installation of your SSL certificate.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
NOTE: Keys and certificates are managed through three scripts: genkey, getca and genreq. These are part of the normal Stronghold distribution. Keys and certificates are stored in the directory$SSLTOP/private/, where SSLTOP is typically /usr/local/ssl.
To generate a key pair and CSR for your server:
Back up your key file and CSR on a floppy disk and store the disk in a secure location. If you lose your private key or forget the password, you will not be able to install your certificate.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
1. Click SSL on your control panel home page.
2. Enable SSL for the domain in the list.
3. Click the link at the top of the form that appears.
4. On the page that appears, confirm your details by clicking the Submit button:
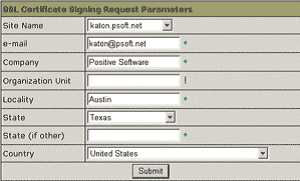
These data will be used to generate the certificate. Don't make changes to the data if you are not sure about the purpose of these changes.
5. Follow instructions that appear at the top of the next page.

6. Copy the signing request and private key for later use.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
NOTE: If you are starting IKEYMAN to create a new key database file, the file is stored in the directory where you start IKEYMAN.
To create a new Key Database:

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
NOTE: You must select all the text in the second dialog box, including Begin Certificate and End Certificate when the CSR is requested.
NOTE: You must select all the text in the second dialog box, including Begin Certificate and End Certificate when the CSR is requested.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
A CSR is a file containing your certificate application information, including your Public Key. Generate your CSR and then copy and paste the CSR file into the web form in the enrolment process:
We recommend that you make a note of your password and backup your key, as only you know these, so if you loose them we can't help! A floppy diskette or other removable media is recommended for your backup files

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
We recommend that you make a note of your password and backup your key as these are known only to you, so if you loose them we can't help! A floppy diskette or other removable media is recommended for your backup files.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
Follow these instructions to generate a certificate request (CSR).

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
Since Microsoft ISA 2000 Server does not have a direct interface for generating Certificate Signing Request, you may need to follow the CSR generation instructions for Microsoft IIS4/IIS5/IIS6 web servers [11]

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
The best resource for Microsoft OCS 2007 is to go directly to the Microsoft TechNet site and follow the instructions for sub section 3.6 Configure Certificates for Front End, Web Conferencing and A/V Server Roles [12].
Once you have followed these instructions, then visit sub section 3.7 Configure the Web Components Server IIS Certificate [12].

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
A CSR is a file containing your certificate application information, including your Public Key. Generate your CSR and then copy and paste the CSR file into the web form in the enrollment process or send it via email to your account manager in Digi-Sign:
Generate keys and Certificate Signing Request:

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
Ironport C100 is currently unable to create keys and certificate requests, however, below are some guidelines on how to generate a CSR and install an SSL certificate on your IronPort device:
*** Generate RSA Key and Certificate Request (CSR) ***
Ironport C100 is currently unable to create keys and certificate requests. You can use "openssl" toolkit on Linux/Windows to generate the CSR. Here are the commands you can use:
On a Linux/Windows computer with OpenSSL toolkit installed:
shell> openssl genrsa -des3 -out server.key 2048 openssl req -new -key
shell> servername.key -out server.csr openssl rsa -in servername.key
shell> -out server.key.PEMunsecure
*** Request Certificate from Digi-Sign **
Send the contents of the "server.csr" file to your account manager in Digi-Sign

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
1. Sign onto the Web server and select the server to manage
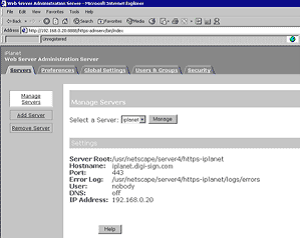
2. Select the Security tab and then Request a Certificate
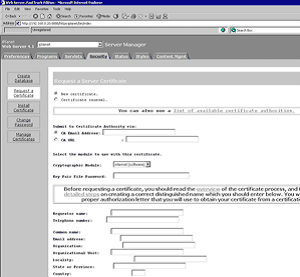
3. Complete the required boxes and click OK
4. An email is then sent to the email address specified containing your CSR
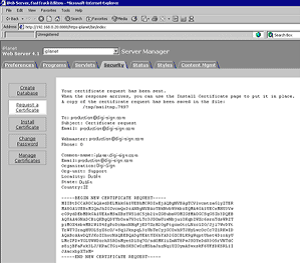
5. The CSR will be required when requesting your certificate.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
1. Restart the administration server by typing the following commands:
2. To request the server certificate, click the Security tab near the top of this page.
3. Select the Request a Certificate link on the left frame.
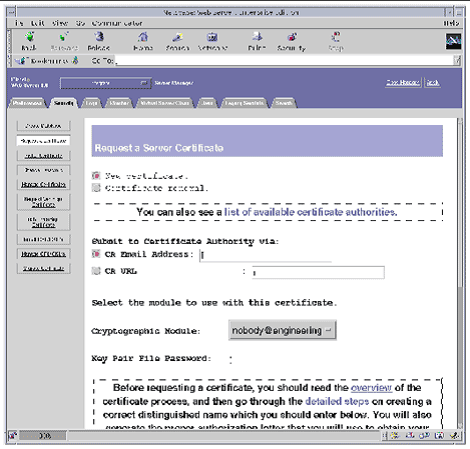
The screenshot depicts the following options:
4. Fill out the form to generate a certificate request, using the following information:
If you can directly post your certificate request to a web-capable certificate authority or registration authority, select the CA URL link. Otherwise, choose CA Email Address and enter an email address where you would like the certificate request to be emailed to.
b. Select the Cryptographic Module you want to use.
Each realm has its own entry in this pull-down menu. Be sure that you select the correct realm. To use the Sun Crypto Accelerator 1000, you must select a module in the form of user@realm-name.
c. In the Key Pair File Password dialog box, provide the password for the user@realm-name that will own the key.
d. Provide the appropriate information for the following fields:
e. Click the OK button to submit the information.
5. Send the CSR to Digi-Sign.
6. Once the certificate is generated, copy it, along with the headers, to the clipboard.
NOTE that the certificate is different from the certificate request and is usually presented to you in text form.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
To request a certificate, perform the following steps:
1. For the Server Manager you must first select the server instance from the drop-down list.
2. Perform the following steps to specify how you want to submit the request for the certificate:
At the end of this process, you may also copy your request in a text format and apply for your certificate online through Digi-Sign website at: http://www.digi-sign.com/product/digi-ssl/ [13] or through your Digi-CA™ [14] Service Account, if you are using the Digi-Sign certificate management system. When prompt, paste your request into a Certificate Signing Request (CSR) box.
3. Select the cryptographic module for the key-pair file you want to use when requesting the certificate from the drop-down list.
4. Enter the password for your key-pair file.
5. Enter your identification information.
You need to provide the following information:
Common Name must be the fully qualified hostname used in DNS lookups (for example, www.yourdomain.com [15]). This is the hostname in the URL that a browser uses to connect to your site. If these two names don't match, a client is notified that the certificate name doesn't match the site name, creating doubt about the authenticity of your certificate.
Email Address is your business email address. This can be used for correspondence between you and Digi-Sign.
Organization is the official, legal name of your company, educational institution, partnership, and so on. You need to verify this information with legal documents (such as a copy of a business license).
Organizational Unit is an optional field that describes an organization within your company. This can also be used to note a less formal company name (without the Inc., Corp., and so on).
Locality is a field that usually describes the city, principality, or country for the organization.
State or Province is usually required, but can be optional.
