

Read about some 'real world' examples of organisations using Digital Certificates and how these solutions were implemented.
![]() [1] National ID Cards are adopting the security of PKI and to be recognized internationally, ISO 27001 Certification is the preferred option.
[1] National ID Cards are adopting the security of PKI and to be recognized internationally, ISO 27001 Certification is the preferred option.
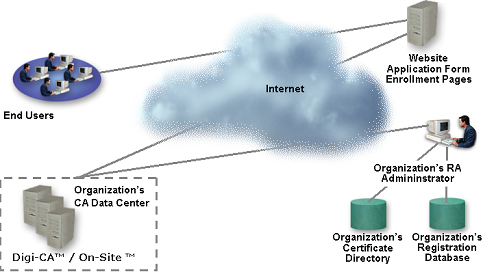
The e Government strategy for the Kingdom of Bahrain is spearheaded by the Central Informatics Organization [2] [CIO]. In 2005, the decision was taken to digitize the Bahrain National ID card using smart cards.
Given the extensive PKI experience within the CIO and the need to protect the integrity of the electronic data that would be stored on the new smart card ID, it was decided that PKI was the best security option.

Following best practice according to the World Trade Organization [WTO] for Government projects, the CIO published their requirements and invited the world leaders in PKI to a workshop open forum in April 2006. Every CA & PKI vendor was in attendance and as the official offerings were submitted, every offering was ‘the same’. Only Digi-Sign had the foresight to stress the importance of support, management and international accreditation according to ISO 27001.
Every CA/PKI vendor will promise the best in service, the best experience, the best people and the best support. However, few can clearly demonstrate this prior to purchase. Moreover, few will guarantee third party accreditation of their offering.
In 2004, the Digi-CAST™ Methodology was pioneered by Digi-Sign to address this critical need. Rather than having the customer use complicated matrices for vendor selection and then attempting to ‘work through’ the delivery, Digi-CAST™ offers the customer a tried and tested project planning, documentation, delivery and management system according to internationally recognized ‘best practice’.
In 2006, BS 17799 became ISO 27001 and is now the defacto international standard for IT Security. The Digi-CAST™ Methodology ensures that this standard is delivered to the customer according to their specific needs and then guarantees certification to ISO 27001 on completion.
The results from this international tender process and the fact that Digi-Sign was awarded this project are now a matter of public record. And the reason for the successful bid, was partly due to the fact that implementing ISO 27001 was stipulated by Digi-Sign as part of the submission.
Most importantly, the project was delivered through close co-operation with the CIO personnel at every level of the organization. User Acceptance Testing [UAT] was completed in November 2007 and the Board of the CIO has implemented its ISO 27001 policy on schedule, awaiting audit in Q1 2008, as planned.
The overall project and the subject of the original specification was to provide a PKI system capable of protecting the millions of National ID cards that would be issued.
It was Digi-Sign’s insistence that best practice be followed and that this was supported by a genuine methodology for delivery combined with a system for subsequent ongoing management that ensured the project’s success.
In addition to following a specific methodology for delivery, the Digi-TaSC [3] on line system for managing the environment was also provided to the CIO. This powerful system enables the tracking and tracing of all policies, procedures and personnel in accordance with the ISO 27001 manual for the environment.
This same system extends to manage all support and support escalation, case logging, ticketing and reporting and is a valuable tool to any organization seeking to implement a National Trust Centre for any e Government initiative.
The newest release of the Digi-CA™ Xg for national and large scale projects was used on the CIO project. As probably the most advanced and sophisticated CA system available anywhere in the market today, this system was modified to meet the precise requirements of the CIO and was delivered in less than nine weeks (after detailed specification was agreed). No other vendor can meet the efficiency that Digi-CA™ offers and this is one reason why Digi-CA™ remains the most competitively priced CA system in the market today.
![]() [1] From San Quentin to Rikers Island, some 150,000 US Department of Corrections inmates are provided with vending, commissary and laundry services; and vocational and culinary training by Canteen Correctional Services.
[1] From San Quentin to Rikers Island, some 150,000 US Department of Corrections inmates are provided with vending, commissary and laundry services; and vocational and culinary training by Canteen Correctional Services.
