


Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
The first part of enrolling for your Digi-SSL™ [2] Certificate is to generate a Certificate Signing Request [CSR]. CSR generation is wholly dependent on the software you use on your webserver. Select your webserver software from the list below after reading the following general points:
The Common Name field should be the Fully Qualified Domain Name [FQDN] or the web address for which you plan to use your Certificate, e.g. the area of your site you wish customers to connect to using SSL. For example, a Digi-SSL™ Certificate issued for digi-sign.com will not be valid for secure.digi-sign.com. If the web address to be used for SSL is secure.digi-sign.com, ensure that the common name submitted in the CSR is secure.digi-sign.com
If your webserver software does not appear on the list, please contact support [3] with full details of your webserver software and we will contact you with further instructions.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
A CSR is a file containing your certificate application information, including your Public Key. Generate your CSR and then copy and paste the CSR file into the web form in the enrollment process:
Generate keys and certificate:
To generate a pair of private key and public Certificate Signing Request (CSR) for a webserver, replace "server" below and "myserver" with the total hostname you are using in the following command:
This creates two files. The file myserver.key contains a private key; do not disclose this file to anyone. Carefully protect the private key.
In particular, be sure to backup the private key, as there is no means to recover it should it be lost. The private key is used as input in the command to generate a Certificate Signing Request (CSR).
You will now be asked to enter details to be entered into your CSR.
What you are about to enter is what is called a Distinguished Name or a DN.
For some fields there will be a default value, If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]: GB
State or Province Name (full name) [Some-State]: York
Locality Name (eg, city) []: York
Organization Name (eg, company) [Internet Widgits Pty Ltd]: MyCompany Ltd
Organizational Unit Name (eg, section) []: IT
Common Name (eg, YOUR name) []: mysubdomain.mydomain.com
Email Address []:
Please enter the following 'extra' attributes to be sent with your certificate request
A challenge password []:
An optional company name []:
-----
Use the name of the web server as Common Name (CN). If the domain name is mydomain.com append the domain to the hostname (use the fully qualified domain name).
The fields email address, optional company name and challenge password can be left blank for a web server certificate.
Your CSR will now have been created. Open the server.csr in a text editor and copy and paste the contents into the online enrollment form when requested.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
A CSR is a file containing your certificate application information, including your Public Key. Generate your CSR and then copy and paste the CSR file into the web form in the enrollment process:
Generate keys and certificate:
To generate a pair of private key and public Certificate Signing Request (CSR) for a web server, "server", use the following commands:
256-bit Certificate:
Openssl req -new -newkey rsa: 2048 -keyout myserver.key -nodes -out server.csr
This creates two files. The file myserver.key contains a private key; do not disclose this file to anyone. Carefully protect the private key.
In particular, be sure to backup the private key, as there is no means to recover it should it be lost. The private key is used as input in the command to generate a Certificate Signing Request (CSR).
You will now be asked to enter details to be entered into your CSR.
What you are about to enter is what is called a Distinguished Name or a DN.
For some fields there will be a default value, If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]: GB
State or Province Name (full name) [Some-State]: York
Locality Name (eg, city) []: York
Organization Name (eg, company) [Internet Widgits Pty Ltd]: MyCompany Ltd
Organizational Unit Name (eg, section) []: IT
Common Name (eg, YOUR name) []: mysubdomain.mydomain.com
Email Address []:
Please enter the following 'extra' attributes to be sent with your certificate request
A challenge password []:
An optional company name []:
-----
Use the name of the web server as Common Name (CN). If the domain name is mydomain.com append the domain to the hostname (use the fully qualified domain name).
The fields email address; optional company name and challenge password can be left blank for a webserver certificate.
Your CSR will now have been created. Open the server.csr in a text editor and copy and paste the contents into the online enrollment form when requested.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
To enable SSL on a virtual site:
Go to the Server Management screen.
Click the green icon (Wrench for RaQ4, Pencil for XTR) next to the virtual site on which you want to enable SSL. The Site Management screen appears.
Click Site Settings on the left side.
(Then 'General' for XTR)
Click the check box next to Enable SSL.
Click Save Changes.
The RaQ4/XTR saves the configuration of the virtual site.
Generate a self-signed certificate:
Once SSL is enabled, the user must now create a self-signed certificate. An external authority will sign the self-signed certificate later.
Go to the Server Management screen.
Click the green icon (Wrench for RaQ4, Pencil for XTR) next to the SSL enabled virtual site
Click SSL Settings on the left side.
The Certificate Subject Information table appears.
Enter the following information:
Country Enter the two-letter country code
State Enter the name of the state or County
Locality Enter the city or locality
Organization Enter the name of the organization
Organizational Unit As an option, enter the name of a department
Select Generate self-signed certificate from the pull-down menu at the bottom.
Click Save Changes.
The RaQ4/XTR processes the information and regenerates the screen with the new self-signed certificate in the Certificate Request and Certificate windows.
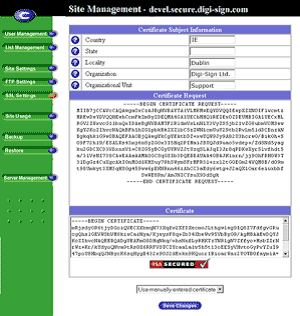
Copy the entire contents of the certificate request, including:
-----BEGIN CERTIFICATE REQUEST-----
and
-----END CERTIFICATE REQUEST-----
for use during the purchasing process.

