

![]() [1] Digi-CA™ is the complete Certificate Authority [2] [CA] system for organisations that would like to own and manage their CA inside the organisation. The CA issues the Digital Certificates [3] that are used for two factor authentication [4], electronic signatures, device-to-device authentication, National ID Cards [5], Machine Readable Travel Documents [MRTD [6]], smart cards and ID Cards [5] and many other network, online, web and physical security environments.
[1] Digi-CA™ is the complete Certificate Authority [2] [CA] system for organisations that would like to own and manage their CA inside the organisation. The CA issues the Digital Certificates [3] that are used for two factor authentication [4], electronic signatures, device-to-device authentication, National ID Cards [5], Machine Readable Travel Documents [MRTD [6]], smart cards and ID Cards [5] and many other network, online, web and physical security environments.
This online manual is the resource for many different users of Digi-CA™, from the most basic RA Operator [7] and RA Administrator [8], right through to the senior CA Manager [9].
![]() [1] The Digi-CA™ system can create multiple instances of unique CAs in a single Digi-CA™ system. The Digi-CA™ model imposes delegation of trust downwards from CAs to their Subordinate Certification Authorities [Sub-CAs]. The same Digi-CA™ system also enables any CA or Sub-CA to be signed or cross signed by an external third party CA. And any number of CAs can have any number of cross signed Sub-CAs. As a result of this design principal, the Digi-CA™ model for trust levels increases towards the highest authority. This type of arrangement facilitates easy deployment and scalability of any PKI [10] requirement from the smallest to the largest. Also, the Digi-CA™ can be offered as a managed service outside your environment Digi-CA™ Service, or as the installed software Digi-CA™ Server.
[1] The Digi-CA™ system can create multiple instances of unique CAs in a single Digi-CA™ system. The Digi-CA™ model imposes delegation of trust downwards from CAs to their Subordinate Certification Authorities [Sub-CAs]. The same Digi-CA™ system also enables any CA or Sub-CA to be signed or cross signed by an external third party CA. And any number of CAs can have any number of cross signed Sub-CAs. As a result of this design principal, the Digi-CA™ model for trust levels increases towards the highest authority. This type of arrangement facilitates easy deployment and scalability of any PKI [10] requirement from the smallest to the largest. Also, the Digi-CA™ can be offered as a managed service outside your environment Digi-CA™ Service, or as the installed software Digi-CA™ Server.
The Digi-CA™ System can issue, revoke, suspend, de-suspend and re-sign x.509v3 Digital Certificates [3]. Time-Stamping [11], Certificate Revocation Lists [CRLs], Online Certificate Status Protocol [OCSP] [12] and many other features of a PKI system can be activated as required using the administration console of the system.
The end user information and certificate requests are entered through the web based Registration Authority [RA] Management Console. This powerful RA Management Console manages the entire Certificate Life cycle. Basic Certificate issuing and revocation by Operatives can be further delegated through a basic and modified RA Management Console interface called the Digi-CA™ Control Centre. It is the Digi-CA™ Control Centre or Limited Registration Authority [LRA] that is used by the RA Operator day-to-day.
Digi-CA™ replaces older Traditional PKI [13] technology and CA systems using the latest in CA technology. With Digi-CA™, all of the complexities and onerous technical overhead that were required by Traditional CAs have been simplified to a ‘user-friendly’ and usable level. The Digi-CA™ can even be ‘dropped’ on top of these Traditional CA environments and seamlessly migrate the older system’s users into this more modern and flexible replacement.
Combining the consulting and professional services [14] offered in the Digi-CAST™ methodology [14] with Digi-CA™ can meet all national and international standards [15] such as:
The remainder of this online manual is for use by Managers [9], Administrators [8] and Operators [7] of the Digi-CA™ system. If you have not already done so, please download and read the Digi-CA™ Manual [16], before proceeding further.
See the Digi-CA™ Flash Presentation [17] that explains the issues and benefits of using the system.
![]() [1] Digital Certificates [3] are issued and managed using a Certificate Authority or CA [2]. In the market, there are two main types of CA systems that are explained in more detail in the Digi-CA™ Manual download [18] or in the Managed CA – Digi-CA™ Service [19] and CA Software – Digi-CA™ Server [20] sub sections of the Certificate Authority online book.
[1] Digital Certificates [3] are issued and managed using a Certificate Authority or CA [2]. In the market, there are two main types of CA systems that are explained in more detail in the Digi-CA™ Manual download [18] or in the Managed CA – Digi-CA™ Service [19] and CA Software – Digi-CA™ Server [20] sub sections of the Certificate Authority online book.
Then there is the innovative CA combination that is unique to Digi-CA™ because of the principals used in the Core Design of Digi-CA™:
This unique offering is called the Shared CA: Digi-CA™ Shared
See the Digi-CA™ Flash Presentation [17] that explains the design principals that have made this innovation possible.