Canteen Correctional Services [CCS] is a division of Compass Group North America, a $5 billion food service and hospitality company with more than 116,000 associates throughout the US and Canada.
Associates of CCS spend much of their time in the field dealing with clients and undertaking day-to-day tasks relating to sales, support and customer relationship management. As part of this daily routine, a CCS Associate would visit one of the thousands of US Penitentiaries each day and access corporate documents and files from the CCS extranet. Access to the extranet was by way of a username and password.
CCS conducted an IT Security audit and clearly identified the possibility of unauthorized access to its extranet. It needed to take proactive, remedial action.
Mirroring the high level of security that is synonymous with the US Department of Corrections, CCS needed to ‘lock down’ its extranet and provide highly secure access to its Associates.
CCS already had a fully operational extranet when they began researching the market for methods to secure its Associates’ access. With hundreds of highly sensitive documents stored on the extranet, usernames and passwords posed too much of a threat to the company’s security. If a competitor or other unauthorized user accessed this data, the damage to the company’s reputation and/or the competitive advantage they would loose, was too high a risk to leave unresolved.
Knowing, with certainty, the identity of each extranet user was the issue. As with most customers that contact Digi-Sign, CCS had investigated the wide range of hardware and software security options in the market. In solving the particular security issue, these alternatives raised other issues.
Most software needs upgrading every year. CCS’s IT Department was reluctant to add more software to their Desktops or more work to their Help Desk. Tokens using asynchronous number authentication, like RSA® SecurID®, were too expensive. Digital Certificates were an option, but CCS was not sure how to implement them.
Working with Digi-Sign, the CCS requirement was designed from the ‘outside in’. Meaning that Digi-Sign examined the CCS Associate’s working environment first and then worked back from there to provide the most practical and simple-to-use solution.
Each Associate travels from location to location, and more often than not, cannot bring any type of PC or notebook into the prison. In some cases, the visit may be sales related and could be a once-off visit that may not be repeated by the Associate. The new access solution needed to be very secure, small and highly portable.
Digital Certificates would provide two factor, secure authentication of the Associate. Once the server was configured, Digi-Access™ would control who had access to the data stored on the server. Most web servers from Apache to Zeus work with Digi-Access™. Configuring a server to work with strong two factor authentication using Certificates is called Digi-Access™.
By storing the Digi-CA™ Certificates on a hardware device, the issue of portability and the ability to bring the small device into the prisons was also solved. Using a USB token
[Digi-Token™], the Digi-CA™ Certificate would be given to the Associate and they would use PCs belonging to the US Department of Corrections during their visits.
Digi-Sign is probably the only CA provider in the world that offers both types of Certificate Authority [CA]: Managed CA and CA Software.
A Managed CA is located in a secure data centre and the customer accesses the solution over a highly secure Internet connection. The solution is charged on an annual recurring subscription basis depending on the number of end users or seats, the customer wishes to use the CA for. Digi-CA™ Service is the Managed CA.
CA Software is like most software in that it is sold ‘in a box’ and is usually delivered and installed at the customer’s site. CA Software is life-time software purchased in Year-1 with an annual maintenance fee thereafter. Digi-Sign’s CA Software is called Digi-CA™ Server.
Digi-CA™ Service was the obvious choice for CCS, but CCS did not have the necessary resources to make the initial deployment.
When an organization wants all the benefits of using Certificates but does not have either the time or the resources to manage them, then Total Trust Management™ [TTM™] is the best option. TTM™ is a unique service offering from Digi-Sign that means every aspect of the Digi-CA™ environment is Totally Managed by Digi-Sign personnel - exactly as the customer instructs. All aspects of the initial deployment, the day-to-day administration of the Digi-CA™ Service and the life-cycle management of every Certificate is totally managed for the customer by Digi-Sign personnel.
Combining all of CCS’s needs into a single offering, from a single vendor, solved all their requirements. As a standard provision of TTM™, Digi-Sign also manages the Help Desk function for the environment meaning that no resources are required in CCS other than a single point of contact.