Cobalt User Guide available at:
http://www.sun.com/hardware/serverappliances/documentation/manuals.html [4]

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
Login to the Site Administrator or Appliance Administrator and select the site to administer.
Select Services
Select the Actions box next to Apache Web Server and then select SSL Settings
Select Generate and fill in the required details, the site name will automatically be entered into the Common Name field, ensure this is correct and contains the Fully Qualified Domain Name (e.g. secure.digi-sign.com, www.digi-sign.com [5], support.digi-sign.net
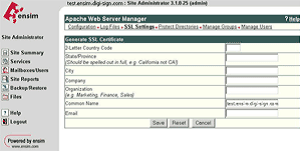
Select Save and you are presented with the RSA Key and the Certificate Request (CSR)
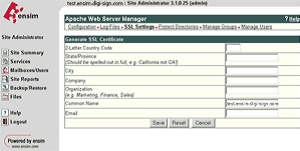
Copy the Certificate Request into a text editor; this will be required when you purchase your certificate. Do not delete this request, as it will be needed during the installation of your SSL certificate.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
NOTE: Keys and certificates are managed through three scripts: genkey, getca and genreq. These are part of the normal Stronghold distribution. Keys and certificates are stored in the directory$SSLTOP/private/, where SSLTOP is typically /usr/local/ssl.
To generate a key pair and CSR for your server:
Back up your key file and CSR on a floppy disk and store the disk in a secure location. If you lose your private key or forget the password, you will not be able to install your certificate.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
1. Click SSL on your control panel home page.
2. Enable SSL for the domain in the list.
3. Click the link at the top of the form that appears.
4. On the page that appears, confirm your details by clicking the Submit button:
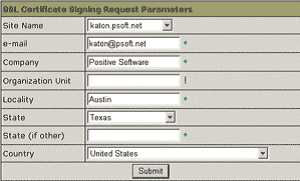
These data will be used to generate the certificate. Don't make changes to the data if you are not sure about the purpose of these changes.
5. Follow instructions that appear at the top of the next page.