So with Digi-CA™ there are in fact three types of Certificate Authority system to choose from:
![]() [1] The Shared CA - Digi-CA™ Shared is a concept and capability that is unique to Digi-CA™. It is made possible by the component design and flexibility that is at the core design of Digi-CA™ and is not available from Traditional CA [13] vendors.
[1] The Shared CA - Digi-CA™ Shared is a concept and capability that is unique to Digi-CA™. It is made possible by the component design and flexibility that is at the core design of Digi-CA™ and is not available from Traditional CA [13] vendors.
The concept is simple: The benefits of outsourcing the entire CA to a Trusted Third Party [TTP] as a Managed CA [19] may meet most of your main business objectives. In a second scenario, your organization may require total ownership of the CA in which case Managed CA is suitable. But there is a third scenario where you want to own the critical assets but do not wish to manage everything internally. In this case, the Digi-CA™ Shared system is the solution.
In instances where critical assets, such as, the Hardware Security Modules [HSMs], databases, key storage and other functions must be retained by your organization and the day-to-day administration, support, help desk, ‘critical response’ and other ‘non critical’ components can be outside your organization, then Digi-CA™ will be your choice.
Digi-CA™ Shared offers all the technical backup and support components of your CA requirements and ‘fills in any gaps’ in your current environment. The external infrastructure, the team of professionals and specialist you require and other critical resources such as Disaster Recovery, critical response and Service Level Agreement [SLA], components can be outsourced with ease. At the same time, the principal assets and integrity you wish to own and control can remain inside your organization.
Digi-CA™ Shared can be designed and delivered to meet your precise requirements and can combine physical IT assets, personnel, help desk, internal and external networks and servers. For further details contact a member of the Digi-CAST1™ [14] Technical Advisor Team and they will advise you accordingly.
![]() [1] To decide on the best CA system for your environment, there are three key considerations you need to take into account and they are explained in the following sub sections of this online manual:
[1] To decide on the best CA system for your environment, there are three key considerations you need to take into account and they are explained in the following sub sections of this online manual:
When deciding on whether the Managed CA [19] or the Managed CA [20] is most suited to you, you should understand the difference between an open and a closed user group. From a CA perspective, this relates to the extent of end user control you have. If the CA exercises some degree of control over the end user’s environment then it is a closed user group and if it doesn’t, it is in an open group.
The following are examples of the two types of user group:
It is not always immediately obvious whether a group is open or closed and it is important that this is determined accurately if your CA is to meet your precise requirements. If there is any doubt, contact the Digi-CAST1™ Team [14] and ask them to advise you.
If the user group is closed, then you may be able to use either CA. There are two exceptions to this when you want to secure:
In 99% of cases an SSL Certificate [22] must be Trusted and if there is any possibility that the secure email [3] is required outside the closed group, then the Trusted Certificate is required here too. In both of these special cases, the Managed CA is your only choice.
The third consideration needed to help you select the correct CA for your organisation is the availability of the type of suitably trained and experienced technical personnel required to run and operate a CA. Most organisations don’t have this type of specialist staff within their organisation and therefore are best advised to use a Managed CA to deliver the required service.
![]() [1] The majority of the remainder of this online manual describes and explains the functionality and flexibility of the Digi-CA™ Server system. With few exceptions, the Digi-CA™ Service can be configured in the same way as Digi-CA™ Server and then offered as a managed service, specifically to meet the needs of your environment.
[1] The majority of the remainder of this online manual describes and explains the functionality and flexibility of the Digi-CA™ Server system. With few exceptions, the Digi-CA™ Service can be configured in the same way as Digi-CA™ Server and then offered as a managed service, specifically to meet the needs of your environment.
There are three classes of Digi-CA™ Server:
The principal difference between Xs, Xp and Xg in each case relates to the degree of integration and customization required. For example, Digi-CA™ Xs can be pre-configured and delivered to the customer for installation without any assistance from Digi-Sign whilst Digi-CA™ Server Xg projects can run for weeks and even months or years.
Depending on type of Digi-CA™ you order and the level of customisation and modification it requires to meet the needs of your specific environment, will dictate the best installation approach. At a basic level (and depending on your qualifications, knowledge, experience, etc.), you can probably install the required operating system and the Digi-CA™ software using help files and telephone support.
Note: If you have technical personnel that can correctly configure a network environment, install the necessary operating systems and provide secure access to the server(s), the Digi-CAST2™ Installations Team [14] may be able to conduct a large part of the installation process prior to visiting your site. In some cases, the complete installation can occur without the need for Digi-CAST2™ to visit your site at all.
![]() [1] The Digi-CAST™ methodology was pioneered in 2004 and is a unique approach to simplifying the design, installation, management, certification [15] and re-certification of any CA environment.