Country is a required, two-character abbreviation of your country name (in ISO format). The country code for the United States is U.S.
All this information is combined as a series of attribute-value pairs called the distinguished name (DN), which uniquely identifies the subject of the certificate.
Double-check your work to ensure accuracy. The more accurate the information, the faster your certificate is likely to be approved.
6. Click OK.
7. For the Server Manager, click Apply, and then Restart for changes to take effect.
If you chose to email the request, the server composes an email message containing the request and sends the message to Digi-Sign. Typically, the certificate is then returned to you via email.
If for any reason your network security settings or a firewall configuration prevents your server from sending the certificate request via email, copy the entire request string, that should appear on the screen and send it manually to your account manager in Digi-Sign or to Digi-Sign Production Department from a PC, that has access to Internet mail.
Once you receive the certificate from Digi-Sign, you can install it. In the meantime, you can still use your server without SSL.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
In this first step you generate a request for Digi-Sign to issue a certificate. It involves generating a public/private key-pair and identifying the server, the organization using it, and its Webmaster. The private key is encrypted and should never leave your server, except for backup purposes. The public key will become part of the certificate and is therefore sent to Digi-Sign, together with the rest of the information identifying your organization and your server.
To generate a certificate request, you will run the interactive utility genreq and enter the information for which it prompts you.
When the prompt specifies a default value, you can just press return to enter that value, or enter a different value if you prefer.
For an example of how to use genreq, see the following sample genreq session. Before you start, create a directory to store all SSL related files in, for example $ORACLE_HOME/ows2/ssl. To avoid typing long path names or moving files later, you can start genreq from this directory. To run genreq, do the following:

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
A CSR is a file containing your certificate application information, including your Public Key. Generate your CSR and then copy and paste the CSR file into the web form in the enrollment process.
Important Notes on Certificates
Generate a Self-signed Certificate or Certificate Signing Request
Access the domain management function by clicking on the Domains button at the top of the PSA interface. The Domain List page appears.
2. If you have established an IP based hosting account with SSL support, the Certificate button will be enabled.
3. Click the Certificate button. The SSL certificate setup page appears.
4. The Certificate Information: section lists information needed for a certificate signing request, or a self-signed certificate. You must fill out these fields before generating your CSR or self-signed certificate.
5. The Bits selection allows you to choose the level of encryption of your SSL certificate. Select the appropriate number from the drop down box next to Bits.
6. To enter the information into the provided text input fields (State or Province, Locality, Organization Name and Organization Unit Name (optional)) click in the text boxes and enter the appropriate name.
7. To enter the Domain Name for the certificate click in the text box next to Domain Name: and enter the appropriate domain.
8. The domain name is a required field. This will be the only domain name that can be used to access the Control Panel without receiving a certificate warning in the browser. The expected format is www.domainname.com [19] or domainname.com.
9. Click on the Request button.
10. Selecting Request results in the sending of a certificate-signing request (CSR) to the email address you provided in the certificate fields discussed above. When a CSR (certificate signing request) is generated there are two different text sections, the RSA Private Key and the Certificate Request. Do not lose your RSA private key. You will need this during the certificate installation process. Losing it is likely to result in the need to purchase another certificate.
11. Copy and paste the Certificate Request emailed to you into the InstantSSL web form where it requests a CSR (Certificate Signing Request).
12. When you are satisfied that the SSL certificate has been generated or the SSL certificate

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
Follow these instructions to generate a CSR for your Web site. When you have completed this process, you will have a CSR ready to submit to your provider in order to be generated into a SSL Security Certificate.
Access the domain management function by clicking on the Domains button at the top of the PSA interface. The Domain List page appears.
2. If you have an IP based hosting account with SSL support, the Certificate button will be enabled. If you have a name based hosting account the Certificate button will be greyed out. You must have an IP based hosting account to continue.
3. Click the Certificate button. The SSL certificate setup page appears.
4. The Certificate Information: section lists asks for a number of fields to be completed to generate your CSR.
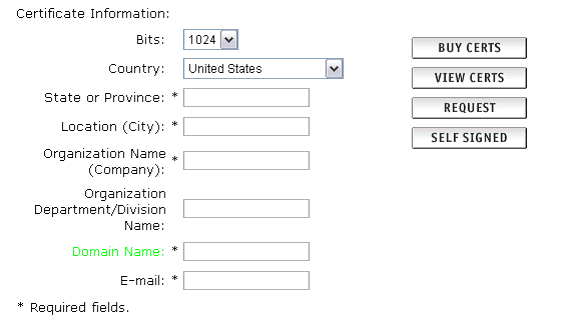
5. The Bits selection allows you to choose the level of encryption of your SSL certificate. Select the appropriate number from the drop down box next to Bits.
6. Enter your details into the State or Province, Locality, Organization Name and Organization Unit Name (optional) fields.
7. Enter your domain name into the Domain Name: field.
8. The domain name is a required field. This will be the only domain name that can be used to access the Control Panel without receiving a certificate warning in the browser. The expected format is www.domainname.com [19] or domainname.com
9. Click on the Request button displayed to the right of your details.
10. Plesk will now email your CSR to the email address provided when you signed up. You will see that the email contains two sections - the RSA Private Key and the Certificate Signing Request. Do not lose your RSA Private Key, you will need this later.
11. Copy and paste the Certificate Request emailed to you into your SSL Provider's enrolment form where it requests a CSR (Certificate Signing Request).
12. Click Up Level to return to the Domain Administration page.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
To generate a certificate signing request (CSR) follow these steps:
2. Specify the certificate name.
3. The Bits selection allows you to choose the level of encryption of your SSL certificate. Select the appropriate number from the drop-down list.
4. Select a country from the drop-down list
5. Specify the state or province, location (city).
6. Enter the appropriate organization name and department/division in the field provided.
7. Enter the Domain Name for which you wish to generate the certificate-signing request.
8. Click the REQUEST button. A certificate-signing request will be generated and added to the repository. You will be able to add the other certificate parts later on.
NOTE: Do not lose your RSA Private Key, you will need this later.
Generating a CSR using an existing private key
In some cases you have a certificate in the repository, which has only the private key part and the other parts are missing due to some reasons. To generate a new Certificate Signing Request using the existing private key, follow these steps:
2. Click REQUEST.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
Follow these instructions to generate a CSR for your Web site. When you have completed this process, you will have a CSR ready to submit to your provider in order to be generated into a SSL Security Certificate.
2. Click on the domain name that you wish to generate the CSR for.
3. On the Certificate repository page click on the Add button.
4. Specify a certificate name.
5. Select the bit size from the drop-down list. 2048 is recommended.
6. Select a country from the drop-down list.
7. Specify the state or province, location (city).
8. Enter the appropriate organization name and department in the field provided.
9. Enter the Domain Name for which you wish to generate the certificate signing request.
10. Click the Request button. A certificate signing request will be generated and added to the repository. When you return to the Certificates page from the list at the bottom of the page, click on the certificate name that you just created. Copy the content of this box labelled 'CSR'. It should look similar to the example below:
11. Your CSR will now have been created. Copy and paste the contents into your SSL Provider's online enrolment form when requested.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
To access the Domain certificates repository page, click the Certificates icon at the Domain administration page. The certificates repository page will open displaying the list of available certificates:
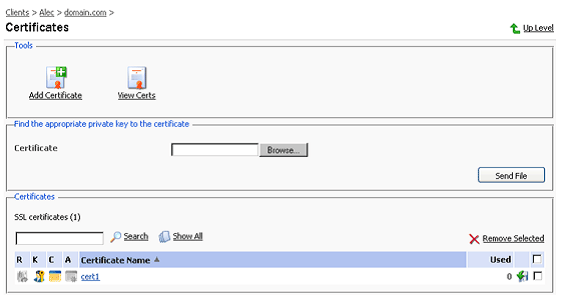
The four icons, preceding the certificate name in the list, indicate the present parts of a certificate. The icon displayed in the R column indicates that the Certificate Signing request part is present in the certificate, the icon in the K column indicates that the private key is contained within the certificate, the icon in the C column indicates that the SSL certificate text part is present and the icon in the A column indicates that CA [9] certificate part is present. The number in the Used column indicates the number of IP addresses the certificate is assigned to.