The Digi-Sign TTM™ Team issue each Associate with a Digi-Token™ for storing the Certificate. The life-cycle of the Certificate; adding and removing Associates and ensuring the smooth operation of the every aspect of the Digi-CA™ Service is managed by Digi-Sign under strict instructions from CCS.
![]() [1] The two largest providers of natural gas in the British Isles shared similar difficulties in communicating and co-operating with external service providers and Gas Installers.
[1] The two largest providers of natural gas in the British Isles shared similar difficulties in communicating and co-operating with external service providers and Gas Installers.
Both companies are responsible for the transmission, distribution and supply of natural gas and are also responsible for the development and maintenance of the various gas transportation systems. As gas producers and distributors, both organizations are also directly involved in gas procurement and supply on the open market.
Utility companies clearly understand the need for tight cost control across the entire organization. IT expenditure is considered to be a part of the total operational costs. Any expenditure must clearly demonstrate cost reduction in the shortest possible time. Total Cost of Ownership [TCO] is usually examined in terms of twelve months or less.
As an industry dealing in fossil fuels, technological advances were more evident in the drilling fields than in the IT Department.
In less than a decade, both organizations experienced exponential growth in their respective customer bases. This business progression demanded that the manual gas consumption and billing procedures be replaced with sophisticated computerised systems. SQL based data servers using Oracle®/IBM® were selected for their efficiency, flexibility and the overall stability of the software’s providers. As with most large organizations, the clear benefits and cost savings of this computerisation prompted further investment in IT.
By the end of the 1990’s, the IT Department was a wholly integrated and essential component in the management of most aspects of day-to-day operations. The storage of all business critical data was centralised and secured in data centres. Access to this data was restricted to proprietory private networks and local area access only.
The technological boom of the Internet, in early 2000, was initially viewed with scepticism by both companies. The only tangible reaction was a heightened concern surrounding the hardening of existing security and the possible use of the basic Internet infrastructure to help reduce costs. Typically this involved little more than replacing frame relay networks with Virtual Private Networks [VPNs].
As consumers and businesses began to understand the difference between Internet ‘hype’ and its true business benefits, the same enthusiasm for IT that was evident in the early 1990’s was reinvigorated by the introduction of Internet based business applications. Because the SQL providers, like Oracle® and IBM® had rapidly integrated Internet technologies in their software and servers, this meant that both organizations could easily ‘open up’ more and more parts of the network and its information.
The business case was obvious. By providing access to external users, these commercial customers could process purchases in ‘real time’ for the area required. This reduced cumbersome paper-based processes with instant accounting and effectively removed the ‘human element’. Therefore, it was consistent with the TCO business principles of the organizations. However, this business opportunity presented a new set of problems for the two IT Departments. Opening up any part of the network on the Internet required good planning, hardening the perimeter and monitoring internal traffic to ensure that IT security remained unaffected.
Firewalls like Cisco® and Check Point® required regular monitoring and updating so that the Firewall Policy protected the principle point of entry. Intrusion Detection Systems [IDS] such as ISS® and Cisco® were used to monitor ‘unusual packets’ on the network and servers were protected with additional advice from security consultants. Combining all of these, the security of the total environment is maintained. In one of the organizations, it was HP® that raised the all-important issue of ‘who’ rather than just how’.
Examining one particular company in more detail, HP® had clearly defined how the network infrastructure was secured, but who had access to it presented them with several problems. Knowing, with certainty, the identity of each user was a new security issue. It was clear that usernames and passwords would not provide sufficient authentication of the end user.
Dial-in software from the firewall was considered as an alternative, however each of the commercial customers experienced conflicts with their own firewalls. There were many software variants available, but the customer did not want to be responsible for distributing and upgrading software.
Tokens using asynchronous authentication like RSA® SecurID® were too expensive. Digital Certificates were considered, but the server software was not capable of working with x.509v3 Certificates or of handling additional x.509 extension fields.
Most Traditional Certificate Authority [4] [CA] providers’ systems are Unix based. In some cases, the core technology of these Traditional CAs is more than ten years old. A decade ago, Unix was necessary to ensure high levels of security and overall system integrity. Unfortunately, the ‘trade off’ means that these, albeit highly secure, systems are not very flexible. Making even minor alterations (such as changing Certificate
extension fields) proved prohibitively expensive.