[1] The Digi-CAST™ methodology was pioneered in 2004 and is a unique approach to simplifying the design, installation, management, certification [15] and re-certification of any CA environment.
The Digi-CAST™ methodology [14] has four distinctly separate components that are adapted and designed specifically to meet the needs of any Digi-CA™ environment:
Digi-CAST1™ and CAST2™ are used on all Digi-CA™ Server projects whereas, Digi-CAST3™ and CAST4™ are used on larger projects such as enterprise, public sector or national government environments.
The Digi-CA™ Manual covers the Digi-CAST™ methodology in more detail as does our website: www.digi-sign.com [29]
This online manual examines Digi-CAST1™ and CAST2™ in more detail here as these specific relate to issues that an Administrator or Manager would be directly concerned with.
Digi-CAST1™ is concerned with project planning excellence, cause and affect planning, 'skills pool' analysis, personnel selection and management. The most important thing to remember about all Digi-CAST™ modules is that the entire service is tailored to your specific needs. For further details download the Digi-CA™ Manual [16].
Digi-CAST2™ is concerned with detailing the actual project as documented in Digi-CAST1™. Its concern is with personnel, availability, time lines, 'choke points' and overall project delivery. Combining your resources with ours, we begin the project and work together to a common goal. For further details download the Digi-CA™ Manual.
The basic requirements for every Digi-CA™ Server installation are the same and in most instances, Digi-CAST2™ install the Digi-CA™ Server system on your server(s). As more sophisticated environments arise for Digi-CA™ Server Xp or Digi-CA™ Server Xg, the requirements increase accordingly.
![]() [1] Digi-CA™ Server Xs is Managed CA [20] for installation on a single server and comes complete with all the different sub-systems designed to run and operate efficiently on that single machine.
[1] Digi-CA™ Server Xs is Managed CA [20] for installation on a single server and comes complete with all the different sub-systems designed to run and operate efficiently on that single machine.
As a software product, Digi-CA™ Server Xs only generates client certificates [3] [Digi-IDs™] that can be used for email, two-factor authentication, secure web access, as electronic signatures, for use within a Virtual Private Networks [VPN] or for device-to-device authentication. Like all professional CA systems it allows the Administrator to set up policies and to manage all of the Digi-ID™ [30] life cycle services.
Even with all of the powerful functionality and capabilities that Digi-CA™ Server Xs offers, it is easy to install, configure and operate. A competent Network Engineer or qualified IT Technician could install a fully functional version of Digi-CA™ Server Xs and be fully competent in its operation a few days.
Digi-CA™ Server Xs can only be installed on a single server and is typically used where high availability is not a key component of the environment. As a single server installation, there is no mirroring, load balancing, fail over or synchronizing of data. All records and data are protected by periodic backups only. Typical installations would be small to medium environments where high system availability is not an issue.
Digi-CA™ Server Xp is Managed CA for installation on two servers and offers the same services as Digi-CA™ Server Xs but on a larger scale and with many additional services including Certificate deployment and renewal automation. The primary reason for selecting Xp instead of Xs is because Digi-CA™ Server Xp offers fail-over functionality.
Digi-CA™ Server Xp can also be configured to generate Secure Socket Layer [22] [Digi-SSL™ [31]] web server Certificates, Software & Code Signing Certificates [Digi-CAST™ methodology [14]] in addition to the Digi-ID™ Xp Certificates.
Most Digi-CA™ Server Xp installations are carried out by the Digi-CAST2™ Installations Team. This installation may require the Digi-CAST2™ Team to physically conduct the installation on site, however, if a competent Network Engineer can provide a reliable connection to the correctly configured servers, then it may be possible to conduct the installation over the internet, without incurring travel and accommodation costs. The fully functional version of Digi-CA™ Server Xp can be completed in three to five days on average.
Digi-CA™ Server Xp is installed on two servers and is typically used where high availability is a component of the environment. As a dual server installation, there is mirroring and synchronising of data. All records and data are protected by this fail-over service. The Digi-CA™ Server Xp is split over two servers and gives the option to include a firewall and load balancing device in between. Typical installations would be large enterprise or government environments.
![]() [1] Digi-CA™ Server Xg is the CA for commercial Trust Centres [32] and other large scale PKI [10] deployments. The entire system and its components parts can be split over many servers and systems as required with a minimum of four servers and a single Hardware Security Module [HSM] being the basic deployment.
[1] Digi-CA™ Server Xg is the CA for commercial Trust Centres [32] and other large scale PKI [10] deployments. The entire system and its components parts can be split over many servers and systems as required with a minimum of four servers and a single Hardware Security Module [HSM] being the basic deployment.