To add a certificate to the

repository, click the Add Certificate icon at the Domain certificate repository page. The SSL certificate creation page will open. On this page you can generate a self-signed certificate, certificate-signing request, purchase a SSL certificate, and add the certificate parts to an existing certificate.
NOTE: When acquiring or generating new certificates, make sure that the values you enter into the fields 'domain name', 'email address', 'state or province', 'location', 'organization name', and 'department name' do not exceed the limit of 64 symbols.
To generate a certificate signing request (CSR) follow these steps:
2. The Bits selection allows you to choose the level of encryption of your SSL certificate. Select the appropriate number from the drop-down list.
3. Select a country from the drop-down list.
4. Specify the state or province, location (city).
5. Enter the appropriate organization name and department/division in the field provided.
6. Enter the Domain Name for which you wish to generate the certificate signing request.
7. Specify the E-mail address.
8. Click the Request button. A certificate-signing request will be generated and added to the repository. You will be able to add the other certificate parts later on.
A situation may occur in some cases, that you have a certificate in the repository, which has only the private key part and the other parts are missing due to some reasons. To generate a new Certificate Signing Request using the existing private key, follow these steps:
2. Click Request.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
You must submit your request in a particular format called a Certificate Signature Request (CSR). WebLogic Server includes a Certificate Request Generator servlet that creates a CSR. The Certificate Request Generator servlet collects information from you and generates a private key file and a certificate request file. You must then submit the CSR. Before you can use the Certificate Request Generator servlet, WebLogic Server must be installed and running.
Start the Certificate Request Generator servlet (certificate.war). The .war file is automatically installed when you start WebLogic Server. In a Web browser, enter the URL for the Certificate Request Generator servlet as follows:
https://hostname:port/Certificate [20]
Hostname is the DNS name of the machine running WebLogic Server. Port is the number of the port at which WebLogic Server listens for SSL connections.
For example, if WebLogic Server is running on a machine named 'server' and it is configured to listen for SSL communications at the default port 7002 to run the Certificate Request Generator servlet, you must enter the following URL in your Web browser:
https://server:7002/certificate [21]
The Certificate Request Generator servlet loads a form in your web browser. Complete the form displayed in your browser.
Click the Generate Request button. The Certificate Request Generator servlet displays messages informing you if any required fields are empty or if any fields contain invalid values. Click the Back button in your browser and correct any errors.
NOTE: Private Key Password if you do not specify a password, you will get an unencrypted RSA private key. If you specify a password, you will get a PKCS-8 encrypted private key. When using PKCS-8 encrypted private keys, you need to enable the Use Encrypted Keys field on the SSL tab of the Server window in the Administration Console.
When all fields have been accepted, the Certificate Request Generator servlet generates the following files in the start-up directory of your WebLogic Server: mydomain_com-key.der-The private key file. The name of this file should go into the Server Key File Name field on the SSL tab in the Administration Console. mydomain_com-request.dem-The certificate request file, in binary format. mydomain_com-request.pem-The CSR file that you submit... It contains the same data as the .dem file but is encoded in ASCII so that you can copy it into email or paste it into a Web form.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
A CSR is a file containing your certificate application information, including your Public Key. Generate your CSR and then copy and paste the CSR file into the web form in the enrollment process.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
1. From WS_FTP Server, in the left pane, expand the FTP host and select SSL. The SSL Host Options appear in the right pane.
2. Click Certificate Management, then select the Certificate Creation tab.
3. Enter a name in the Certificate Set Name box. This will be the name of the certificate that is generated by WS_FTP Server.
4. Click the Browse (...) button in the Output Location box to select the folder you want the certificate created in.
5. Enter information in all of the Certificate Information boxes:
6. After all of the boxes are filled in correctly click Create to generate the keys, certificate, and certificate-signing request. If all of the boxes are not filled in, you cannot create the certificate.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]

When you are emailed your Digi-SSL™ certificate, two other certificates will also be attached to the email. Should they be required, you may download these certificates individually or collectively as a bundled file below:
(needed for Apache & Plesk Administrator installations)
(needed for Apache & Plesk Administrator installations)
NOTE: You must install both the bundle CA [9] certificate and your server certificate to provide secure access to your Web server.
On start-up, Stronghold loads CA certificates from the file specified by the SSLCACertificateFile entry in its 'httpd.conf' file.
You will receive an email from Digi-Sign with the certificate in the email (yourdomainname.cer). When viewed in a text editor, your certificate will look something like:
Copy your Certificate into the directory that you will be using to hold your certificates. In this example we will use /etc/ssl/crt/. Both the public and private key files will already be in this directory. The private key used in the example will be labelled private.key and the public key will be yourdomainname.cer.
It is recommended that you make the directory that contains the private key file only readable by root.
Login to the Administrator console and select the site that the certificate was requested for.
Select Services, then Actions next to Apache Web Server and then SSL Settings. There should already be a 'Self Signed' certificate saved.

Select 'Import' and copy the text from the yourdomainname.cer file into the box
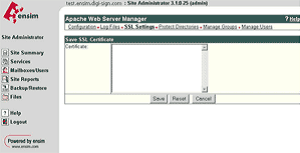
Select 'Save', the status should now change to successful.
Logout, do not select delete as this will delete the installed certificate.
You will need to install the Intermediate and Root certificates in order for browsers to trust your certificate. As well as your SSL certificate ( yourdomainname.cer) two other certificates, named UTN-USERFirst-Hardware.crt and Digi-SignCADigi-SSLXp.crt or
Digi-SignCADigi-SSLXs.crt, are also attached to the email from Digi-Sign. Apache users will not require these certificates. Instead you can install the intermediate certificates using a 'bundle' method.
In the Virtual Host settings for your site, in the virtual site file, you will need to add the following SSL directives. This may be achieved by:
2. Add the following line to the virtual host file under the virtual host domain for your site (assuming /etc/httpd/conf is the directory mentioned in 1.), if the line already exists amend it to read the following:
SSLCACertificateFile /etc/httpd/conf/ca-bundle/ca_new.txt
If you are using a different location and certificate file names you will need to change the path and filename to reflect this.
The SSL section of the updated virtual host file should now read similar to this example (depending on your naming and directories used):
Save your virtual host file and restart Apache.
You are now all set to start using your Digi-Sign certificate with your Apache Ensim configuration.
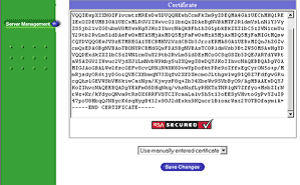
Go to the Server Management screen.
Click the green icon (Wrench for RaQ4, Pencil for XTR) next to the SSL enabled virtual site
Click SSL Settings on the left side.
Copy the entire contents of the site certificate that you received, including
-----BEGIN CERTIFICATE-----
and
-----END CERTIFICATE-----
Paste the new certificate information that you copied into the "Certificate" window.
