

![]() [1] Digi-CA™ is the complete Certificate Authority [2] [CA] system for organisations that would like to own and manage their CA inside the organisation. The CA issues the Digital Certificates [3] that are used for two factor authentication [4], electronic signatures, device-to-device authentication, National ID Cards [5], Machine Readable Travel Documents [MRTD [6]], smart cards and ID Cards [5] and many other network, online, web and physical security environments.
[1] Digi-CA™ is the complete Certificate Authority [2] [CA] system for organisations that would like to own and manage their CA inside the organisation. The CA issues the Digital Certificates [3] that are used for two factor authentication [4], electronic signatures, device-to-device authentication, National ID Cards [5], Machine Readable Travel Documents [MRTD [6]], smart cards and ID Cards [5] and many other network, online, web and physical security environments.
Combining the consulting and professional services offered in the Digi-CAST™ [8] methodology with Digi-CA™ can meet all national and international standards [9] such as: Common Criteria, Sarbanes Oxley, SB 1386, BS 7799-3:2006, ISO 17799, FFIEC, HIPAA, ACSI 33, 1999/93/EC, ANSI, CWA 14167-1, ETSI 101 456, EAL, FIPS, RFC, ICAO, MRTD, CONOPS, ALGO, Gramm-Leach Bliley and many other compliance [9] and certification [9] requirements.
Small and medium sized businesses, large corporate, government, local government, Trust Centres [10], statutory bodies, security companies or any enterprise that wants to use Digital Certificates, should carefully examine the true benefits of using this radical new technology.
The Digi-CA™ system can issue, revoke, suspend and re-sign x.509v3 Certificates. The end user information and certificate request is entered through the web-based Registration Authority [RA] called the Digi-CA™ Control Centre. It is the Digi-CA™ Control Centre that is used to control all day-to-day administrative functions. Time stamping, Online Certificate Status Protocol [OCSP] [11], customized Certificate Revocation Lists [CRLs] and many other options can be incorporated into Digi-CA™ on request.
The Digi-CA™ suite of CA systems offers the following benefits:
This online manual is the resource for the many different users of Digi-CA™ system and is suitable for both the technical and non-technical reader.
![]() [13] Multiple customized Root Certificates, Intermediate Root Certificates and EU Qualified Certificates can also be catered for. Every aspect of the Digital Certificate including Certificate fields can all be customized to meet any x.509 standard requirement.
[13] Multiple customized Root Certificates, Intermediate Root Certificates and EU Qualified Certificates can also be catered for. Every aspect of the Digital Certificate including Certificate fields can all be customized to meet any x.509 standard requirement.
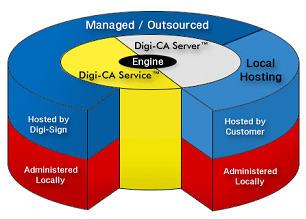
Whether your requirement is for a simple to use and operate CA that is installed as software inside the organization or a totally outsourced service, Digi-CA™ can meet your precise requirements. Highly customized and complex CA environments and even a certified Trust Centre [10] that complies with international standards [9] can be built-to-order using Digi-CA™ Server. And you can also have almost all these same functionalities, no matter how complex, delivered as a service from outside the organization using the Digi-CA™ Service. No matter how it’s delivered, Digi-CA™ is the most flexible, efficient and cost effective CA system for you.
Digi-CA™ can be delivered exactly to your requirements. You can choose to have Digi-Sign do everything for you and ‘Fast Track’ your requirements, or you can be proactively involved at whatever level you like.
Implementing a Certificate Authority is not a ‘one size fits all’ project. Your requirement might be for a few hundred users with exceptionally high security parameters or you could be looking to authenticate several million hardware devices. The commercial organization’s requirements are typically related to cost, benefit, risk and return whilst the government project is more concerned with statutory requirements, IT standards and compliance [9].
No matter how small or large your requirement, you’ll have restrictions on what your current environment can cope with; availability of staff; budgetary constraints and other parameters within which you must choose the correct CA for your organization. You may want to be very ‘hands on’ at every stage of the project and even want to conduct some of the integration and even programming or you may decide you want us to do everything for you. Just as Digi-CA™ is totally flexible, so too is the Digi-Sign approach.
![]() [13] AACD™ System [14] ‘Fast Track’ is exactly as it sounds, you want everything done as quickly as possible and you want the professionals to do it for you. This is a total ‘turn key’ approach where we take your instructions, document them and deliver the entire solution back to you in the shortest possible time. Once the Digi-CA™ is delivered, you nominate personnel within your organization to take responsibility for it and we support them in the background.
[13] AACD™ System [14] ‘Fast Track’ is exactly as it sounds, you want everything done as quickly as possible and you want the professionals to do it for you. This is a total ‘turn key’ approach where we take your instructions, document them and deliver the entire solution back to you in the shortest possible time. Once the Digi-CA™ is delivered, you nominate personnel within your organization to take responsibility for it and we support them in the background.
This is where we not only ‘Fast Track your requirements through to delivery but actually assume responsibility for the total management of your CA environment for as long as you need us too.
Total Trust Management™ [TTM™] [15] is a unique offering from Digi-Sign (although some try to copy it) and it means that you Trust us to Totally Manage the Digi-CA™ for you. TTM™ is much more than a dedicated telephone support line, it’s a service where Digi-Sign personnel effectively work for you. We ensure that the CA technology is introduced to the end users with the minimum of fuss. All you do is agree how you want us to operate the Digi-CA™, and we do everything for you. It’s a bit like travelling First Class.
75% of our customers use TTM™ in the first year, at least, so that they can see how we do everything and then learn by watching us, see section 3.3 for more details.
You call us, we document your requirement, you sign the order and then we build, box and either ship it to you for installation or we host it for you so that it only needs to be activated.
If your requirements include integration work or customization, this is scheduled and delivery is subject to Production scheduling and all of this is agreed in advance.
The success or failure of any project can normally be traced back to the start, where bad planning will be found. This poor initial planning will either be as a result of bad management and leadership and to a lesser extent, the selection of technically inexperienced personnel. That is why Digi-Sign insists that no matter how much 'trouble' the project encounters en route, if it is properly planned initially, it will succeed.
Digi-CAST™ [8] is factual, high-quality, Digital Certificate and CA advice from experienced personnel that can show you how your CA should be implemented, integrated and maintained. The C-A-S-T method was pioneered by Digi-Sign in 2005 after many years of developing and deploying CAs around the world.
![]() [16] The Digi-CA™ system is a complete system containing all of the necessary Operating System [OS], modules, directories and engines required to operate a fully functional CA system.
[16] The Digi-CA™ system is a complete system containing all of the necessary Operating System [OS], modules, directories and engines required to operate a fully functional CA system.
Digi-CA™ has been designed by some of the foremost experts in Internet Application Security. All modules are contained in one Linux / Unix based system. Specific care has been taken in the design of Digi-CA™ to ensure that no outside intrusion can take place and that all the private Keys for the Digi-CA™ are secure (if they are not stored on a HSM).
To ensure the uniqueness of the keys in the Digi-IDs™, Digi-CA™ uses its own entropy system. Digi-CA™ can create Key lengths up to 9192-bits. It can also support all key ciphers and signature algorithms.
Depending on the level of security required, Administrators must be authenticated by either a smart card [Digi-Card™], a USB Tokens [Digi-Tokens™] and/or a biometric reader.
The entire Digi-CA™ system infrastructure is formed mainly around x.509 certificates, produced with accordance to the internationally recognized RFC 2459 standard and is maintained in accordance to the same internationally recognized RFC 3647 standard.
The design of a typical x.509 Certificate includes the following cryptographic algorithms that are approved for commercial use by governments and related agencies and institutions around the world.
The Signature Algorithm uses RSA and DSA and as these algorithms are always used in conjunction with a one-way hash function, the following hash functions can be applied:
![]() [16] The Signature Key generation algorithms use RSA and DSA (Digi-CA™ Server only).
[16] The Signature Key generation algorithms use RSA and DSA (Digi-CA™ Server only).