6. Copy the signing request and private key for later use.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
NOTE: If you are starting IKEYMAN to create a new key database file, the file is stored in the directory where you start IKEYMAN.
To create a new Key Database:

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
NOTE: You must select all the text in the second dialog box, including Begin Certificate and End Certificate when the CSR is requested.
NOTE: You must select all the text in the second dialog box, including Begin Certificate and End Certificate when the CSR is requested.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
A CSR is a file containing your certificate application information, including your Public Key. Generate your CSR and then copy and paste the CSR file into the web form in the enrolment process:
We recommend that you make a note of your password and backup your key, as only you know these, so if you loose them we can't help! A floppy diskette or other removable media is recommended for your backup files

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
We recommend that you make a note of your password and backup your key as these are known only to you, so if you loose them we can't help! A floppy diskette or other removable media is recommended for your backup files.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
Follow these instructions to generate a certificate request (CSR).

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
Since Microsoft ISA 2000 Server does not have a direct interface for generating Certificate Signing Request, you may need to follow the CSR generation instructions for Microsoft IIS4/IIS5/IIS6 web servers [8]

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
The best resource for Microsoft OCS 2007 is to go directly to the Microsoft TechNet site and follow the instructions for sub section 3.6 Configure Certificates for Front End, Web Conferencing and A/V Server Roles [9].
Once you have followed these instructions, then visit sub section 3.7 Configure the Web Components Server IIS Certificate [9].

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
A CSR is a file containing your certificate application information, including your Public Key. Generate your CSR and then copy and paste the CSR file into the web form in the enrollment process or send it via email to your account manager in Digi-Sign:
Generate keys and Certificate Signing Request:

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
Ironport C100 is currently unable to create keys and certificate requests, however, below are some guidelines on how to generate a CSR and install an SSL certificate on your IronPort device:
*** Generate RSA Key and Certificate Request (CSR) ***
Ironport C100 is currently unable to create keys and certificate requests. You can use "openssl" toolkit on Linux/Windows to generate the CSR. Here are the commands you can use:
On a Linux/Windows computer with OpenSSL toolkit installed:
shell> openssl genrsa -des3 -out server.key 2048 openssl req -new -key
shell> servername.key -out server.csr openssl rsa -in servername.key
shell> -out server.key.PEMunsecure
*** Request Certificate from Digi-Sign **
Send the contents of the "server.csr" file to your account manager in Digi-Sign