Select Use manually entered certificate from the pull-down menu at the bottom.
Click Save Changes.
You will need to install the Intermediate and Root certificates in order for browsers to trust your certificate. As well as your site certificate (yourdomainname.cer) two other certificates, named UTN-USERFirst-Hardware.crt and Digi-SignCADigi-SSLXp.crt or
Digi-SignCADigi-SSLXs.crt,, are also attached to the email from Digi-Sign. Cobalt users will not require these certificates. Instead you can install the intermediate certificates using a 'bundle' method.
Download a Bundled cert file
The following will require that you access the httpd config file. This may be achieved by telnetting into your webserver.
In the Global SSL settings, in the httpd.conf file, you will need to add the following SSL directive.
This may be achieved by:
Copying the bundle file to the same directory as httpd.conf (this contains all of the ca certificates in the Digi-Sign chain).
Add the following line to httpd.conf, if the line already exists amend it to read the following:
SSLCACertificateFile /etc/httpd/conf/ca-bundle/ca_new.txt
NOTE: If you are using a different location and certificate file names you will need to change the path and filename to reflect your server.
1. After you receive your SSL certificate, firstly visit our web site download site file and the bundle file (rootchain) certificates to a secure location.
2. Click SSL on your control panel home page.
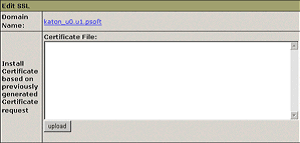
3. Go to the Web Service page and click the Edit icon in the SSL field.
4. In the form that opens, enter the SSL certificate into the box Install Certificate based on previously generated Certificate request and click Upload:
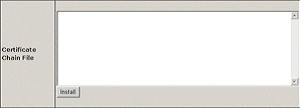
5. Enter the rootchain (bundle) certificate into the box Certificate Chain File and click Install:
6. Now you can use the SSL certificate.
IKEYMAN for Certificate Installation
Digi-Sign sends more than one certificate. In addition to the certificate for your server Digi-Sign send an Intermediate CA Certificate (the Digi-Sign certificate) and a Root CA Certificate (UTN-USERFirst-Hardware). Before installing the server certificate, install both of these certificates. Follow the instructions in 'Storing a CA certificate'.
NOTE:If the authority who issues the certificate is not a trusted CA in the key database, you must first store the CA certificate and designate the CA as a trusted CA. Then you can receive your CA-signed certificate into the database. You cannot receive a CA-signed certificate from a CA who is not a trusted CA. For instructions see 'Storing a CA certificate'
Storing a CA Certificate:
To receive the CA-signed certificate into a key database:
Requires the certificates to be merged into the Key Ring file. This process must be completed for all three certificates provided.
For additional information, refer to your server documentation.
Please note: To meet the most recent security standards [29], we strongly advise to update all servers running MS IIS 4.x with the most recent Service Packs for Windows NT 4.
We also advise to perform an upgrade on the server, of the MS Internet Explorer to at least version 5.5 Service Pack 2.
You will have received 3 Certificates from Digi-Sign. Save these Certificates to the desktop of the web server machine, then:
Important: You must now restart the computer or the IISAdmin Service to complete the installation
You may want to test the Web site to ensure that everything is working correctly. Be sure to use https:// when you test connectivity to the site
Follow these instructions to install your SSL server certificate:
Important: You must now restart the computer or the IISAdmin Service to complete the installation
You may want to test the Web site to ensure that everything is working correctly. Be sure to use https:// when you test connectivity to the site
You must first export the SSL certificate of the IIS 4.x / IIS 5.x / IIS 6.x Web site with the associated Private Key. If you do not have this key, ISA server will not allow you to use this certificate for SSL:
NOTE: If you do not have the option to export the Private key then the private key has already been exported to another computer or the key never existed on this computer. You cannot use this certificate on ISA Server. You must request a new certificate for this site for ISA Server.
NOTE: Ensure that you keep the file safe the SSL protocol depends upon this file.
Copy the file that you created to ISA Server.
On the ISA Server, open the MMC:
Now you will need to import the root and intermediate certificates.
On the Microsoft ISA Server:
To install the UTN-USERFirst-Hardware.crt Certificate:
To install the Digi-SignCADigi-SSLXp.crt or Digi-SignCADigi-SSLXs.crt:
Important: You must now restart the computer to complete the install.
Under the Personal folder, when a subfolder called 'Certificates' is displayed, click "Certificates" and verify that there is a certificate with the name of the Web computer.
Right-click the certificate and then click Properties.
If the 'Intended Purposes' field of the certificate is set to 'All' rather than a list of specific purposes, the following steps must be followed before ISA Server can recognize the certificate:
In the Certificate Services snap-in, open the Properties dialog box of the relevant certificate. Change the Enable all purposes for this certificate option to the Enable only the following purposes option, select all of the items, and then click Apply.
Open the ISA Manager and complete the SSL install:
Restart ISA Server.
You will have received 3 Certificates from Digi-Sign. Save these Certificates to the desktop of the webserver machine, then:
Important: You must now restart the computer or the IISAdmin Service to complete the installation
When you receive your certificates from Digi-Sign there will be your site certificate (named yourdomain.cer) plus 2 others (UTN-USERFirst-Hardware.crt and
Digi-SignCADigi-SSLXp.crt or Digi-SignCADigi-SSLXs.crt), these 2 must be installed as a Trusted Certificate Authority [9] CA and Certificate Chain.
*** Install the SSL Certificate ***
On Ironport's operating system, Async 5.5, you can't install the SSL certificate via the GUI. You must login to the command line (CLI). You can SSH into the CLI and type the following command sequence:
ironport> certconfig
[]> setup
ironport output: paste cert in PEM format (end with '.'):
Copy and paste the .crt/.cer file, including the "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----" lines. If you're using windows, you may need to open this file with wordpad/notepad.
ironport output: paste key in PEM format (end with '.'):
Copy and paste the server.key.PEMunsecure file.
If you received an intermediate CA certificate, you need to perform an additional step:
ironport output: Do you want to add an intermediate certificate? [N]> Y
Copy and paste the contents of the intermediate CA certificate file here.
ironport>commit
When you receive your certificates from Digi-Sign there will be your site certificate (named yourdomain.cer) plus 2 others (UTN-USERFirst-Hardware.crt and
Digi-SignCADigi-SSLXp.crt or Digi-SignCADigi-SSLXs.crt), these 2 must be installed as a Trusted Certificate Authority [9] CA and Certificate Chain.
1. Select the Install Certificate link on the left side of the page.
2. Select the Security Tab.
3. On the left frame, choose the Install Certificate link.
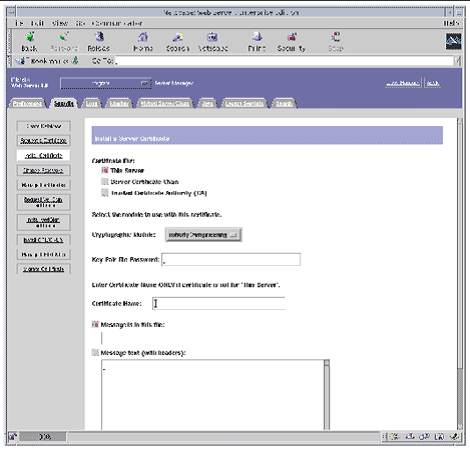
Select Trusted Certificate Authority CA, enter the password and copy the text from the
UTN-USERFirst-Hardware to the Message Text box (including the BEGIN and END lines), then click 'OK'.
Accept the certificate.