The x.509 certificate can be used for many purposes, such as: electronic signature, two factor authentication [4], client authentication, email signing and encryption and many other applications.
The most common and most frequently used purposes can be included using further layers of security protocols and cryptographic algorithms, the most common of which are:
Digi-SSLs™ and Digi-Codes™ require browser compatibility. Digi-IDs™ require browser compatibility and email software compatibility when being used for Digi-Mail™ [18]
The following is a list of browsers that are compatible with Digi-SSLs™, Digi-Codes™ and Digi-IDs™:
The following is a list of browsers that are compatible with the Digi-IDs™ used for Digi-Mail™:
![]() [16] Number of certificates: 200 up to 200,000,000
[16] Number of certificates: 200 up to 200,000,000
Production speed: Without HSM up to 5,000 1024-bits Digi-IDs™/hour
With HSM up to 10,000 1024-bits Digi-IDs™/hour
Key length: Root and Intermediate Certificates 9196-1024 bits
Digi-IDs™ 1024-2048 bits
Symmetric Keys 56 to 256 bits
Key validity: Root Key 1 to 25 years
Intermediate Keys 1 to 10 years
Client Keys 1 to 10 years (as per Digi-ID™ Policy)
Key storage: Root Key off-line and stored in several separate pieces Intermediate (signing) keys access through HSM, biometric client certificates [3], smart card or USB tokens
Cryptographic Ciphers: AES, Blowfish, CAST5, DES, 3DES, IDEA, RC2, RC4, RC5 and RSA
Signature Algorithms: MD2, MD4, MD5, MDC2, SHA1 (DSSI) and RIPEMD-160
Entropy: 2127
![]() [16] The authentication, privacy and integrity of the Digi-ID™ is governed by several factors:
[16] The authentication, privacy and integrity of the Digi-ID™ is governed by several factors:
![]() [16] At the heart of every Digi-CA™ are at least one Root Key(s) or Root Certificate(s) and one Intermediate Root Certificate(s). Every Digi-CA™ Certificate is made from a Public and a Private Key. A Root Key Ceremony is a procedure where a unique pair of Public and Private Root Keys is generated. Depending on the Certificate Policy, the generation of the Root Keys may require notarization, legal representation, witnesses and ‘Key Holders’ to be present. This process is best explained with some examples:
[16] At the heart of every Digi-CA™ are at least one Root Key(s) or Root Certificate(s) and one Intermediate Root Certificate(s). Every Digi-CA™ Certificate is made from a Public and a Private Key. A Root Key Ceremony is a procedure where a unique pair of Public and Private Root Keys is generated. Depending on the Certificate Policy, the generation of the Root Keys may require notarization, legal representation, witnesses and ‘Key Holders’ to be present. This process is best explained with some examples:
Unless the information being accessed or transmitted is valued in terms of millions of dollars, it is probably sufficient that the Digi-CAST2™ Team [8] conduct the Root Key Ceremony within the security of the Digi-CAST2™ Laboratory. The customer may opt to have the Root Key stored on a Luna Card or HSM, but in most cases the safe storage of the Root Key on a CD or hard disk is sufficient. The Root Key is never stored on the Digi-CA™ server.
Example B: Machine Readable Travel Document [MRTD [6]] ID Card or e Passport [20]
This type of environment requires much higher security than a commercial one. When conducting the Root Key Ceremony, the Government or Organization will require rigorous security checks to be conducted on all personnel in attendance. Those that are normally required to attend the Key Ceremony will include a minimum of two Administrators from the organization, two signatories from the organization, one lawyer, a notary and two video camera operators in addition to the Digi-CAST2™ Team.
The actual Root Key-Pair generation is normally conducted in a secure vault that has no communication or contact with the outside world other than a single telephone line or intercom. Once the vault is secured, all personnel present must prove their identity using at least two legally recognized forms of identification. Every person present, every transaction and every event is logged by the lawyer in a Root Key Ceremony Log Book and each page is notarized by the notary. From the moment the vault door is closed until it is re-opened, everything is also video recorded. The lawyer and the two organization’s signatories must sign the recording and it too is then notarized.
Finally, as part of the above process, the Root Key is broken into as many as twenty-one parts and each individual part is secured in its own safe for which there is a key and a numerical lock. The keys are distributed to as many as twenty-one people and the numerical code is distributed to another twenty-one people.
Important Note: Example A and B are at opposite ends of the security spectrum and no two environments are the same. When considering the Root Key Ceremony, the Digi-CAST1™ Team [8] of professional advisors can assist you in deciding on the most efficient level of security to reflect the level of protection required.
![]() [16] A standard process for issuing a Digi-ID™ [21] Certificate involves the following stages:
[16] A standard process for issuing a Digi-ID™ [21] Certificate involves the following stages:
![]() [16] Digi-IDs™ are requested by the end user at the Enrollment Application Form or by the Administrator (on the users behalf) using the Digi-CA™ Control Centre.
[16] Digi-IDs™ are requested by the end user at the Enrollment Application Form or by the Administrator (on the users behalf) using the Digi-CA™ Control Centre.
From the Digi-CA™ Control Centre, all Digi-ID™ [21] requests are either entered into the database on an individual basis, using a batch upload file or automatically, depending on the Class of Digi-CA™ you are using. Similarly, all requests for Digi-IDs™ are accepted, rejected or deferred either manually or automatically, depending on the Class of Digi-CA™ you are own, using the RA Control Centre of the Digi-CA™.
The Digi-CA™ system automatically generates a Certificate Signing Request [CSR [22]] if the requesting party did not already supply one and then generates the Digi-ID™. The generation is done in batch processes according to schedules set in crontab. The default is to run the process every hour.
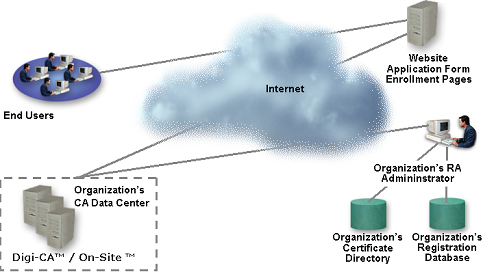
After generation, the Digi-ID™ is activated at the users PC or it can be delivered by email as a .p12 file. Storage of the Digi-ID™ can be on the PC or any suitable media such as a Digi-Card™ or a Digi-Token™. Similarly, the Administrator can pre-install the Digi-ID™ on the Digi-Card™ or Digi-Token™ prior to dispatch. This is particularly convenient where the Administrator wants ‘Zero Touch’ at the user’s location.
The method of distribution is set in the database at the time of the validation. The default is that Digi-IDs™ are distributed over the web, with the Digi-IDs™ holder getting an email containing a one-time password needed to pick it up.
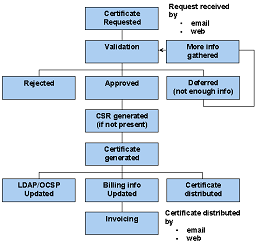
If the billing module is installed, this module is updated with information and then passed on to your billing system.

The following are the steps for issuing a Digi-ID™ Digital Signature:
The following are the steps for re-issuing/replacing an existing Digi-ID™ Digital Signature:
Typically the renewal process is simply a case of presenting the previous Digi-ID™ and a new one is issued to replace it

The Digi-CA™ [23] Certificate Authority [CA] system (that issues the Digi-ID™ end user digital signatures) can issue thousands of digital signatures every hour. This 'endless' capacity means that getting Digi-ID™ digital signatures to the end users can occur as quickly as your environment demands.
How the Digi-ID™ digital signatures are issued is set by the 'Enrolment Policy [24]'. The options within the Enrolment Policy are designed to be very flexible. They can be customised to meet almost any requirement with many different settings and combinations. The three basic options are:
Issuing the Digi-ID™ digital signatures is either a one or two stage process. Either the user receives an email inviting them to apply for their digital signature, or they are referred from an existing online site/system to the Digital Signature Application form.