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
1. Sign onto the Web server and select the server to manage
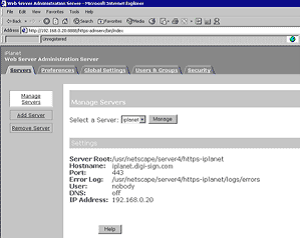
2. Select the Security tab and then Request a Certificate
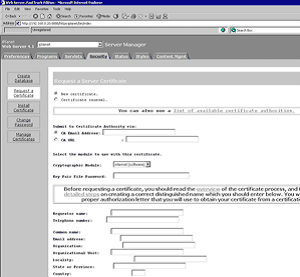
3. Complete the required boxes and click OK
4. An email is then sent to the email address specified containing your CSR
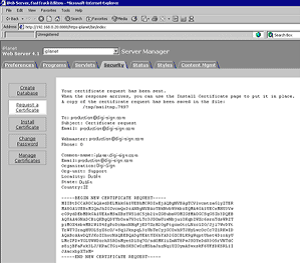
5. The CSR will be required when requesting your certificate.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
1. Restart the administration server by typing the following commands:
2. To request the server certificate, click the Security tab near the top of this page.
3. Select the Request a Certificate link on the left frame.
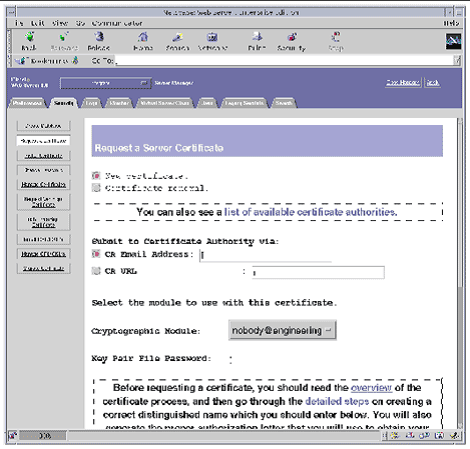
The screenshot depicts the following options:
4. Fill out the form to generate a certificate request, using the following information:
If you can directly post your certificate request to a web-capable certificate authority or registration authority, select the CA URL link. Otherwise, choose CA Email Address and enter an email address where you would like the certificate request to be emailed to.
b. Select the Cryptographic Module you want to use.
Each realm has its own entry in this pull-down menu. Be sure that you select the correct realm. To use the Sun Crypto Accelerator 1000, you must select a module in the form of user@realm-name.
c. In the Key Pair File Password dialog box, provide the password for the user@realm-name that will own the key.
d. Provide the appropriate information for the following fields:
e. Click the OK button to submit the information.
5. Send the CSR to Digi-Sign.
6. Once the certificate is generated, copy it, along with the headers, to the clipboard.
NOTE that the certificate is different from the certificate request and is usually presented to you in text form.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
To request a certificate, perform the following steps:
1. For the Server Manager you must first select the server instance from the drop-down list.
2. Perform the following steps to specify how you want to submit the request for the certificate:
At the end of this process, you may also copy your request in a text format and apply for your certificate online through Digi-Sign website at: http://www.digi-sign.com/product/digi-ssl/ [10] or through your Digi-CA™ [11] Service Account, if you are using the Digi-Sign certificate management system. When prompt, paste your request into a Certificate Signing Request (CSR) box.
3. Select the cryptographic module for the key-pair file you want to use when requesting the certificate from the drop-down list.
4. Enter the password for your key-pair file.
5. Enter your identification information.
You need to provide the following information:
Common Name must be the fully qualified hostname used in DNS lookups (for example, www.yourdomain.com [12]). This is the hostname in the URL that a browser uses to connect to your site. If these two names don't match, a client is notified that the certificate name doesn't match the site name, creating doubt about the authenticity of your certificate.
Email Address is your business email address. This can be used for correspondence between you and Digi-Sign.
Organization is the official, legal name of your company, educational institution, partnership, and so on. You need to verify this information with legal documents (such as a copy of a business license).
Organizational Unit is an optional field that describes an organization within your company. This can also be used to note a less formal company name (without the Inc., Corp., and so on).
Locality is a field that usually describes the city, principality, or country for the organization.
State or Province is usually required, but can be optional.
Country is a required, two-character abbreviation of your country name (in ISO format). The country code for the United States is U.S.
All this information is combined as a series of attribute-value pairs called the distinguished name (DN), which uniquely identifies the subject of the certificate.
Double-check your work to ensure accuracy. The more accurate the information, the faster your certificate is likely to be approved.
6. Click OK.
7. For the Server Manager, click Apply, and then Restart for changes to take effect.
If you chose to email the request, the server composes an email message containing the request and sends the message to Digi-Sign. Typically, the certificate is then returned to you via email.
If for any reason your network security settings or a firewall configuration prevents your server from sending the certificate request via email, copy the entire request string, that should appear on the screen and send it manually to your account manager in Digi-Sign or to Digi-Sign Production Department from a PC, that has access to Internet mail.
Once you receive the certificate from Digi-Sign, you can install it. In the meantime, you can still use your server without SSL.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
In this first step you generate a request for Digi-Sign to issue a certificate. It involves generating a public/private key-pair and identifying the server, the organization using it, and its Webmaster. The private key is encrypted and should never leave your server, except for backup purposes. The public key will become part of the certificate and is therefore sent to Digi-Sign, together with the rest of the information identifying your organization and your server.
To generate a certificate request, you will run the interactive utility genreq and enter the information for which it prompts you.
When the prompt specifies a default value, you can just press return to enter that value, or enter a different value if you prefer.
For an example of how to use genreq, see the following sample genreq session. Before you start, create a directory to store all SSL related files in, for example $ORACLE_HOME/ows2/ssl. To avoid typing long path names or moving files later, you can start genreq from this directory. To run genreq, do the following:

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
A CSR is a file containing your certificate application information, including your Public Key. Generate your CSR and then copy and paste the CSR file into the web form in the enrollment process.
Important Notes on Certificates
Generate a Self-signed Certificate or Certificate Signing Request
Access the domain management function by clicking on the Domains button at the top of the PSA interface. The Domain List page appears.
2. If you have established an IP based hosting account with SSL support, the Certificate button will be enabled.
3. Click the Certificate button. The SSL certificate setup page appears.
4. The Certificate Information: section lists information needed for a certificate signing request, or a self-signed certificate. You must fill out these fields before generating your CSR or self-signed certificate.
5. The Bits selection allows you to choose the level of encryption of your SSL certificate. Select the appropriate number from the drop down box next to Bits.
6. To enter the information into the provided text input fields (State or Province, Locality, Organization Name and Organization Unit Name (optional)) click in the text boxes and enter the appropriate name.
7. To enter the Domain Name for the certificate click in the text box next to Domain Name: and enter the appropriate domain.
8. The domain name is a required field. This will be the only domain name that can be used to access the Control Panel without receiving a certificate warning in the browser. The expected format is www.domainname.com [16] or domainname.com.
9. Click on the Request button.
10. Selecting Request results in the sending of a certificate-signing request (CSR) to the email address you provided in the certificate fields discussed above. When a CSR (certificate signing request) is generated there are two different text sections, the RSA Private Key and the Certificate Request. Do not lose your RSA private key. You will need this during the certificate installation process. Losing it is likely to result in the need to purchase another certificate.
11. Copy and paste the Certificate Request emailed to you into the InstantSSL web form where it requests a CSR (Certificate Signing Request).
12. When you are satisfied that the SSL certificate has been generated or the SSL certificate