NOTE:: Do not shutdown or restart the server until all steps have been completed.
Repeat the steps from above using the text from the Digi-Sign CA Digi-SSL Xs™ or
Digi-Sign CA Digi-SSL Xp™and choosing the 'Certificate Chain' option.
4. Fill out the form to install your certificate:
5. Choose Message text (with headers) and paste the text you copied from your certificate file: your_domain.cer
6. Click the OK button at the bottom of the page.
7. If everything looks correct, click the Add Server Certificate button.
1. Click the Preferences tab near the top of the page.
2. Select the Edit Listen Sockets link on the left frame.
a. Alter the following fields:
b. Click the OK button to apply these changes.
In the security field of the Edit Listen Sockets page, there should now be an Attributes link.
3. Click the Attributes link.
4. Enter the user@realm-name password to authenticate to the user@realm-name on the system.
5. Select SSL settings from the pop-up window.
6. Select the certificate for the user@realm-name followed by: Server-Cert (or the name you chose if it is different).
7. When you have chosen a certificate and confirmed all the security settings, click the OK button.
8. Click the Apply link in the far upper right corner to apply these changes before you start your server.
9. Click the Load Configuration Files link to apply the changes.
If you click the Apply Changes button when the server is off, a pop-up window prompts you for a password. This window is not resizable, and you might have problem submitting the change.
There are two workarounds for the problem noted above:
10. Provide the requested passwords in the dialog boxes to start the server.
11. At the Module user@realm-name prompt, enter the password you set when you created user in the realm-name using secadm.
12. Verify the new SSL-enabled web server at the following URL:
Note that the default server_port is 443.
When you receive your Digi-SSL™ [5] certificate back from Digi-Sign, it will be encrypted with your public key so that only you can decrypt it. Only by entering the correct password for your trust database, can you decrypt and install your certificate.
There are three types of certificates:
A certificate chain is a hierarchical series of certificates signed by successive certificate authorities. A CA certificate identifies a certificate authority (CA) and is used to sign certificates issued by that authority. A CA certificate can in turn be signed by the CA certificate of a parent CA, and so on, up to a Root CA.
The server will use the key-pair file password you specify to decrypt the certificate when you install it. You can either save the certificates somewhere accessible to the server, or copy them in a text format and be ready to paste them into the Install Certificate form, as described here.
Installing a Certificate
To install a certificate, perform the following steps:
1. Access either the Administration Server or the Server Manager and choose the Security tab.
2. Click the Install Certificate link.
3. Check the type of certificate you are installing:
4. Select the Cryptographic Module from the drop-down list.
5. Enter the Key-Pair File Password.
6. Leave the a name for the certificate field blank if it is to be the only one used for this server instance, unless:
7. Select either:
8. Click OK.
9. Select either:
10. Repeat steps from point 2 to 9 for each individual certificate you received from Digi-Sign and ensure you select the correct certificate type, that you are installing. We recommend, that you install certificates in the following order:
11. For the Server Manager, click Apply, and then Restart for changes to take effect.
Important: Installation is a two-step process - ensure you follow both steps listed below:
Important: Installation is a two-step process - ensure you follow both steps listed below.
If you have already obtained a certificate containing private key and certificate part (and may be CA certificate), follow these steps to upload it:
You can upload an existing certificate in two ways:
Uploading a CA certificate
For the Digi-Sign CA [9] Digi-SSL Xs or Digi-Sign CA Digi-SSL Xp is the CA Certificate, or rootchain certificate. The CA Certificate is used to appropriately identify and authenticate the certificate authority, which has issued your SSL certificate. To upload your CA Certificate, follow these steps:
NOTE: When you add a certificate, it is not installed automatically onto the domain or assigned to an IP address, but only added to the Certificate repository. You can assign a certificate to an IP address at the Client's IP pool
9. Click the 'Send Text' button.
10. Now click 'Up Level' from the top right of the screen and choose 'Setup'.
11. At the top of the page, change the 'SSL Certificate' drop-down menu to the certificate you have just installed.
12. Click the 'Server' item from the left hand menu.
13. Click on the 'Service Management' menu item.
14. You now need to Stop and Start the Apache process.
NOTE: Restarting Apache will NOT work. You must stop the service, then start it again to complete the installation
When you receive your certificates you need to store them in the mydomain directory.
NOTE: If you obtain a private key file from a source other than the Certificate Request Generator servlet, verify that the private key file is in PKCS#5/PKCS#8 PEM format.
To use a certificate chain, append the additional PEM-encoded digital certificates to the digital certificate that issued for the WebLogic Server (the intermediate CA certificate). The last digital certificate in the file chain will be the Root certificate that is self-signed. (example below:)
MIIB+jCCAWMCAgGjMA0GCSqGSIb3DQEBBAUAMEUxCzAJBgNVBAYTAlVTMRgwFgYD
.....(your Intermediate CA certificate).....
bW1EDp3zdHSo1TRJ6V6e6bR64eVaH4QwnNOfpSXY
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIE0DCCA7igAwIBAgIQMKeebbHpGVqxyFDTln1j1TANBgkqhkiG9w0BAQUFADBv
.....(your Root CA certificate).....
WjEZgqr9NaoNZCZpyfZxPsOFYzoxLYEmJs3AJHxkhIHg6YQU
-----END CERTIFICATE-----
Configure WebLogic Server to use the SSL protocol; you need to enter the following information on the SSL tab in the Server Configuration window:
Once you have a private key and digital certificate, copy the private key file generated by the Certificate Request Generator servlet and the digital certificate you received into the mydomain directory. Private Key files and digital certificates are generated in either PEM or Definite Encoding Rules (DER) format. The filename extension identifies the format of the digital certificate file. A PEM (.pem) format private key file begins and ends with the following lines, respectively:
NOTE: Typically, the digital certificate file for a WebLogic Server is in one file, with either a .pem or .der extension, and the WebLogic Server certificate chain is in another file. Two files are used because different WebLogic Servers may share the same certificate chain.
The first digital certificate in the certificate authority file is the first digital certificate in the WebLogic Server's certificate chain. The next certificates in the file are the next digital certificates in the certificate chain. The last certificate in the file is a self-signed digital certificate that ends the certificate chain. A DER (.der) format file contains binary data. WebLogic Server requires that the file extension match the contents of the certificate file.
NOTE: If you are creating a file with the digital certificates of multiple certificate authorities or a file that contains a certificate chain, you must use PEM format. WebLogic Server provides a tool for converting DER format files to PEM format, and visa versa.
When your certificate is issued you will receive 4 certificates:
Yourdomain.cer
Digi-SignCADigi-SSLXp.crt or Digi-SignCADigi-SSLXs.crt
UTN-USERFirst-Hardware.crt
When you have chosen your cipher settings, click Save again to send the information to the server.
When you receive your certificates there will be 3 files, open a text editor and then copy the text from each certificate into the text editor to form one file. The certificates should be pasted in the following sequence, your site Certificate named yourdomain.cer, Digi-SignCADigi-SSLXp.crt or Digi-SignCADigi-SSLXs.crt , UTN-USERFirst-Hardware.crt, and the resulting file should look like the following:
-----BEGIN CERTIFICATE-----
(Class3CertificateAthority Encoded Text)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(TrustRootCertificateAuthority Encoded Text)
-----END CERTIFICATE-----
Please note: Make sure you include the -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- as displayed above.