However the user is prompted to get their digital signature, in the first stage, the Digi-CA™ Inviting 'action' requires the end user 'reaction' (completing an application form). In the second stage, the Digi-CA™ Approving 'action' requires the end user 'reaction' (activating the digital signature) and this completes the process. It is best understood as follows:
As stated, because the Enrolment Policy is very flexible, there are many different ways to invite and approve end users digital signatures. The following is a sample issuing process only. You may wish to include other options, as required.
Stage One 'Digi-CA™ Action' - Inviting Digi-ID™ Digital Signature Applications
Using the Digi-CA™ RA Management Console interface, the Administrator uploads a .CSV batch file inviting [25] as many users as required.

Stage One 'User Reaction' - Completing Enrolment Form
The Digi-CA™ system sends an email to each end user with a unique link to the Digi-ID™ digital signature enrolment form. Using the link provided in the email, the end user then completes the Digi-ID™ digital signature enrolment form.
Note:- this is the default Digi-ID™ End Entity Digital Signature Enrolment Form. This form uses basic HTML programming that can be altered [26] to match your specific design requirements.

Once the end user completes all the fields and submits the enrolment form to the Digi-CA™ system, the Administrator is notified. The Administrator then approves [24] each end user application using the Digi-ID™ Digital Signature Authorization Panel.
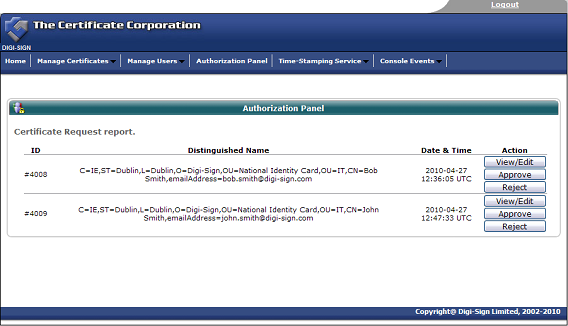
Stage Two 'User Reaction' - Activating the Digi-ID™ Digital Signature
Assuming the Administrator approves the application, the Digi-CA™ system sends a new email to the end user advising them that their application has been approved. Using the link provided in the email, the end user then activates [27] the Digi-ID™ digital signature and this completes the issuing process.
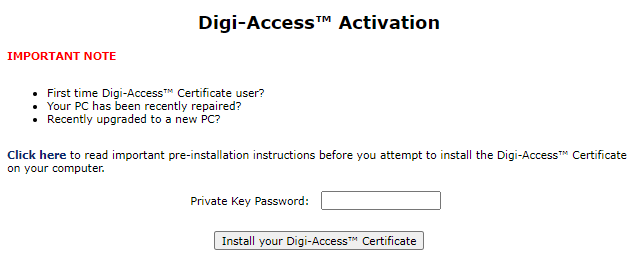

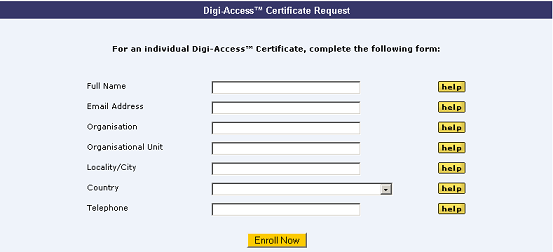
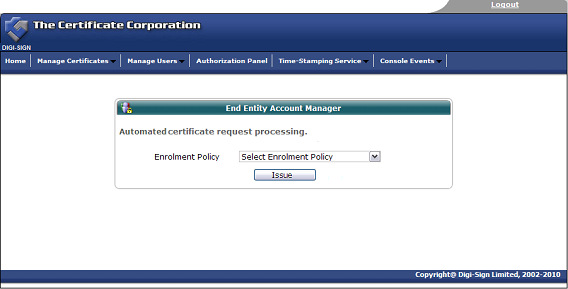
Once the enrolment form is completed and submitted by the end user, the Enrolment Policy enforces how the application is handled by the Digi-CA™ system. Learn more about the Enrolment Policy [24] options or browse the other pages below.

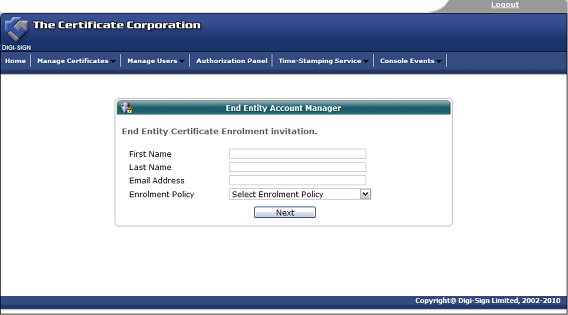

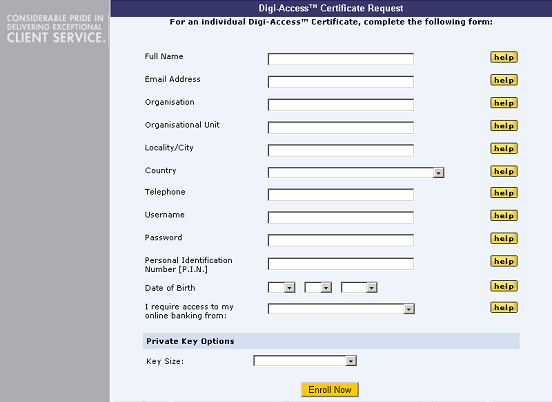
Once the invitation is issued, the end user must complete the enrolment form. View customised enrolment [26] forms or browse the other pages below.

The Enrolment Policy for Digi-ID™ controls the entire certificate issuing process. Enrolment Policy is set by the Certificate Policy [CP] for the Digi-CA™. This is a specialist subject and requires experienced knowledge of Certificate Authority [CA] systems and Public Key Infrastructure [PKI]. Keeping this complex topic simple, there are three basic options for Enrolment Policy:


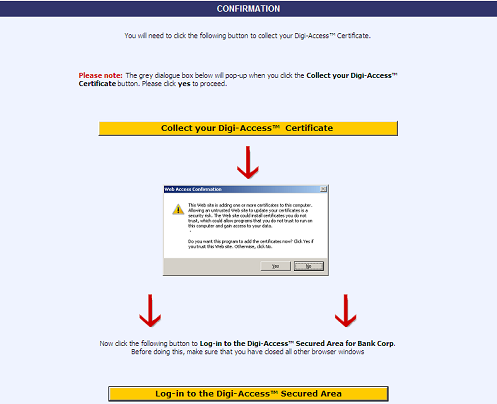
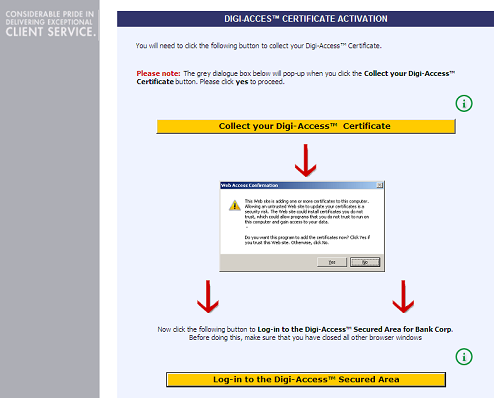
Once the enrolment form is completed and submitted by the end user, the Enrolment Policy enforces how the application is handled by the Digi-CA™ system. Learn more about the Enrolment Policy [24] options or browse the other pages below.