This is not the case with Digi-CA™. Digi-CA™ Digital Certificates use the latest in CA technology. By combining its proprietary technology with Open Source technology and security hardened Linux, every aspect of Digi-CA™ can be changed and customised easily and usually at a minimal cost to the customer.
Digi-Sign is probably the only CA provider in the world that offers both types of Certificate Authority [CA]: Managed CA and CA Software.
A Managed CA is located in a secure data centre and the customer accesses the solution over a highly secure Internet connection. The solution is charged on an annual recurring subscription basis depending on the number of end users or seats, the customer wishes to use the CA for. Digi-CA™ Service is the Managed CA.
CA Software is like most software in that it is sold ‘in a box’ and is usually delivered and installed at the customer’s site. CA Software is life-time software purchased in Year-1 with an annual maintenance fee thereafter. Digi-Sign’s CA Software is called Digi-CA™ Server.
In this specific customer case study, the requirement was small (less than 2,500 users). Although Service™ was the obvious choice, the legal liabilities in the Digi-Sign Certificate Practice Statement [Digi-CPS™], meant that although technically Digi-CA™ Service could be modified, legally it could not. Therefore, Digi-CA™ Server was selected so that the entire Certificate Chain could be modified to meet the precise requirements of the customer environment.
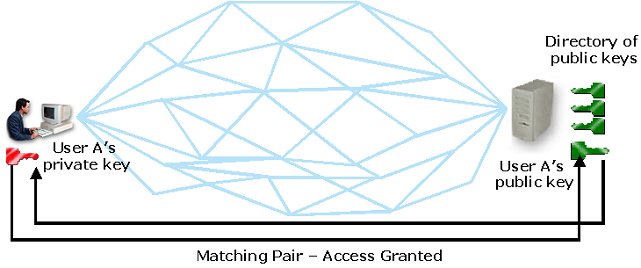
If the Digital Certificates issued by a CA are to have any legal standing or real business purpose, they must have, what is called, non-repudiation. Non-repudiation is deniability. If the recipient of a Digital Certificate can show that the organization that issued the Certificate does not operate the CA in accordance with internationally accredited standards and local laws for Digital Signatures, then any transaction conducted using any Certificate from that CA has no non-repudiation. In other words, all the transactions can be denied and have no legal standing. For non-repudiation to exist, that CA must document its operation using a Certificate Practice Statement [CPS] and a Certificate Policy. The Digital Certificate Policy is a ‘who’, ‘what’, ‘where’ and ‘how’ document that describes the principles of the Digital Certificate usage; how they are issued and under what conditions; how an end user receives or applies for a Digital Certificate; and then references the CPS for issues relating to law, location, security, insurance and other operational matters.
Digi-Sign has simplified producing this complex series of documents using a single ‘intelligent’ questionnaire that is used to generate the Certificate Policy easily. The Policy stipulates that the CA is secure, cannot be compromised and that the end users are correctly identified. This Policy ensures that all Certificates have the non-repudiation the organization requires.
There are two primary ways that Digi-CA™ Certificates can be delivered to the end user. The first method is the Package Method, where both the public and the private key are generated together and delivered together – in a ‘package’. In the second method, the Process Method, there are two stages, or processes, in getting the Certificate. With the Process Method, the private key never leaves the users device (floating text box/Alt tab text: PC Registry, Smartcard, USB Token or other Certificate storage media device).
The Certificate Policy agreed with the gas company, when combined with the uniqueness of the specific environment, meant that the Certificates needed to be delivered using the Package Method. It was further agreed that each Certificate would be delivered using the Total Trust Management™ [TTM™] service.
When an organization wants all the benefits of using Digi-CA™ Certificates but does not have either the time or the resources to manage them, then Total Trust Management™ [TTM™] is the best option. TTM™ is a unique service offering from Digi-Sign that means every aspect of the Digi-CA™ environment is Totally Managed by Digi-Sign personnel - exactly as the customer instructs. Referencing the Certificate Policy, all aspects of the initial deployment, the day-to-day administration of the CA and the life-cycle management of every Certificate is totally managed for the customer by Digi-Sign.