1. Login to the web server.
2. Select SSL certificates
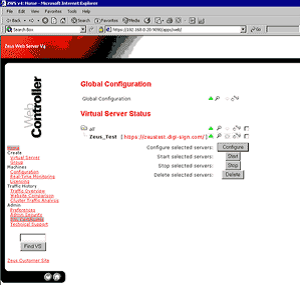
3. Select Generate CSR [32] (or Replace Certificate) against the certificate set
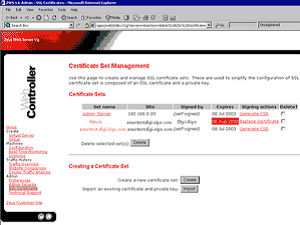
4. Copy/Paste the text from the text editor into the Signed Certificate box and click OK.
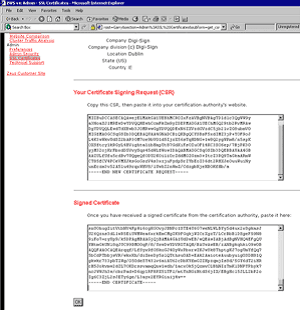
5. Then select Accept this Certificate
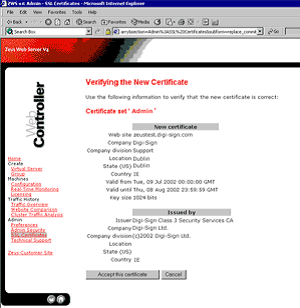
6. The certificate set now needs assigning to the web site. Click on the Home icon. Put a tick in the box next to the virtual server to configure and select configure.
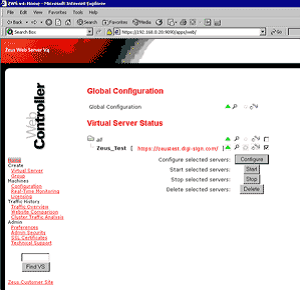
7. Click on SSL Enabled.
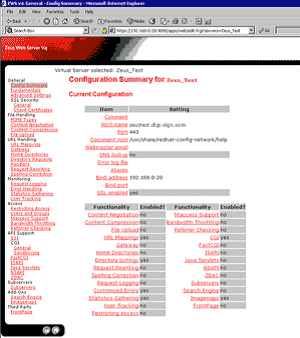
8. Enable SSL and select the certificate set to use.
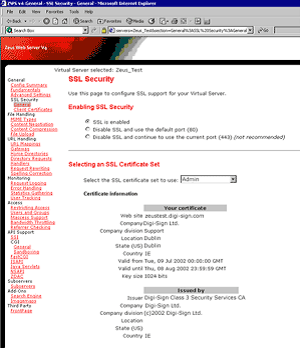
9. Apply and commit the changes then restart the web server.
The following are frequently asked questions on the most popular web servers that use Digi-SSL™ Secure Soctket Layer [SSL] security.
No, Apache users should use the bundle file on the support page instead of the Digi-Sign and GTE certificate:
http://www.digi-sign.com/support/digi-ssl/install+certificate/index [33]
If you do not install the bundle file you will receive not trusted messages when you go to the secure area of your web site.
First check your backups and see if you can re-install the Private Key. If you don't know how to re-install the key from your backups, then contact your systems administrator. Failing that, contact your server software vendor for technical support. The only alternative course of action available is a re-issuance of the certificate following the re-submitting of a replacement CSR.
There may not be a corresponding Private Key or the key that is found is not the one that matches the certificates.
You may also see this error: "OpenSSL: error:0B080074:x509 certificate
outines:x509_check_private_key:key values mismatch"
Name based hosting is rarely used in production environments. IP based hosting should be used due to the way that the SSL protocol works.
There is no difference, the process is the same and the directives used are the same. Apache fails on start up, what could cause this?
If the key file has a Passphrase you need to remove it, as Apache cannot read this on start-up, you can do that with the following command: openssl rsa -in file1.key -out file2.key
file2.key will contain your unencrypted key If you used Mozilla to download the file, it may have saved the file in compressed format.
The certificate is not bound to any specific IP address. It is bound to the fully qualified domain name such as www.digi-sign.com [8].
Is the SSL port opened, this is usually port 443. (listen 443) Is the firewall set to allow the SSL port through. Has the server been rebooted Make sure 'Use SSL 3.0' is ticked in the web browser options.
This is usually caused by the directive SSLCertificateChainFile being used instead of the SSLCACertificateFile directive.
This error message occurs because there are directives missing from the httpd.conf file. Most web servers can be configured to 'talk' to various browser versions in a different way, the fix for this particular problem is to add the following directives to the httpd.conf file so allowances can be made for Internet Explorer on the Mac:
SSLSessionCache dbm:/var/cache/httpd/ssl_cache
SSLSessionCacheTimeout 300.
The error means that there are embedded objects or HTML tags on the page that are not being called absolutely secure. For example, a page that is loaded securely (HTTPS), and contains an image tag within the source code such as IMG SRC =http://www.yyy.com/image.gif. In this case the image is being called absolutely using the non-secure (HTTP) protocol.
This problem occurs if you assign the same IP address to each host in your config file. SSL does not support name based virtual hosting (host headers are encrypted in SSL), so only the first certificate listed in your config file will be used.
The Root Certificates and/or Intermediate Certificates may not be installed correctly. This can be checked by clicking on 'View Certificates' when you get the error message and seeing if all three certificates are visible.
It may also be that the certificate being used is not for the Fully Qualified Domain Name, check again using 'View Certificates' to see if the domain name on the certificate matches the domain name in the URL that you are going to.
Check your 'Internet Options' and make sure that 'Use SSL 3.0' is ticked in the 'Advanced' section. Check your .conf file to ensure that SSL Protocol version 3 is allowed.
If the web server is set to check the Certificate Revocation List and the server is down, this can cause a time-out of the operation. This will not be the certificates, but something related to the browser timing out on the operation.
When I connect via HTTPS to an Apache with Mod_SSL or OpenSSL server with Microsoft Internet Explorer (MSIE) I get various I/O errors. What is the reason?
The first reason is that the SSL implementation in some MSIE versions has some subtle bugs related to the HTTP keep-alive facility and the SSL close notify alerts on socket connection close. Additionally the interaction between SSL and HTTP/1.1 features are problematic with some MSIE versions, too. You've to work-around these problems by forcing Apache with Mod_SSL or OpenSSL to not use HTTP/1.1, keep-alive connections or sending the SSL close notify messages to MSIE clients. This can be done by using the following directive in your SSL-aware virtual host section:
SetEnvIf User-Agent ".*MSIE.*" nokeepalive ssl-unclean-shutdown downgrade-1.0 force-response-1.0
Additionally it is known some MSIE versions also have problems with particular ciphers. Unfortunately you cannot workaround these bugs only for those MSIE particular clients, because the ciphers are already used in the SSL handshake phase. So a MSIE-specific SetEnvIf doesn't work to solve these problems.
Instead you have to do more drastic adjustments to the global parameters. But before you decide to do this, make sure your clients really have problems. If not, do not do this, because it affects ALL of your clients.
Apache-SSL uses a toolkit called OpenSSL for its security routines. OpenSSL is very particular about the format of certificate requests and certificates. This error is specifically related to the format of the certificate.
Check that there are 5 dashes before and after the BEGIN and END text, and they must form the first and last lines of the certificate.
In particular, the BEGIN and END lines must look like:
-----BEGIN CERTIFICATE-----
Encoded Certificate
-----END CERTIFICATE-----
Be careful when you cut and pasted the certificate from the browser window into a text editor to create the certificate text file.
Make sure you remove any trailing spaces, before and after the BEGIN or END lines, or you will see this error.
Specify the correct private key for the certificate.