|
Microsoft® Internet Explorer® |
Mozilla/Firefox/Safari |
|
1. To view your Digi-ID™ digital signature in Microsoft® Internet Explorer®, use the Tools menu (you may have to press the 'Alt' button on your keyboard to view this menu) and then select Internet Options 2. In the Internet Options dialog box, select the Content tab and then click the Certificates button 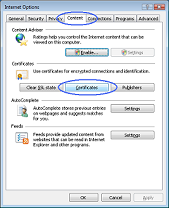 3. In the Certificates dialog box, select the certificate/digital signature you wish to examine and then click the View button 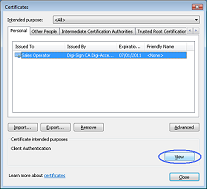 4. The chosen digital signature will be displayed where you will be able to see:
 |
1. To view your Digi-ID™ digital signature in Mozilla, Firefox or Safari, use the Tools menu and then select Options 2. In the Options dialog box, select the Encryption tab and then click the View Certificates button 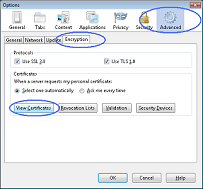 3. In the Certificate Manager dialog box, select the certificate/digital signature you wish to examine and then click the View button  4. The chosen digital signature will be displayed where you will be able to see:
 |


|
Microsoft® Internet Explorer® |
Mozilla Firefox |
|
1. To view your Digi-ID™ digital signature in Microsoft® Internet Explorer®, use the Tools menu (you may have to press the 'Alt' button on your keyboard to view this menu) and then select Internet Options 2. In the Internet Options dialog box, select the Content tab and then click the Certificates button  3. In the Certificates dialog box, select the certificate/digital signature you wish to examine and then click the View button  4. The chosen digital signature will be displayed where you will be able to see:
 5. Once you have viewed and confirmed this is the Digi-ID™ digital signature you wish to remove, return to the Certificates dialog box, select the certificate/digital signature and click the Remove button |
1. To view your Digi-ID™ digital signature in Mozilla Firefox, use the Tools menu and then select Options 2. In the Options dialog box, select the Encryption tab and then click the View Certificates button  3. In the Certificate Manager dialog box, select the certificate/digital signature you wish to examine and then click the View button  4. The chosen certificate/digital signature will be displayed where you will be able to see:
 5. Once you have viewed and confirmed this is the Digi-ID™ digital signature you wish to delete, return to the Certificate Manager dialog box, select the digital signature and click the Delete button |
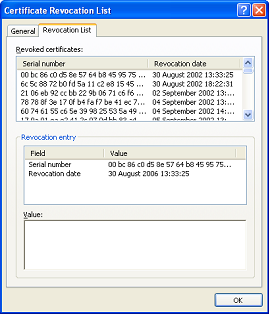
![]() [16] All Digi-ID™ revocations are initiated either by the user or by the Administrator. Revocations are required for a number of reasons, for example:
[16] All Digi-ID™ revocations are initiated either by the user or by the Administrator. Revocations are required for a number of reasons, for example:
1. the user has lost the PC or media where the Digi-ID™ was stored.
2. the user no longer has any affiliation with the organisation that issued the Digi-ID™.
3. the user changed position in the organisation and no longer has any right to the Digi-ID™.
4. the Administrator believes a Digi-ID™ has been misused.
5. the Administrator believes a Digi-ID™ used to misrepresent the organization that issued the Digi-ID™.
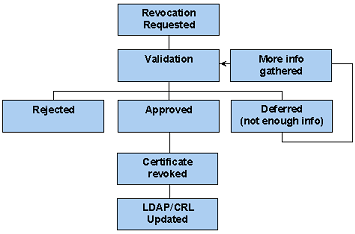
The following sub sections detail how Revocation requests are made and the resulting actions and uses for this important feature.
The following diagram explains the events that occur within the Digi-CA™ and how a revocation request is executed:
![]() [16] The digital signature [3] and message encryption implementation on email messages is achieved by mechanisms implemented directly in the email client software and that follows the S/MIME standard.
[16] The digital signature [3] and message encryption implementation on email messages is achieved by mechanisms implemented directly in the email client software and that follows the S/MIME standard.
Both S/MIME message encryption and Digital Signatures are based on encryption technologies. Message body encryption creates a completely unreadable message body and Digital Signature. The diagram below shows how the encryption process generates a one-time Symmetric Key (also called a Session Key) that encrypts the message body.
The Symmetric Key is then encrypted with each recipient’s Public Key so that only the recipient can decrypt the Symmetric Key. The message is then sent. On the recipient end, the Private Key is used to decrypt the Symmetric Key, which is then used to decrypt the message. This process is transparent to the user and is performed with no interaction between clients. Symmetric encryption is much faster than asymmetric encryption. The reason is because symmetric encryption encrypts the data (message body) in bulk.
The following diagram describes how email encryption is achieved:
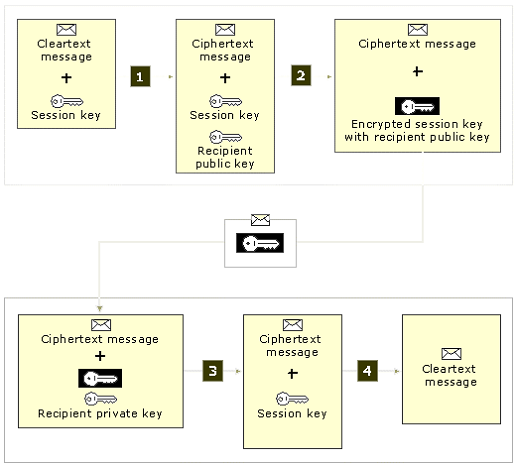
The diagram illustrates the message encryption and decryption process. The four main steps detailed in the illustration are as follows:
2. Session Key is encrypted with recipient’s Public Key.
3. After encrypted message is received, recipient decrypts Session Key with the recipient’s Private Key.
4. Message is decrypted with Session Key.
When you add a Digital Signature to a message, a hash value of the message contents is computed. User Keys aren’t used to compute the hash value and the hash doesn’t identify anyone. The hash is only a small, unique digital fingerprint of the message. This hash value is then encrypted with the sender’s Private Key, and can be decrypted with the Public Key found in the sender’s certificate.
The recipient decrypts the original hash value with the sender’s Public Key, which might be sent with the signed message or can be found in the sender’s certificate. Your client verifies signatures. For encrypted messages, it decrypts the message first. The client computes a new hash value based on the text received and compared to the original hash value. If they match, you can trust the content’s integrity and the sender’s identity.
The Digi-CA™ system can create multiple instances of unique CAs in a single Digi-CA™ system. The Digi-CA™ model imposes delegation of trust downwards from CAs to their Subordinate Certification Authorities [Sub-CAs]. The same Digi-CA™ system also enables any CA or Sub-CA to be signed or cross signed by an external third party CA. And any number of CAs can have any number of cross signed Sub-CAs. As a result of this design principal, the Digi-CA™ model for trust levels increases towards the highest authority. This type of arrangement facilitates easy deployment and scalability of any PKI requirement from the smallest to the largest.
Digi-CA™ replaces older Traditional PKI [28] technology and CA systems using the latest in CA technology. With Digi-CA™, all of the complexities and onerous technical overhead that were required by Traditional CAs have been simplified to a ‘user-friendly’ and usable level. Digi-CA™ can also be ‘dropped’ on top of these Traditional CA environments and seamlessly migration [29] the older system’s users into this more modern and flexible replacement.
At its core, the Digi-CA™ system works on Unix/Linux operating systems and was written using C programming language for the low application level and PHP at the high level. The design philosophy was that the simplicity of the complete system should also be capable of large scale enterprise or national CA system, so that it could be delivered and scaled, easily. This critical design component has not changed in the past seven years.
To enable this, the modular design of Digi-CA™ allows easy and flexible service distribution to multiple numbers of servers, thus achieving high level of service availability. Each system component [30], for example the Cryptographic Service Provider [CSP], and all system modules [31] can be installed and operated on a multiple number of servers that can further be configured in a variety of high availability modes such as fail over, cluster and load balanced.
In each case, software or hardware high availability solution can be independently implemented to achieve best option suitable for your environment. And even more importantly, Digi-CA™ has the ability to scale, easily and without interrupting the live production environment at any stage during the life of your system.
The Digi-CA™ System can issue, revoke, suspend, de-suspend and re-sign x.509v3 Digital Certificates. Time-Stamping, Online Certificate Status Protocol [OCSP], Certificate Revocation Lists [CRLs] and many other features of a PKI system can be activated as required using the administration console of the system.