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
Follow these instructions to generate a CSR for your Web site. When you have completed this process, you will have a CSR ready to submit to your provider in order to be generated into a SSL Security Certificate.
Access the domain management function by clicking on the Domains button at the top of the PSA interface. The Domain List page appears.
2. If you have an IP based hosting account with SSL support, the Certificate button will be enabled. If you have a name based hosting account the Certificate button will be greyed out. You must have an IP based hosting account to continue.
3. Click the Certificate button. The SSL certificate setup page appears.
4. The Certificate Information: section lists asks for a number of fields to be completed to generate your CSR.
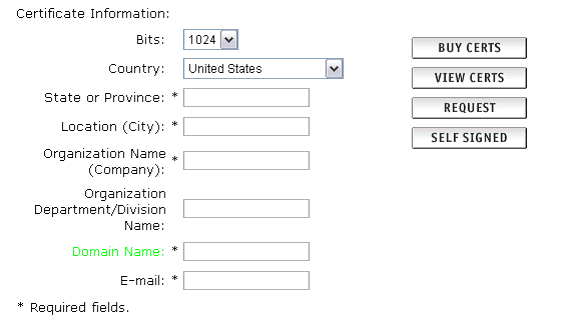
5. The Bits selection allows you to choose the level of encryption of your SSL certificate. Select the appropriate number from the drop down box next to Bits.
6. Enter your details into the State or Province, Locality, Organization Name and Organization Unit Name (optional) fields.
7. Enter your domain name into the Domain Name: field.
8. The domain name is a required field. This will be the only domain name that can be used to access the Control Panel without receiving a certificate warning in the browser. The expected format is www.domainname.com [16] or domainname.com
9. Click on the Request button displayed to the right of your details.
10. Plesk will now email your CSR to the email address provided when you signed up. You will see that the email contains two sections - the RSA Private Key and the Certificate Signing Request. Do not lose your RSA Private Key, you will need this later.
11. Copy and paste the Certificate Request emailed to you into your SSL Provider's enrolment form where it requests a CSR (Certificate Signing Request).
12. Click Up Level to return to the Domain Administration page.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
To generate a certificate signing request (CSR) follow these steps:
2. Specify the certificate name.
3. The Bits selection allows you to choose the level of encryption of your SSL certificate. Select the appropriate number from the drop-down list.
4. Select a country from the drop-down list
5. Specify the state or province, location (city).
6. Enter the appropriate organization name and department/division in the field provided.
7. Enter the Domain Name for which you wish to generate the certificate-signing request.
8. Click the REQUEST button. A certificate-signing request will be generated and added to the repository. You will be able to add the other certificate parts later on.
NOTE: Do not lose your RSA Private Key, you will need this later.
Generating a CSR using an existing private key
In some cases you have a certificate in the repository, which has only the private key part and the other parts are missing due to some reasons. To generate a new Certificate Signing Request using the existing private key, follow these steps:
2. Click REQUEST.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
Follow these instructions to generate a CSR for your Web site. When you have completed this process, you will have a CSR ready to submit to your provider in order to be generated into a SSL Security Certificate.
2. Click on the domain name that you wish to generate the CSR for.
3. On the Certificate repository page click on the Add button.
4. Specify a certificate name.
5. Select the bit size from the drop-down list. 2048 is recommended.
6. Select a country from the drop-down list.
7. Specify the state or province, location (city).
8. Enter the appropriate organization name and department in the field provided.
9. Enter the Domain Name for which you wish to generate the certificate signing request.
10. Click the Request button. A certificate signing request will be generated and added to the repository. When you return to the Certificates page from the list at the bottom of the page, click on the certificate name that you just created. Copy the content of this box labelled 'CSR'. It should look similar to the example below:
11. Your CSR will now have been created. Copy and paste the contents into your SSL Provider's online enrolment form when requested.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
To access the Domain certificates repository page, click the Certificates icon at the Domain administration page. The certificates repository page will open displaying the list of available certificates:
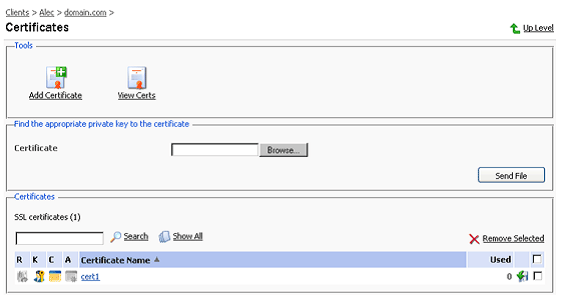
The four icons, preceding the certificate name in the list, indicate the present parts of a certificate. The icon displayed in the R column indicates that the Certificate Signing request part is present in the certificate, the icon in the K column indicates that the private key is contained within the certificate, the icon in the C column indicates that the SSL certificate text part is present and the icon in the A column indicates that CA [6] certificate part is present. The number in the Used column indicates the number of IP addresses the certificate is assigned to.
To add a certificate to the