Compare the modulus of certificate against the modulus of the private key to see if they match by using the following commands:
To view the certificate modulus:
Openssl x509 -noout -text -in certfile –modulus
To view the key:
Openssl rsa -noout -text -in keyfile –modulus
Check that the certificate and private key is saved in notepad and that it has no trailing spaces.
The "modulus" and "public exponent" portions in the key and the certificate must match exactly
This error message occurs if you are using the incorrect certificate or private key during installation. So you need to use the matching key and certificate files. To check that the public key in your cert matches the public portion of your private key, view both files, and compare the modulus values with the following instructions:
To view the certificate:
Openssl x509 -noout -text -in certfile
To view the key:
Openssl rsa -noout -text -in keyfile
The "modulus" and "public exponent" portions in the key and the certificate must match exactly. If the "modulus" do not match exactly then you are using either the incorrect private key or certificate.
Yes, if you do not install all the received certificates you will receive not trusted messages when you go to the secure area of your web site.
First check your backups and see if you can re-install the "pending request" or "private key". If you don't know how to re-install the key from your backups, then contact your systems administrator. Failing that, contact your server software vendor for technical support. The only alternative course of action available is a re-issuance of the certificate following the re-submitting of a replacement CSR.
There may not be a corresponding 'private key' or 'pending request' or the key that is found is not the one that matches the certificates.
Name based hosting is rarely used in production environments. IP based hosting should be used due to the way that the SSL protocol works.
Is the SSL port opened, this is usually port 443.
Is the firewall set to allow the SSL port through?
Has the server been rebooted?
Make sure 'Use SSL 3.0' is ticked in the web browser options.
The error means that there are embedded objects or HTML tags on the page that are not being called absolutely secure. For example, a page that is loaded securely (HTTPS), and contains an image tag within the source code such as IMG SRC =http://www.yyy.com/image.gif. In this case the image is being called absolutely using the non-secure (HTTP) protocol.
The certificate is not bound to any specific IP address. It is bound to the fully qualified domain name such as www.digi-sign.com [8].
This problem occurs if you assign the same IP address to each host in your config file. SSL does not support name based virtual hosting (host headers are encrypted in SSL), so only the first certificate listed in your config file will be sent.
The Root Certificates and/or Intermediate Certificates may not be installed correctly. This can be checked by clicking on 'View Certificates' when you get the error message and seeing if all three certificates are visible.
It may also be that the certificate being used is not for the Fully Qualified Domain Name, check again using 'View Certificates' to see if the domain name on the certificate matches the domain name in the URL that you are going to.
Check your 'Internet Options' and make sure that 'Use SSL 3.0' is ticked in the 'Advanced' section.
Microsoft IIS is configured to require a secure channel.
The following steps will allow non-secure (http) connections to your site:
Within Microsoft Internet Information Server, right click on your web site.
Under Secure Communications, click on Edit.
Un-check the box that says 'Require Secure Channel'
If the web server is set to check the Certificate Revocation List and the server is down, this can cause a time-out of the operation.
This will not be the certificate, but something related to the browser timing out on the operation.
Start, run, type mmc
Go into the Console Tab, Add/Remove Snap in
Click on Add, Double Click on Certificates and Click on Add > OK
Choose Computer Account
Choose Local Computer
Open up the Certificates Consol Tree
Look for a folder labelled REQUEST, then select Certificates
Highlight the key that you wish to back up
Right click on the file and choose, All Tasks, Export
Follow the Certificate Export Wizard
Choose to mark the Private key as exportable
Leave default settings
Choose to save file on a set location.
Click Finish
You will get message that the export was successful
Note: Once the Pending Request is completed the Key is no longer available
Start the certificates mmc for the web server and select 'All Tasks', 'Export' against the site certificate. Do not choose to export the CA certificates. Specify a password. Specify a filename (e.g. mypkcs12.pfx). Copy the resulting .pfx file to your Apache web server.
Then import the private key and cert file into Apache using the following commands:
openssl pkcs12 -in mypkcs12.pfx -out pfxoutput.txt
You'll need to enter the password at least once.
Load pfxoutput.txt into a text editor and save each certificate as a separate file.
Also save the private key as a separate file (e.g. myencrypted.key).
The private key will probably be encrypted at the moment. i.e. looking something like.....
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,.........
.........
-----END RSA PRIVATE KEY-----
If the version of Apache we're using doesn't allow encrypted private keys, to decrypt the private key run the following command:
Openssl rsa -in myencrypted.key -out my.key
To use ASP to force SSL for specific pages follow the directions at the following url:
http://support.microsoft.com/default.aspx?scid=kb;EN-US;q239875 [34]
Please refer to the following URL on Microsoft's Knowledgebase: http://support.microsoft.com/support/kb/articles/Q232/1/36.ASP [35]
Please refer to the following URL on Microsoft's Knowledgebase: http://support.microsoft.com/support/kb/articles/Q232/1/37.ASP [36]
Create a new web site in IIS, then go to the 'Properties', 'Directory Security', 'Server Certificate' tab.
Use the certificate wizard to create your new Key/CSR file
Backup the private key file by following the instructions:
Start, run, type mmc, select OK
Go into the Console Tab, Add/Remove Snap in
Click on "Add". Double Click on "Certificates" and Click on "Add", click "OK"
Choose Computer Account, then Local Computer
Open up the Certificates Consol Tree
Look for a folder called REQUEST, Certificates
Highlight the key that you wish to back up
Right click on the file and choose, All Tasks, Export
Follow the Certificate Export Wizard
Choose to mark the Private key as exportable
Leave default settings
Choose to save file on a set location.
It is important to take a copy of the private key and store it off the server; in the event
that the server crashes.
Click Finish
You will get message that the export was successful
Save the resultant CSR file to your hard drive indicating it is a renewal CSR
Use this CSR during the purchase process.
Once you receive the renewed certificate, install it using the wizard you used to create it
on the same NEW website you created.
Once installed, go to the correct website you want the certificate to run on.
Go to 'Properties', 'Directory Security', 'Server Certificate', remove the certificate currently installed, and assign the certificate you installed in the previous step
Restart the WWW service
To avoid this error, create a new certificate and verify that there are no special characters in any of the fields in the distinguished name.
In particular, do not include a comma in the company name.
The following characters are not allowed in any of the CSR fields:
[! @ # $ % ^ * ( ) ~ ? > < & / \ , . " ']
You are attempting to install a certificate that does not match the private key (Pending request) that is currently residing in the Certificate Wizard. Microsoft IIS 5 only allows you to make one request per site. If you create a new CSR for the same website, your original request (and private key) will be overwritten.
If you have a backup of the private key, you can install the certificate via the MMC if you can restore the request to the REQUEST folder.
Unless you can find the matching private key for the certificate, you will need to have the certificates reissued.
Microsoft has released a fix for this error. Please refer to the relevant knowledge base article Q285821, which can be found at the following url:
http://support.microsoft.com/default.aspx?scid=kb;EN-US;q285821 [37]
Start the certificates mmc for the web server and select 'All Tasks', 'Export' against the site certificate. Choose to export the CA certificates. Specify a password. Specify a filename (e.g. mypkcs12.pfx). Save the .pfx file in a safe place off the server.
First check your backups and see if you can re-install the Private Key. If you don't know how to re-install the key from your backups, then contact your systems administrator. Failing that, contact your server software vendor for technical support. The only alternative course of action available is a re-issuance of the certificate following the re-submitting of a replacement CSR.
There may not be a corresponding Private Key or the key that is found is not the one that matches the certificates.