End user information and certificate requests are entered through the web based Registration Authority [RA] Management Console [32]. This powerful RA Management Console manages the entire Certificate Life cycle. Basic Certificate issuing and revocation by Operatives can be further delegated through a basic and modified RA Management Console interface called the Digi-CA™ Control Centre. It is the Digi-CA™ Limited RA [LRA] - Control Centre [33] that is used by the RA Operator on a day-to-day basis.
Unlike any other CA system in the market, Digi-CA™ is specifically designed to easily migrate any other existing PKI system. By design Digi-CA™ [23], as a entirely self dependent system, allows its easy migration from one data centre to another in an almost seamless manner. The transfer can be accomplished either physically through hardware transportation or by secure software and data migration whereby all software and database data is securely migrated in an encrypted format from one location to another.
The key features necessary for running your existing framework PKI infrastructure are already embedded in the Digi-CA™ System as standard. It additionally offers a much wider scale of possibilities in using PKI throughout your entire organisation. Where Traditional CA [28]s offer most modules as add-ons (and at additional cost), Digi-CA™ offers these 'as standard' and provides alternative key generation, certificate enrolment and certificate installation features, with policy based controls, in compliance with most current commercial and open standards. Digi-CA™ also supports a large variety of third party software and cryptographic hardware devices such as smart cards, USB tokens and Hardware Security Modules [HSMs].
In conjunction with your existing on line applications and PKI infrastructure, features provided by Digi-CA™ can introduce and add enhanced support and security to inbound and outbound email exchange communications through the use of S/MIME. Also, web server and web client strong and multi factor authentication using Public Key Certificates and SSL/TLS communication protocols, signing of application code, authentication of network routers, firewalls and Virtual Private Network [VPN] devices and many other business-to-client and business-to-business PKI aware solutions too.
To migrate your system, the Digi-CAST™ [36] methodology, you will experience a smooth transition process from your current PKI framework. The Digi-CAST™ Team consists of highly qualified, expert IT engineers responsible for providing analysis, planning and implementation services to meet the your requirements and allows you to completely 'off load' all activities in these areas. The Digi-CAST™ method will provide for a detailed migration plan that outlines all phases of the migration process and provides estimated delivery schedules for each phase of the project, leaving no space for omissions or lengthy implementation delays by providing best Digi-CAST™ guaranteed quality of service.
![]() [16] The Digi-CA™ system is built in several modules. Each module communicates with other modules either directly through a programmable socket interface or an API interface. The system design is such that no access is allowed to the system Certificate Engine core level, except through the web based interface panel or through SSH for power low level administrators only [super users].
[16] The Digi-CA™ system is built in several modules. Each module communicates with other modules either directly through a programmable socket interface or an API interface. The system design is such that no access is allowed to the system Certificate Engine core level, except through the web based interface panel or through SSH for power low level administrators only [super users].
There is one operating system and four principle modules in the Digi-CA™ and how they are implemented for your requirements depends on the Certificate Policy:
As an option the following sub-systems can also be installed:
The above options are available subject to consultation and are listed here for indicative purposes only.
Digi-CA™ has been designed and is built for Unix / Linux compatible operating system platforms. Typical installations use FreeBSD 5.4+ Unix or a RedHat Enterprise Linux based operating system.
The main module of the system is the Digi-CA™ Certificate Engine core that is used for the creation and revocation of Certificates based on the system Certificate Policy. It uses a direct interface to the Digi-CA™ Information Database that contains information about all Digi-ID™ [21] Certificate holders and the issued (or pending to be issued, suspended or revoked) Certificates. Output from the Digi-CA™ Certificate Engine core is directed to:
The Digi-CA™ Certificate Engine core is designed so that no Administrator intervention is necessary. Using a daemon server, important maintenance tasks occur automatically.
![]() [16] The Digi-CA™ This module is used for storing:
[16] The Digi-CA™ This module is used for storing:
The database is SQL based and by default the system is installed with MySQL database server. At an additional cost, the Administrator can define what database to use (PostGRE SQL, Oracle®, DB2®, SQL Server®, Websphere®, etc).
Based on information stored in the database, the system generates requests for creation, suspension (if enabled) and revoking of Digi-ID™ [21] certificates to the Digi-CA™ Certificate Engine core.
The Digi-CA™ Directory stores Digi-ID™ Certificates and user data according to current international RFC standards. The schemas used are core, cosine and internetperson. The schemas are stored in a directory. Access to the directory is available through an LDAP compatible client.
The Digi-CA™ Control Centre is the Administrators’ interface for controlling the day-to-day operation of the Digi-CA™ system. The Digi-CA™ Control Centre provides all of the deployment and life cycle management functions of the Digi-IDs™ and any other Digital Certificates [3] the system issues. One or more Administrators can manage the Digi-CA™ Control Centre. Depending on the level of security required, Administrators must be authenticated using Digi-Access™ [40], Digi-Card™, Digi-Token™ and/or a biometric reader.
Digi-CA™ uses the x.509 standard Certificate Revocation List [CRL] format so that Digi-ID™ information can be made publicly available at a designated web address. This is the repository for all issued Digi-IDs™ and enables integration of Digi-IDs™ into third party or custom applications an easy task.
Recent ANSI, ETSI and ICAO guidelines have recommended the use of Online Certificate Status Protocol [OCSP] [11] for certain environments. Offering OCSP as a service can cause considerable traffic on your network and should only be considered where there is a statutory or compliance [9] requirement.
In all other cases, the CRL service is the preferred method of communicating the status of the Digi-ID™.
![]() [16] After the environment has been prepared and the Certificate Policy (and in the case of Xg the Digi-Sign Certificate Practice Statement [12]) agreed, the software is configured. Software configuration may be as simple as designing the SSRoot & Intermediate Certificates or it can be a complex environment requiring compliance and standards, integration and application development.
[16] After the environment has been prepared and the Certificate Policy (and in the case of Xg the Digi-Sign Certificate Practice Statement [12]) agreed, the software is configured. Software configuration may be as simple as designing the SSRoot & Intermediate Certificates or it can be a complex environment requiring compliance and standards, integration and application development.
A simple configuration can be completed in 2-3 days with full-scale projects running into several months of configuration, documentation and implementation. The following descriptions are provided here as guidelines only:
Configuration Time: 2 Days
Configuration Time: 25 Days
Configuration Time: 5 Days
Configuration Time: 90+ Days
Once the software is configured, installation of the Digi-CA™ can begin. Subject to project scheduling, and Digi-CAST2™ [8] availability, the following are indicative installation times. You should also note that the installation also includes Administrator and RA training:
As Digi-CA™ Xg is usually a highly customized setup [41], the following sections focus on the installation of the Xs and Xp environments for Digi-CA™ Server and Digi-CA™ Service.
![]() [16] Ordering and operating a Digi-CA™ Service Xs or Xp couldn’t be simpler. All you require is a single internet enabled PC with Internet Explorer 5.5+ and the Digi-CAST2™ Team [8] will either send you a Digi-Card™ and smart card reader or a Digi-Token™ USB token that enables you to access the Service or you will be permitted to store the Administrator’s Digi-ID™ [21] in the Certificate Store of the PC.
[16] Ordering and operating a Digi-CA™ Service Xs or Xp couldn’t be simpler. All you require is a single internet enabled PC with Internet Explorer 5.5+ and the Digi-CAST2™ Team [8] will either send you a Digi-Card™ and smart card reader or a Digi-Token™ USB token that enables you to access the Service or you will be permitted to store the Administrator’s Digi-ID™ [21] in the Certificate Store of the PC.
Whoever logs into the system first is assigned PRIMARY Administrator status with access to all areas and functions of the system. The PRIMARY can invite other Administrators onto the system and may even reassign PRIMARY status to another person.

The Digi-CA™ Service ‘ownership’ is strictly controlled so that the identity of the PRIMARY Administrator is a carefully monitored process. Once the identity of this Administrator is Validated, they are invited to enroll for the Administrator’s Digi-ID™ and this used as two factor authenticated access to the Service. The first time this Administrator logs into the system, they must agree to the Terms & Conditions of the service by clicking the ‘I Agree’ log in button on the index page (see Appendix V.iii). This acceptance uses the electronic signature capability of the Digi-ID™ to sign the Digi-CA™ Service contract with Digi-Sign before permitting access to the system. All subsequent Administrators, regardless of their status, must also digitally sign the same contract but ultimate responsibility resides with the very first Administrator to access the system.