repository, click the Add Certificate icon at the Domain certificate repository page. The SSL certificate creation page will open. On this page you can generate a self-signed certificate, certificate-signing request, purchase a SSL certificate, and add the certificate parts to an existing certificate.
NOTE: When acquiring or generating new certificates, make sure that the values you enter into the fields 'domain name', 'email address', 'state or province', 'location', 'organization name', and 'department name' do not exceed the limit of 64 symbols.
To generate a certificate signing request (CSR) follow these steps:
2. The Bits selection allows you to choose the level of encryption of your SSL certificate. Select the appropriate number from the drop-down list.
3. Select a country from the drop-down list.
4. Specify the state or province, location (city).
5. Enter the appropriate organization name and department/division in the field provided.
6. Enter the Domain Name for which you wish to generate the certificate signing request.
7. Specify the E-mail address.
8. Click the Request button. A certificate-signing request will be generated and added to the repository. You will be able to add the other certificate parts later on.
A situation may occur in some cases, that you have a certificate in the repository, which has only the private key part and the other parts are missing due to some reasons. To generate a new Certificate Signing Request using the existing private key, follow these steps:
2. Click Request.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
You must submit your request in a particular format called a Certificate Signature Request (CSR). WebLogic Server includes a Certificate Request Generator servlet that creates a CSR. The Certificate Request Generator servlet collects information from you and generates a private key file and a certificate request file. You must then submit the CSR. Before you can use the Certificate Request Generator servlet, WebLogic Server must be installed and running.
Start the Certificate Request Generator servlet (certificate.war). The .war file is automatically installed when you start WebLogic Server. In a Web browser, enter the URL for the Certificate Request Generator servlet as follows:
https://hostname:port/Certificate [17]
Hostname is the DNS name of the machine running WebLogic Server. Port is the number of the port at which WebLogic Server listens for SSL connections.
For example, if WebLogic Server is running on a machine named 'server' and it is configured to listen for SSL communications at the default port 7002 to run the Certificate Request Generator servlet, you must enter the following URL in your Web browser:
https://server:7002/certificate [18]
The Certificate Request Generator servlet loads a form in your web browser. Complete the form displayed in your browser.
Click the Generate Request button. The Certificate Request Generator servlet displays messages informing you if any required fields are empty or if any fields contain invalid values. Click the Back button in your browser and correct any errors.
NOTE: Private Key Password if you do not specify a password, you will get an unencrypted RSA private key. If you specify a password, you will get a PKCS-8 encrypted private key. When using PKCS-8 encrypted private keys, you need to enable the Use Encrypted Keys field on the SSL tab of the Server window in the Administration Console.
When all fields have been accepted, the Certificate Request Generator servlet generates the following files in the start-up directory of your WebLogic Server: mydomain_com-key.der-The private key file. The name of this file should go into the Server Key File Name field on the SSL tab in the Administration Console. mydomain_com-request.dem-The certificate request file, in binary format. mydomain_com-request.pem-The CSR file that you submit... It contains the same data as the .dem file but is encoded in ASCII so that you can copy it into email or paste it into a Web form.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
A CSR is a file containing your certificate application information, including your Public Key. Generate your CSR and then copy and paste the CSR file into the web form in the enrollment process.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
1. From WS_FTP Server, in the left pane, expand the FTP host and select SSL. The SSL Host Options appear in the right pane.
2. Click Certificate Management, then select the Certificate Creation tab.
3. Enter a name in the Certificate Set Name box. This will be the name of the certificate that is generated by WS_FTP Server.
4. Click the Browse (...) button in the Output Location box to select the folder you want the certificate created in.
5. Enter information in all of the Certificate Information boxes:
6. After all of the boxes are filled in correctly click Create to generate the keys, certificate, and certificate-signing request. If all of the boxes are not filled in, you cannot create the certificate.

Effective 1 January 2011, we will no longer support any Certificate Signing Request [CSR] generated with a 1024 bit key. This is because NIST, PKIX, WebTrust and other respective security standards no longer consider the 1024 bit key size as secure. Read more > [1]
Links:
[1] http://www2.digi-sign.com/about/announcements/2048
[2] http://www2.digi-sign.com/digi-ssl
[3] http://www2.digi-sign.com/en/node/add/forum/11
[4] http://www.sun.com/hardware/serverappliances/documentation/manuals.html
[5] http://www.digi-sign.com
[6] http://www2.digi-sign.com/certificate+authority
[7] http://www.company.com
[8] http://www2.digi-sign.com/support/digi-ssl/Microsoft+iis+5+iis+6
[9] http://www2.digi-sign.com/http
[10] http://www.digi-sign.com/product/digi-ssl/
[11] http://www2.digi-sign.com/digi-ca
[12] http://www.yourdomain.com
[13] http://www2.digi-sign.com/digital+certificate
[14] http://www.yoursitename.com
[15] mailto:sleuniss@yoursitename.com
[16] http://www.domainname.com
[17] https://hostname:port/Certificate
[18] https://server:7002/certificate