


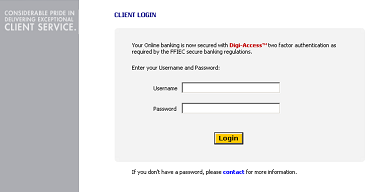
 [1]Online Banking Example [1]
[1]Online Banking Example [1] One-Time-Password [OTP] Tokens |
 Digi-Access™ Certificates |
In Favour of OTPAgainst using OTP |
In Favour of Digi-Access™Against using Digi-Access™ |
Perhaps you don't have any plans to increase the security access to your online application. Budgetary restrictions may be another issue. So why not let your users decide if they want this security 'add-on'.
We have a simple programme for this too:

The Man-in-the-Middle [MITM] attack intercepts a communication between two systems. For example, in an http transaction the target is the TCP connection between client and server. Using different techniques, the attacker splits the original TCP connection into 2 new connections, one between the client and the attacker and the other between the attacker and the server, as shown in figure 1. Once the TCP connection is intercepted, the attacker acts as a proxy, being able to read, insert and modify the data in the intercepted communication.
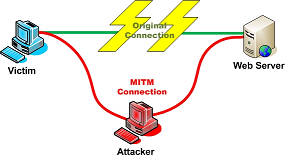
This attack can occur, even when One-Time-Password [OTP] tokens are in use. The MITM system simply takes the password as it is issued and uses it to gain access to the online system.
Using Digi-Access™ the Man-in-the-Middle attack is not possible because it uses completely different 'key-pair' technology. The server must receive the public key from the Digi-Access™ certificate and the MITM server cannot have the correct configuration to request this (because it is not part of the 'trust-link' that is an integral part of the Digi-Access™ 'key-pair' technology). Therefore the MITM attack will fail to work when the user has a Digi-Access™ certificate.
Some systems Administrators will refer to the security bug within Microsoft© CryptoAPI [10]. This security bug means that for users that have Internet Explorer© browsers, it is possible for hackers to break into the Microsoft© Certificate store and misappropriate the Digi-Access™ certificate (this does not apply to Mozilla browser users).
However, this security concern is irrelevant if the user has a properly configured PC with regular Microsoft© updates enabled. As most responsible users do have Microsoft© updates enabled (and you can provide help pages to highlight the issue), then this is as much a risk to end users as protecting their computers from viruses.
Links:
[1] http://www2.digi-sign.com/demos/instructions/online+banking
[2] http://www2.digi-sign.com/cell-otp
[3] http://www2.digi-sign.com/support/digi-access/user/mitm
[4] http://www2.digi-sign.com/digi-access/distribute
[5] http://www2.digi-sign.com/digi-access/website
[6] http://www2.digi-sign.com/support/digi-access/user/mitm#cryptoapi
[7] http://www2.digi-sign.com/demos/digi-access#bank
[8] http://www2.digi-sign.com/quote/digi-access
[9] http://www2.digi-sign.com/arp
[10] http://www.microsoft.com/technet/security/bulletin/ms02-050.mspx