There are no other hardware, software or contracts required by the Administrators of the Digi-CA™ Service and, subject to the Digi-CAST2™ [8] Production Schedule, they can usually order and receive their required system in a few days.
![]() [16] The Digi-CA™ Server, by nature of the fact that it is installed software (usually at the customer site), is a more involved process with hardware, software, documentation and installation requirements. The basic requirements for every Digi-CA™ Server installation are the same and in most instances, Digi-CAST2™ [8] install the Digi-CA™ Server system on your server(s). As more sophisticated environments arise for Digi-CA™ Server Xp or Digi-CA™ Server Xg, the requirements increase accordingly.
[16] The Digi-CA™ Server, by nature of the fact that it is installed software (usually at the customer site), is a more involved process with hardware, software, documentation and installation requirements. The basic requirements for every Digi-CA™ Server installation are the same and in most instances, Digi-CAST2™ [8] install the Digi-CA™ Server system on your server(s). As more sophisticated environments arise for Digi-CA™ Server Xp or Digi-CA™ Server Xg, the requirements increase accordingly.
The following sections describe the basic requirements for installing the three classes of Digi-CA™ Server and the three main components are detailed in each case:
The Digi-CA™ Server Xs is usually installed on a single server and if the correct internet connection and secure Virtual Private Network [VPN] can be provided to the server, it is possible that the installation of the software can be carried out virtually.
The benefit of this is that it reduces the cost of travel and accommodation. When examining each of the following three sub sections you can consult with the Digi-CAST2™ Team at any time to check configurations and access for you.
These are the minimum suitable conditions for the correct operation of the single server Digi-CA™ Server Xs:
![]() [16] These are the minimum equipment specification for the correct operation of the single server Digi-CA™ Server Xs:
[16] These are the minimum equipment specification for the correct operation of the single server Digi-CA™ Server Xs:
Digi-CA™ Server Xs is supplied complete and ready for total install on the server. There is no requirement for any Operating System [OS] or pre-configuration, whatsoever. In fact, if the Server is not completely free of any OS or software, it must be formatted to return it to its original ‘as manufactured’ state.
During the installation, the Digi-CA™ Server will use versions of the following software that will be hardened and modified by the Digi-CAST2™ [8] Team during their installation work:
The previous list is provided for information purposes only.
These are the minimum requirements for the correct installation of the single server Digi-CA™ Server Xs:
![]() [16] The Digi-CA™ Server Xp is usually installed on two servers and if the correct internet connection and a VPN can be provided to the servers, it is possible that the installation of the software can be carried out virtually.
[16] The Digi-CA™ Server Xp is usually installed on two servers and if the correct internet connection and a VPN can be provided to the servers, it is possible that the installation of the software can be carried out virtually.
The benefit of this is that it reduces the cost of travel and accommodation. When examining each of the following three sub sections you can consult with the Digi-CAST2™ Team [8] at any time to check configurations and access for you.
These are the minimum suitable conditions for the correct operation of the dual server Digi-CA™ Server Xs:
These are the minimum equipment specification for the correct operation of the dual server Digi-CA™ Server Xp:
Digi-CA™ Server Xp is supplied ready for total installation on the two servers. There is no requirement for any Operating System [OS] or pre-configuration, whatsoever. In fact, if the servers are not completely free of any OS or software, they must be formatted to return them to their original ‘as manufactured’ state.
During the installation, the Digi-CA™ [23] will use versions of the following software that will be hardened and modified by the Digi-CAST2™ Team during their installation work:
The above list is provided for information purposes only.
These are the minimum requirements for the correct installation of the dual server Digi-CA™ Server Xp:
![]() [16] The Digi-CA™ Server Xg is completely customizable and can be installed across many servers, even if they are in different locations. A Trust Centres [10] example would use four servers and if the correct internet connection and a VPN can be provided to the server, it is possible that much of the installation of the software can be carried out virtually. However, the Digi-CA™ Server Xg will require at least one site visit from a Digi-CAST™ Team Member [8] to conduct certain specialist tasks.
[16] The Digi-CA™ Server Xg is completely customizable and can be installed across many servers, even if they are in different locations. A Trust Centres [10] example would use four servers and if the correct internet connection and a VPN can be provided to the server, it is possible that much of the installation of the software can be carried out virtually. However, the Digi-CA™ Server Xg will require at least one site visit from a Digi-CAST™ Team Member [8] to conduct certain specialist tasks.
The benefit of using the VPN connection as much as possible is that it reduces the cost of travel and accommodation. When examining each of the following three sub sections you can consult with the Digi-CAST2™ Team at any time to check configurations and access for you.
These are the minimum suitable conditions for the correct operation of the multiple server Digi-CA™ Server Xg:
These are the minimum equipment specification for the correct operation of the multiple server Digi-CA™ Server Xg:
Digi-CA™ Server Xg is supplied ready for total installation on the desired number of servers. There is no requirement for any Operating System [OS] or pre-configuration, whatsoever. In fact, if the servers are not completely free of any OS or software, they must be formatted to return them to their original ‘as manufactured’ state.
During the installation, the Digi-CA™ [23] will use versions of the following software that will be hardened and modified by the Digi-CAST2™ Team during their installation work:
The above list is provided for information purposes only.
These are the minimum requirements for the correct installation of the multiple server Digi-CA™ Server Xg:
![]() [16] Once the Certificate Policy Requirements are documented and available, the project process can begin. The Digi-CA™ project can be sub-divided into five separate undertakings:
[16] Once the Certificate Policy Requirements are documented and available, the project process can begin. The Digi-CA™ project can be sub-divided into five separate undertakings:
The Certificate Policy sets out the system design, RA function and overall workflow of the system and also the Root Certificate(s) and Intermediate Root Certificate(s) design. As explained in the Requirements section of this document, the Digi-CA™ is pre-configured prior to delivery at the customer site.
During the software configuration, the Digi-CAST2™ Team [8] will produce test Root Certificate(s) and Intermediate Certificates(s) for your approval. Again, depending on the Certificate Policy, the actual Root(s) and Intermediate Certificate(s) may be generated prior to delivery. Other workflow and processes may also need to be verified. Finally, all the interfaces for the End User and Administrators can be customized to reflect the organization’s identity and/or local language.
Once the configuration is complete it is compiled, complete with ‘hardened’ Operating System [OS] and software, and delivered on a CD or DVD to the customer site.
At the heart of every Digi-CA™ are at least one Root Key or Root Certificate and one Intermediate Root Certificate(s). Every Digi-CA™ Certificate is made from a Public and a Private Key. A Root Key Ceremony is a procedure where a unique pair of Public and Private Root Keys is generated. Depending on the Certificate Policy, the generation of the Root Keys may require notarization, legal representation, witnesses and ‘Key Holders’ to be present. This process is best explained with some examples:
The Root Certificate is only ever used to sign the Intermediate Root Key(s). After signing this Key(s) the Root Key is 3-DES encrypted and split into a minimum of 4 Key shares that are each stored on 3-DES encrypted smartcard and signed with SHA-1. All Key shares will have a unique password and should be stored separately in different secure locations (bank vault, safety deposit box, attorney’s office, etc). A Key generation log is kept in the system and in a separate physical log.
Important Note: the Root Certificate should not exceed a 25-Year life duration.
The Intermediate Root Certificate is protected by 3-DES encryption and all key shares have unique passwords.
Important Note: the Root Certificate should not exceed a 25-Year life duration.
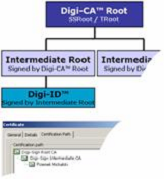
In order to create Digi-IDs™ from the system, at least one self-signed Digi-CA™ Root Certificate must be generated. There is a possibility in the system, depending on ordered options, to create any number of Digi-CA™ Root Certificates and Digi-CA™ Intermediate Roots with different policies and validity. The figure below represents a theoretical relationship between Digi-CA™ Root Certificates. Please consult Digi-CAST1™ before setting up your specific schema.