For the gas company, given its unique combination of ‘problems’, it elected to use Digi-CA™ Server and to have Digi-Sign host and manage it under an expanded version of TTM™. Combining all of their requirements into a single offering, from a single vendor, solved every aspect of their requirement in every detail. As a standard provision of TTM™, Digi-Sign also manages the Help Desk function for the environment meaning that no resources are taken from the gas company.
Configuring a server to work with strong two-factor authentication using Certificates is called Digi-Access™. Once the server is configured, Digi-Access™ controls who has access to the data stored on the server. Most web servers from Apache to Zeus work with Digi-CA™ Certificates. In addition, integrated server software like that found on Oracle®, IBM® and other branded servers are also compliant.
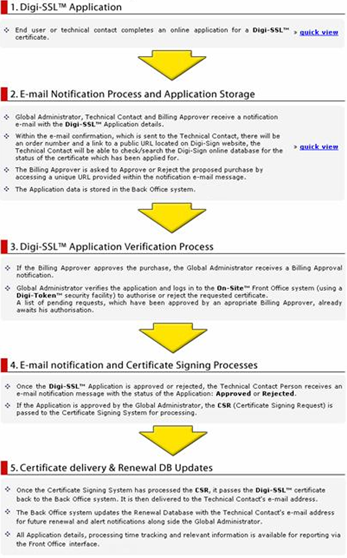
Prior to the initial deployment of the solution, Digi-Sign Professional Services ensured every aspect of the gas company’s environment was correctly configured to work with Digi-CA™.
For the deployment, the gas company prepared a simple Excel® spreadsheet with the details of the initial ‘block’ of users. The Digi-Sign TTM™ Team then issued each end user with a Digi-CA™ .p12 file by email (a .p12 file is one type of Package used when sending Certificates using the Package Method). On opening the received file, the user was invited to apply for a Personal Identification Number [PIN] to unlock and install the Certificate.
In accordance with the Certificate Policy, the PIN was supplied using a pre-defined set of protocols, either by telephone or to a specified email address within the end user organization. If the request conformed to the protocol, the PIN was issued. When the end user entered the PIN, the Certificate was then automatically installed in the Certificate Store of Microsoft’s® browser, Internet Explorer.
As more and more customers of the gas company require access, using the same predefined security protocols, it simply emails or telephones in the end user details to the Digi-Sign TTM™ Team. The request protocols are verified and if they match those in the Policy, the Certificate is dispatched.
All technical support issues, all Help Desk functions and every aspect of the Certificate life-cycle is managed by Digi-Sign under TTM™.
The customer continues to save costs, increase productivity and communicate more efficiently with its customers, safe in the knowledge that Digi-Sign’s total solution protects the environment in a way that was previously believed to be impossible.
![]() [1] One of the world’s largest human resource companies required an SSL management system that could meet their global requirement. In purchasing centrally, they wanted to be sure that the savings made were not lost through inter-company billing and administrative issues.
[1] One of the world’s largest human resource companies required an SSL management system that could meet their global requirement. In purchasing centrally, they wanted to be sure that the savings made were not lost through inter-company billing and administrative issues.
As one of the world’s largest human resource companies in the world, Mercer employs more than 15,000 individuals in 40 countries around the world. Each country has one or more web servers that require Secure Socket Layer [SSL] web server protection. Mercer had been using the ‘world leader’ in SSL supply but could not get the SSL management solution they required to accurately meet the global requirement.
In approaching Digi-Sign, Mercer came to understand that managing SSLs in quantity requires a sophisticated solution capable of meeting all their requirements.
An organization like Mercer understands the technical aspects of SSL. Their principle issue was that there was no real centralized process for purchasing SSLs and attempts to implement one would result in more costs than savings. They were seeking a solution that would permit the economics of ‘bulk purchase’ to be retained whilst also implementing a method of controlling SSL consumption.