You may also see this error: "OpenSSL: error:0B080074:x509 certificate outines:x509_check_private_key:key values mismatch"
Name based hosting is rarely used in production environments.
IP based hosting should be used due to the way that the SSL protocol works.
If the key file has a pass phrase you need to remove it, as Apache cannot read this on start-up, you can do that with the following command:
Openssl rsa -in file1.key -out file2.key
File2.key will contain your unencrypted key
If you used Mozilla to download the file, it may have saved the file in compressed format
I get 'The Page Cannot Be Displayed' when going to the HTTPS page
Is the SSL port opened, this is usually port 443. (Listen 443)?
Is the firewall set to allow the SSL port through?
Has the server been rebooted?
Make sure 'Use SSL 3.0' is ticked in the web browser options.
This error message occurs because there are directives missing from the httpd.conf file. Most web servers can be configured to 'talk' to various browser versions in a different way, the fix for this particular problem is to add the following directives to the httpd.conf file so allowances can be made for Internet Explorer on the Mac:
SSLSessionCache dbm:/var/cache/httpd/ssl_cache
SSLSessionCacheTimeout 300.
The error means that there are embedded objects or HTML tags on the page that are not being called absolutely secure. For example, a page that is loaded securely (HTTPS), and contains an image tag within the source code such as IMG SRC =http://www.yyy.com/image.gif. In this case the image is being called absolutely using the non-secure (HTTP) protocol.
The certificate is not bound to any specific IP address. It is bound to the fully qualified domain name such as www.digi-sign.com [8].
This problem occurs if you assign the same IP address to each host in your config file. SSL does not support name based virtual hosting (host headers are encrypted in SSL), so only the first certificate listed in your config file will be sent.
The Root Certificates and/or Intermediate Certificates may not be installed correctly. This can be checked by clicking on 'View Certificates' when you get the error message and seeing if all three certificates are visible.
It may also be that the certificate being used is not for the Fully Qualified Domain Name, check again using 'View Certificates' to see if the domain name on the certificate matches the domain name in the URL that you are going to.
Check your 'Internet Options' and make sure that 'Use SSL 3.0' is ticked in the 'Advanced' section.
Also ensure that SSL Protocol version 3 is supported.
The bundle file must also be specified in the Global SSL section of the. conf file.
If the web server is set to check the Certificate Revocation List and the server is down, this can cause a time-out of the operation.
This will not be the certificate, but something related to the browser timing out on the operation.
The first reason is that the SSL implementation in some MSIE versions has some subtle bugs related to the HTTP keep-alive facility and the SSL close notify alerts on socket connection close. Additionally the interaction between SSL and HTTP/1.1 features are problematic with some MSIE versions, too. You've to work-around these problems by forcing Apache with Mod_SSL or OpenSSL to not use HTTP/1.1, keep-alive connections or sending the SSL close notify messages to MSIE clients. This can be done by using the following directive in your SSL virtual host section:
Open the file with any text editor and carefully insert the code piece below in the appropriate place, around the directive for "SSLengine on", you may have to insert it in both the IF and the ELSIF portions of the setup:
$PerlConfig .= "Listen $ip:443\n";
$PerlConfig .= "
# ------------- INSERT THIS CODE -------------
$PerlConfig .= "SetEnvIf User-Agent \".*MSIE.*\" \\n";
$PerlConfig .= " nokeepalive ssl-unclean-shutdown \\n";
$PerlConfig .= " downgrade-1.0 force-response-1.0 \n";
# ------------- END INSERT -------------------
$PerlConfig .= "SSLengine on\n";
$PerlConfig .= "SSLCertificateFile /home/sites/$group/certs/certificate\n";
$PerlConfig .= "SSLCertificateKeyFile /home/sites/$group/certs/key\n";
$PerlConfig .= join('', @ssl_conf);
Additionally it is known some MSIE versions have also problems with particular ciphers. Unfortunately one cannot workaround these bugs only for those MSIE particular clients, because the ciphers are already used in the SSL handshake phase. So a MSIE-specific SetEnvIf doesn't work to solve these problems. Instead one has to do more drastic adjustments to the global parameters. But before you decide to do this, make sure your clients really have problems. If not, do not do this, because it affects all (!) your clients, i.e., also your non-MSIE clients.
The certificates must be provided in a single chain file in Netscape format. Please request this from support@digi-sign.com [38]
The certificates must be provided in a single text file in this order:
The customer certificate
Digi-SignClass3CA.cer
GTECyberTrustRootCA.cer
And there MUST be a blank line between
-----END CERTIFICATE-----
and
-----BEGIN CERTIFICATE-----
This error happens when using the Certificate Extractor utility. If you do not use the extractor to import the certificate, it should work OK.
This error is a known bug in earlier versions of 4D Webstar Server Suite/SSL. You should upgrade to the latest version, and make sure all fixes and updates have been applied.
If you are using the latest version, check that your SSL settings are correct. The server should be listening on Port 443 for SSL connections, and have the correct certificate and key file specified. Enable all ciphers. If you have not set up your server correctly for SSL, you may receive this error.
Links:
[1] http://www2.digi-sign.com/about/announcements/2048
[2] http://www2.digi-sign.com/support/knowledgebase/digi-ssl
[3] http://www2.digi-sign.com/user/login
[4] http://www2.digi-sign.com/user/register
[5] http://www2.digi-sign.com/digi-ssl
[6] http://www2.digi-sign.com/en/node/add/forum/11
[7] http://www.sun.com/hardware/serverappliances/documentation/manuals.html
[8] http://www.digi-sign.com
[9] http://www2.digi-sign.com/certificate+authority
[10] http://www.company.com
[11] http://www2.digi-sign.com/support/digi-ssl/Microsoft+iis+5+iis+6
[12] http://www2.digi-sign.com/http
[13] http://www.digi-sign.com/product/digi-ssl/
[14] http://www2.digi-sign.com/digi-ca
[15] http://www.yourdomain.com
[16] http://www2.digi-sign.com/digital+certificate
[17] http://www.yoursitename.com
[18] mailto:sleuniss@yoursitename.com
[19] http://www.domainname.com
[20] https://hostname:port/Certificate
[21] https://server:7002/certificate
[22] https://www.digi-sign.com/downloads/download.php?id=aacd-digi-ssl-pdf
[23] http://www2.digi-sign.com/download/certificate/UTN-USERFirst-Hardware.crt
[24] http://www2.digi-sign.com/download/certificate/Digi-SignCADigi-SSLXs.crt
[25] http://www2.digi-sign.com/download/certificate/Digi-SSLXsCA_Chain.pem
[26] http://www2.digi-sign.com/download/certificate/Digi-SignCADigi-SSLXp.crt
[27] http://www2.digi-sign.com/download/certificate/Digi-SSLXpCA_Chain.pem
[28] http://www.digi-sign.com/support/digi-ssl/install%20certificate/index
[29] http://www2.digi-sign.com/compliance/introduction
[30] https://hostname.domain:
[31] https://myhost.yoursitename.com
[32] http://www2.digi-sign.com/support/digi-ssl/generate+csr
[33] http://www.digi-sign.com/support/digi-ssl/install+certificate/index
[34] http://support.microsoft.com/default.aspx?scid=kb;EN-US;q239875
[35] http://support.microsoft.com/support/kb/articles/Q232/1/36.ASP
[36] http://support.microsoft.com/support/kb/articles/Q232/1/37.ASP
[37] http://support.microsoft.com/default.aspx?scid=kb;EN-US;q285821
[38] mailto:support@digi-sign.com