![]() [16] Digi-CA™ is normally installed by Digi-CAST2™ [8] but in the case of a very basic Digi-CA™ Xs installation (and based on the availability of experienced Network Engineers), you may be capable of installing the Digi-CA™ Xs using its documentation and simple telephone support from a Digi-CAST2™ Team member.
[16] Digi-CA™ is normally installed by Digi-CAST2™ [8] but in the case of a very basic Digi-CA™ Xs installation (and based on the availability of experienced Network Engineers), you may be capable of installing the Digi-CA™ Xs using its documentation and simple telephone support from a Digi-CAST2™ Team member.
The basic Digi-CA™ Xs installation can be completed in three to five days. See Appendix II for two examples of a Single Server and a Dual Server installation. The following is a brief installation schedule:
A Digi-CA™ Xs customized installation may take additional time to configure and a Digi-CA™ Xp or Digi-CA™ Xg installation, using the basic outline as described above, takes longer.
The system activation of the Digi-CA™ is also an integral part of the installation process and is completed, checked and approved by the customer before the Digi-CAST2™ Team leaves the customer site. The online flash presentation of Digi-CA™ [42] explains the benefits in a simple and easy to understand manner.
![]() [16] The Digi-CA™ is probably the most flexible and capable CA system available in the market today. Unlike the other Traditional CA [28]s, Digi-CA™ takes advantage of the many advances in technology over the past seven years and you benefit by getting the most flexible, cost effective and easily integrated and/or migrated [43] CA system you need.
[16] The Digi-CA™ is probably the most flexible and capable CA system available in the market today. Unlike the other Traditional CA [28]s, Digi-CA™ takes advantage of the many advances in technology over the past seven years and you benefit by getting the most flexible, cost effective and easily integrated and/or migrated [43] CA system you need.
The Digi-CA™ still uses Unix in its Certificate Engine core but by using Open Source PKI technology in other modules, Professional Services and upgrade costs are substantially less than those normally associated with the complex and costly modifications of the less flexible Unix Traditional CAs.
In the larger or more complex environment, the organization may require a workflow process to control the use of the Digi-CA™ usage from a cost, security or for general management reasons. The following is an example of a customization currently in use by a Digi-Sign customer for issuing Digi-SSLs™:
This type of customization is not unusual but it does add to the initial cost of deploying a Digi-CA™ system.
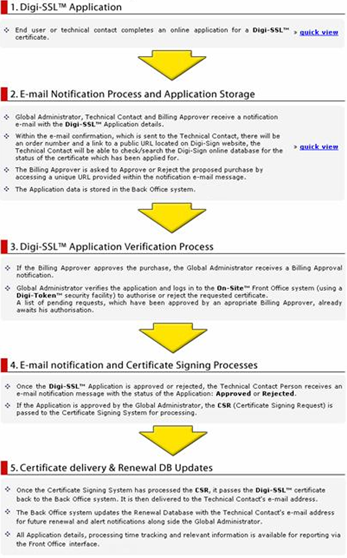
Every aspect of the Digi-CA™ can be automated. Examples of this would be where the Digi-IDs™ are being used to replace Usernames and Passwords for login to a secure website, to replace hardware tokens like SecurID®, to issue Digi-IDs™ for secure email [3] on a closed network or to replace an existing Traditional CA with Digi-CA™.
Using the Digi-CA™ technology and its capabilities, it is possible to use existing LDAPs or other databases such as Oracle®, Active Directory® or any other SQL or flat file format to automate the Digi-ID™ [21] issuing, renewal, suspension and revocation processes.
Using the authentication and validation Certificate Policies from your Traditional CA, Digi-CA™ can migrate users automatically without requiring any IT resources or Administrators’ time.
![]() [16] The entire Digi-CA™ system and all of the interfaces used by the Administrators and users can be completely customized on request. Typical reasons for the graphical changes are for integrating Digi-CA™ into a larger application to make a complete package or the simpler integration of the Digi-CA™ into the organization’s web systems or extranet.
[16] The entire Digi-CA™ system and all of the interfaces used by the Administrators and users can be completely customized on request. Typical reasons for the graphical changes are for integrating Digi-CA™ into a larger application to make a complete package or the simpler integration of the Digi-CA™ into the organization’s web systems or extranet.
The specification of the Digi-CA™ at the time of going to print is available in Appendix IV. All specification updates and technical help files are updated using the online support section of the Digi-Sign website located at www.digi-sign.com [44].
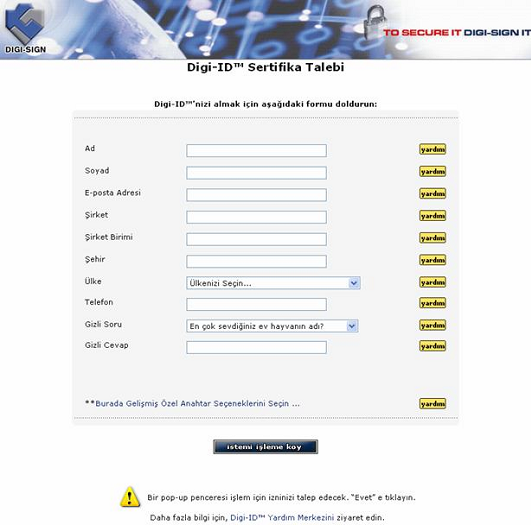
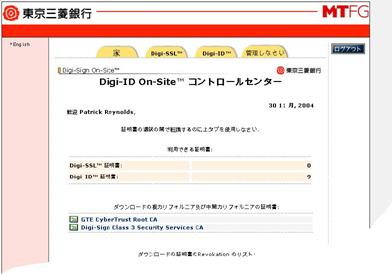
As is the case with sub section 6.5, Digi-CA™ offers the capability to completely localize all interfaces, help files and user screens into your local language(s). This is particularly important to organizations where English is not used. It is also possible to have multiple interfaces with multiple languages for the same system. The following two samples show the Digi-CA™ Control Centre screen in Chinese and the user enrollment screen where users can apply for a [21]Digi-ID™ in Turkish.
The importance of the capability to produce the Digi-CA™ in the local language(s) cannot be over stated. It will result in faster training of the RA personnel and will significantly reduce the Help Desk Support calls (where users are seeking help to with translations from English rather than actual technical support related issues).
It is also possible to have a single Digi-CA™ configured in multiple languages so that different Digi-RAs™ in different countries can use the same Digi-CA™ Control Centre in their native language. Similarly, the users requesting Digi-IDs™ can do so from the same system but again in their native language.
To have your Digi-CA™ localized in your language, the system files and instructions are available in Appendix V.
The following are sample Digi-CA™ installation diagrams, schedule and technical schematics for review.
![]() [45] The following diagram explains the ideal environment for running the Digi-CA™ Server Xs single server system. The Strong Room/locked server cabinet should be a secured with biometric access, ideally with main power supply and a backup power supply with at least one reliable internet connection. Access to this area should be restricted to Administrators only. Two trusted and approved Administrators should be present at all times when the area is being accessed.
[45] The following diagram explains the ideal environment for running the Digi-CA™ Server Xs single server system. The Strong Room/locked server cabinet should be a secured with biometric access, ideally with main power supply and a backup power supply with at least one reliable internet connection. Access to this area should be restricted to Administrators only. Two trusted and approved Administrators should be present at all times when the area is being accessed.
![]() [45] The following technical installation diagram outlines the typical network requirement to run and operate a single server Digi-CA™ Server Xs system without a HSM. Backup server is optional.
[45] The following technical installation diagram outlines the typical network requirement to run and operate a single server Digi-CA™ Server Xs system without a HSM. Backup server is optional.
![]() [45] The following is the time required to install a single server Digi-CA™ Server Xs system without a HSM. Backup server is optional.
[45] The following is the time required to install a single server Digi-CA™ Server Xs system without a HSM. Backup server is optional.