In learning about Mercer’s total global requirement and also understanding internal procedures for IT requisitioning and purchasing, Digi-SSL™ Service was customized to meet Mercer’s precise requirements. In addition, the entire solution was designed, activated and continues to be managed for less than the cost of the previous supplier.
A simple order, approve, request and deliver flow diagram was designed. Each SSL request would be entered through the Control Centre by any of Mercer’s approved Administrators. This request automatically requested a Manager’s approval and only once this approval was received would the SSL request be processed by the Digi-SSL™ system.
This workflow and management solution has resulted in a significant improvement in SSL usage and purchasing for all the companies in the group.

![]() [1] Norwich Union, Allianz, AXA, Fortis, Legal & General, Royal & Sun Alliance, KGM, NIG and Provident are just some of the household names using this online service.
[1] Norwich Union, Allianz, AXA, Fortis, Legal & General, Royal & Sun Alliance, KGM, NIG and Provident are just some of the household names using this online service.
InsureLink is an online insurance portal that enables insurers to distribute new and amended products to brokers seamlessly and in real time. Insurers can create products and adjust prices as often as required via a single path to market and are free from the constraints of traditional systems where delays in getting products to market exist.
The insurers now have complete control from their desktop, enabling them to directly control rate testing, switching rates on and off, providing different brokers with different products and which brokers they want to trade with. The speed of delivery and security has been dramatically improved, allowing immediate delivery of products to market and access to participating brokers.
The result is lower distribution costs, reduction in data keying, access to more business information and more time to set rates based on current market conditions.
This Insurecom system is an example of a business-to-business e-commerce system that not only required a secure access security system, but a system that could be easily integrated into their existing environment.
After three years of working with Digital Certificates, Insurecom was not satisfied with the service or supply from the Traditional Certificate Authority [4] [CA] system they had been using for Certificates. The vendor was slow to react to support queries and the management interface was antiquated. They needed a new CA system.
Digi-Access™ Service was the solution that met all of their requirements. It also had a simple procedure for moving the Certificate users from the old Traditional CA system to the newer Digi-CA™ Service system.
With literally hundreds of users accessing the system every day, without Digi-Sign, replacing the Traditional CA could have been a difficult task.
Digi-CA™ Service easily overcame all migration obstacles with its ‘auto migration’ engine. This engine provides for complete migration in a simple process that is seamless to the end user and requires minimal resources from the organization operating the Traditional CA that is to be replaced.
Traditional CAs can be migrated to Digi-CA™ in several ways:
1. Export & Import
2. Renewal Change Over
3. Revokation & Reissue
1. Export& Import
By exporting all of the Digital Certificate data, and user information, from the Traditional CA, this data can be imported directly into the Digi-CA™ Service system. By doing this, the Traditional CA can be shut down immediately because Digi-CA™ is capable of managing multiple Certificates, regardless of the original vendor. There is no loss of service and the total environment continues to operate without interruption.
2. Renewal Change Over
Most CAs reissue Digital Certificates each year and revoke the previous year’s Certificates in the process. This Certificate Renewal Process is an ongoing component of the CA environment.
Working with the Certificate Policy for validating users, the Digi-CA™ system simply switches the older Digital Certificate for the new Certificate during the Renewal Process. The end user experiences no interruption of use and often can be completely unaware that the Legacy CA has been replaced by the new Digi-CA™ system.
3. Revokation & Reissue
In some cases the Traditional CA is too inflexible to use either of the previous migration methods and the simplest solution is to revoke all of the older Certificates and issue the new ones as required.
The Renewal Change Over process was used in this Digi-CA™ Service case. Insurecom used the Certificate Renewal Process to replace the older Certificates with Digi-CA’s™ and migrated from the Legacy CA to complete the process during the course of the year.
There was no service interruption, no loss of access and no ‘down time’ in the process. The resources used in the migration were no more than had been used in the operation of the Legacy CA and the entire environment continued to operate uninterrupted.
The Insurecom system operates more efficiently and uses less human resources than was the case with the Legacy CA.
Insurecom enjoyed the benefits of Digi-CA™ without the usual complications associated with migrating from one system to another. For Insurecom, the decision to migrate was a difficult one, but one that reaped significant rewards.
It is worth noting that in addition to the time and human resource savings afforded to Insurecom as a result of migrating from the Legacy CA to Digi-CA™, the annual subscription costs are lower too!

![]() [1] As a profession synonymous with the written word and the ‘right to a fair trial’, technology has been slow to enter the halls of justice. The technological advances that have been made are usually introduced through the governing bodies or legal associations.
[1] As a profession synonymous with the written word and the ‘right to a fair trial’, technology has been slow to enter the halls of justice. The technological advances that have been made are usually introduced through the governing bodies or legal associations.
The Pennsylvania Board of Law Examiners grants admission to the bar in the commonwealth of Pennsylvania. Traditionally, test papers, exams and essays were distributed on paper. Professors and Administrators prepared the necessary documents and drafts were marked, re-marked and finalized before being sent for secure printing. Students who sat these examinations or submitted essays and term papers, also used traditional paper-based methods. Exam’ results and term papers were also graded manually and on paper.
The use of email in academia is now commonplace. All aspects of college and university communications are electronic wherever possible. This proliferation of technology prompted the Pennsylvania Board of Law Examiners to find an electronic solution to ease the most laborious component of their environment: term paper grading.
The process of preparing a term paper involves several contributors. These Professors must exchange ideas, agree test principles and set the term paper requirements. This preparatory work must be kept secret if the Board is to keep its reputation. In electing to use secure email, the primary objective was absolute security.
On the understanding that security was central to the solution, issues relating to deployment of the software and subsequent management of users were examined. It was obvious that a software solution would create more problems than it would actually solve. A student recommended that the Board look to Digital Certificates to solve these issues.
Microsoft®, Lotus Notes®, Mozilla, Eudora®, Thunderbird and most email software in the market today are all compliant with the x.509 Digital Certificate standards. This means that regardless of what email software a person uses for their email, they are guaranteed that it works with Digital Certificates.
This realization solved most if not all of the Board’s issues, all they required now was the Certificates themselves. To do this, the existing Traditional CA [4] system had to be migrated to Digi-CA™ using three simple steps:
By exporting all of the Digital Certificate data, and user information, from the Traditional CA, this data can be imported directly into the Digi-CA™ Service system. By doing this, the Traditional CA can be shut down immediately because Digi-CA™ is capable of managing multiple Certificates, regardless of the original vendor. There is no loss of service and the total environment continues to operate without interruption.
Most CAs reissue Digital Certificates each year and revoke the previous year’s Certificates in the process. This Certificate Renewal Process is an ongoing component of the CA environment.
Working with the Certificate Policy for validating users, the Digi-CA™ system simply switches the older Digital Certificate for the new Certificate during the Renewal Process. The end user experiences no interruption of use and often can be completely unaware that the Legacy CA has been replaced by the new Digi-CA™ system.
In some cases the Traditional CA is too inflexible to use either of the previous migration methods and the simplest solution is to revoke all of the older Certificates and issue the new ones as required.
The Renewal Change Over process was used in this Digi-CA™ Service case. Insurecom used the Certificate Renewal Process to replace the older Certificates with Digi-CA’s™ and migrated from the Legacy CA to complete the process during the course of the year.
There was no service interruption, no loss of access and no ‘down time’ in the process. The resources used in the migration were no more than had been used in the operation of the Legacy CA and the entire environment continued to operate uninterrupted.
The Insurecom system operates more efficiently and uses less human resources than was the case with the Legacy CA.
Insurecom enjoyed the benefits of Digi-CA™ without the usual complications associated with migrating from one system to another. For Insurecom, the decision to migrate was a difficult one, but one that reaped significant rewards.
It is worth noting that in addition to the time and human resource savings afforded to Insurecom as a result of migrating from the Legacy CA to Digi-CA™, the annual subscription costs are lower too!
Links:
[1] https://www.digi-sign.com/downloads/download.php?id=white-paper
[2] http://www.cio.gov.bh
[3] http://www2.digi-sign.com/digi-tasc
[4] http://www2.digi-sign.com/certificate+authority/traditional+ca