Days Project Part Persons Description
0.5 Server Configurations
0.5 RA Core configuration, Digi-CA™, RA and Public services configuration
0.5 Network connectivity and service accessibility tests
0.5 Root and Intermediate CA Key Ceremony
0.5 Digi-CA™ Administration Training
0.5 RA Training
3 Total Project Installation Time
Note: This installation can be conducted by two personnel, a qualified IT person and a Network Engineer. Alternatively, Digi-CAST2™ can conduct the installation and in some cases this can occur from outside the environment using virtual access (this means there is no on site visit required).
![]() [45] The following is the time required to install a single server Digi-CA™ Server Xs system with a HSM. Backup server is optional.
[45] The following is the time required to install a single server Digi-CA™ Server Xs system with a HSM. Backup server is optional.
Days Project Part Persons Description
0.5 Server Configurations
0.5 Digi-CA™ Core configurations
0.5 Digi-CA™ RA and Public services configuration
1 HSM configuration
0.5 Network connectivity and service accessibility tests
0.5 Root and Intermediate CA Key Ceremony
0.5 Digi-CA™ Administration Training
0.5 RA Training
4.5 Total Project Installation Time
![]() [45] The following technical installation diagram outlines the typical network requirement to run and operate a single server Digi-CA™ Server Xs system with a HSM. Backup server is optional.
[45] The following technical installation diagram outlines the typical network requirement to run and operate a single server Digi-CA™ Server Xs system with a HSM. Backup server is optional.
![]() [45] The following diagram explains the ideal environment for running the dual server Digi-CA™ Server Xp system. The Strong Room/locked server cabinet should be a secured with biometric access, ideally with two power supplies and two separate internet connections from two different providers. Access to this area should be restricted to Administrators only. Two trusted and approved Administrators should be present at all times when the area is being accessed.
[45] The following diagram explains the ideal environment for running the dual server Digi-CA™ Server Xp system. The Strong Room/locked server cabinet should be a secured with biometric access, ideally with two power supplies and two separate internet connections from two different providers. Access to this area should be restricted to Administrators only. Two trusted and approved Administrators should be present at all times when the area is being accessed.
![]() [45] The following technical installation diagram outlines a typical network requirement to run and operate a dual server Digi-CA™ Server Xp system without a HSM. Backup server is optional.
[45] The following technical installation diagram outlines a typical network requirement to run and operate a dual server Digi-CA™ Server Xp system without a HSM. Backup server is optional.
![]() [45] The following is the time required to install a dual server Digi-CA™ Xp system without a HSM. Backup server is optional.
[45] The following is the time required to install a dual server Digi-CA™ Xp system without a HSM. Backup server is optional.
Days Project Part Persons Description
1 Server Configuration
1 RA Core configuration
1 Digi-CA™ Server Failover and Database Replication configuration
1 Digi-CA™ RA and Public services configuration
0.5 Digi-CA™ RA and Public services redundancy configuration
1 Network connectivity and service accessibility tests
0.5 Root and Intermediate CA Key Ceremony
0.5 Digi-CA™ Administration Training
0.5 RA Training
7 Total Project Installation Time
![]() [45] The following technical installation diagram outlines a typical network requirement to run and operate a dual server Digi-CA™ Server Xp system with a HSM. Backup server is optional.
[45] The following technical installation diagram outlines a typical network requirement to run and operate a dual server Digi-CA™ Server Xp system with a HSM. Backup server is optional.
![]() [45] The following is the time required to install a dual server Digi-CA™ Server Xp system with a HSM. Backup server is optional.
[45] The following is the time required to install a dual server Digi-CA™ Server Xp system with a HSM. Backup server is optional.
Days Project Part Persons Description
1 Server Configuration
1 Digi-CA™ Core configuration
1 Digi-CA™ Server Failover and Database Replication
1 Digi-CA™ RA and Public services configuration
0.5 Digi-CA™ RA and Public services redundancy configuration
1 HSM configuration
1 Network connectivity and service accessibility tests
0.5 Root and Intermediate CA Key Ceremony
0.5 Digi-CA™ Administration Training
0.5 RA Training
8 Total Project Installation Time
![]() [45] The following technical installation diagram outlines a typical network requirement to run and operate a multi-server Digi-CA™ Server Xg, full redundancy system with a HSM and optional HSM Fail Over (not shown).`
[45] The following technical installation diagram outlines a typical network requirement to run and operate a multi-server Digi-CA™ Server Xg, full redundancy system with a HSM and optional HSM Fail Over (not shown).`
![]() [45] The following is the time required to install a multi-server Digi-CA™ Server Xg full redundancy system with an HSM.
[45] The following is the time required to install a multi-server Digi-CA™ Server Xg full redundancy system with an HSM.
Days Project Part Persons Description
2 Server Configuration
1 Digi-CA™ Core configuration
1 Digi-CA™ Server Failover and Replication
1 Digi-CA™ RA and Public services configuration
0.5 Digi-CA™ RA and Public services redundancy configuration
1 HSM configuration
1 Network connectivity and service accessibility tests
0.5 Root and Intermediate CA Key Ceremony
0.5 Digi-CA™ Administration Training
0.5 RA Training
9 Total Project Installation Time
Links:
[1] https://www.digi-sign.com/order/digi-ca-admin/accept.php
[2] http://www2.digi-sign.com/certificate+authority
[3] http://www2.digi-sign.com/digital+certificate
[4] http://www2.digi-sign.com/two+factor+authentication
[5] http://www2.digi-sign.com/id+card
[6] http://www2.digi-sign.com/electronic+identification
[7] http://www2.digi-sign.com/public+key+infrastructure
[8] http://www2.digi-sign.com/digi-cast
[9] http://www2.digi-sign.com/compliance/introduction
[10] http://www2.digi-sign.com/trust+centre
[11] http://www2.digi-sign.com/digi-ca/administrator/online+certificate+status+protocol
[12] http://www2.digi-sign.com/repository/certificate+practice+statement
[13] http://www2.digi-sign.com/downloads/aacd-manual
[14] http://www2.digi-sign.com/aacd
[15] http://www2.digi-sign.com/service/certificate+authority+management+services#ttm
[16] http://www2.digi-sign.com/downloads/digi-ca-manual
[17] http://www2.digi-sign.com/ssl+certificate
[18] http://www2.digi-sign.com/digi-mail
[19] http://www2.digi-sign.com/key+ceremony
[20] http://www2.digi-sign.com/e+passport
[21] http://www2.digi-sign.com/digi-id
[22] http://www2.digi-sign.com/support/digi-ssl/generate+csr
[23] http://www2.digi-sign.com/digi-ca
[24] http://www2.digi-sign.com/digi-id/distribute/policy
[25] http://www2.digi-sign.com/digi-id/distribute/invite
[26] http://www2.digi-sign.com/digi-id/distribute/enrol
[27] http://www2.digi-sign.com/digi-id/distribute/activate
[28] http://www2.digi-sign.com/certificate+authority/traditional+ca
[29] http://www2.digi-sign.com/digi-ca/introduction/migration
[30] http://www2.digi-sign.com/digi-ca/administrator/certificate+authority+components
[31] http://www2.digi-sign.com/digi-ca/administrator/certificate+authority+modules
[32] http://www2.digi-sign.com/digi-ca/administrator/certificate+authority+console#ra-mc
[33] http://www2.digi-sign.com/
[34] http://www2.digi-sign.com/digi-ca/administrator/index
[35] http://www2.digi-sign.com/digi-ca/transition
[36] http://www2.digi-sign.com/service/digi-cast
[37] http://www2.digi-sign.com/digi-ca/information+database
[38] http://www2.digi-sign.com/digi-ca/information+database#control+centre
[39] http://www2.digi-sign.com/digi-ca/information+database#crl
[40] http://www2.digi-sign.com/digi-access
[41] http://www2.digi-sign.com/digi-ca/customisation/index
[42] http://www2.digi-sign.com/demos/aacd
[43] http://www2.digi-sign.com/digi-ca/migration
[44] http://www.digi-sign.com
[45] https://www.digi-sign.com/downloads/download.php?id=digi-ca-pdf