Digi-CA™ Server Xg is used where high availability and reliability are a key component of the environment. As a multi-server installation, there is mirroring, fail over and synchronizing of data. All records and data are protected by this fail-over service. The Digi-CA™ Server Xg separates the CA services so that seven layers of security can be applied to the Trust Centre environment. The CA services are located in the Certificate Engine core with the RA, Certificate Revocation List [CRL], Lightweight Directory Access Protocol [LDAP] and Time Stamping [11] services located in the Outer Core (see Appendix II). Typical installations are government and commercial CA Trust Centres.
This class of Digi-CA™ Server has four levels of security including two or three levels of firewalls with fail over facilities and can incorporate hot standby, disaster recovery and a single system can operate from multiple locations.
Digi-CA™ Server Xg customization, configuration and testing is conducted off site after detailed requirements are documented and agreed with the customer. This off site work can take several weeks, or months, depending on the level and scale of the customizations required. Once configured, the fully functional version of Digi-CA™ Server Xg can be completed in five to ten days.
All Digi-CA™ Server Xg installations must be carried out by the Digi-CAST2™ Installations Team and requires that the Team conduct the installation on site with the associated travel and accommodation costs.
![]() [1] The Digi-CA™ is a complete Digital Certificate [3] and certificate management system. It has three main components that are explained in more detail in their respective sub sections:
[1] The Digi-CA™ is a complete Digital Certificate [3] and certificate management system. It has three main components that are explained in more detail in their respective sub sections:
The Digi-CA™ Administration Management Console is for use by Senior Administrators. At a minimum, these should be qualified Senior Administrators with in-depth knowledge and qualifications specifically in IT and IT security networks. Suitable personnel would be the CTO, CIO, CISO, IT Director, Systems Manager, Systems Analyst, Analyst Programmer, Software Engineer, Technical Engineer and similar job functions with ‘hands on’ technical experience of five or more years. The sections of this online manual relevant to these Senior Administrators are marked in blue.
The Digi-CA™ RA Management Console is for use by RA Administrators. At a minimum, these should be qualified network Administrators with good working knowledge and qualifications specifically in IT and IT security networks. Suitable personnel would be the Technical Managers, Information Systems Manager, QA Manager, Product Manager, Systems Analyst, System Administrator, Senior Systems Engineer, Unix Administrator and similar job functions with ‘hands on’ technical experience of three or more years.
The Digi-CA™ Control Centre or LRA Management Console is for use by RA Operators. This is the most basic component of the Digi-CA™ system and the Operator needs only to have basic PC skills to adequately fulfill this role.
![]() [18] The flexibility of the Digi-CA™ [35] Certificate Authority [CA] system design means that each installation is unique and customised to the precise needs of the customer. Once the Digi-CAST™ [36] Team have agreed and documented your requirements, your Managed CA [37], Digi-CA™ Service or CA Software [38], Digi-CA™ Server, is configured and activated. In certain projects, your specific needs may require a combination of CA Software and a Managed CA, to achieve the best results. Uniquely and unlike any other Traditional CA [13] system on the market, Digi-CA™ can offer the Shared CA [39] option.
[18] The flexibility of the Digi-CA™ [35] Certificate Authority [CA] system design means that each installation is unique and customised to the precise needs of the customer. Once the Digi-CAST™ [36] Team have agreed and documented your requirements, your Managed CA [37], Digi-CA™ Service or CA Software [38], Digi-CA™ Server, is configured and activated. In certain projects, your specific needs may require a combination of CA Software and a Managed CA, to achieve the best results. Uniquely and unlike any other Traditional CA [13] system on the market, Digi-CA™ can offer the Shared CA [39] option.
The following are samples of different CA projects that use the different Digi-CA™ options and also combine other valuable services like the Digi-CAST™ Methodology [36] and consulting advice; the Total Trust Management™ [40] [TTM™] CA Management service; and the Digi-TaSC [41] on line system for CA Management and compliance.
The most substantial difference between Digi-CA™ and other Traditional CA [13]s is the flexibility and capabilities that are central to the design of the Public Key Infrastructure [PKI] system. This means that virtually any type of PKI design can be implemented using Digi-CA™ and because Digi-CA™ is probably the most modern CA available on the market, your specific design requirements can be delivered easily and cost effectively.
The following sub sections provide details of a typical project implementation and its stages. The Preliminary Analysis & Requirement Measurement stage of the project (stage I) is the first stage and this sets the project parameters and requirements from the very beginning of your project:
s
The most substantial difference between Digi-CA™ [35] and other Traditional CA [13]s is the flexibility and capabilities that are central to the design of the PKI system. This capability of transferring from a different service provider is a powerful capability that is simply not available from alternative vendor.
Digi-CA™ allows for easy migration from one data centre, or system, in an almost seamless manner. The transfer can be accomplished either physically through hardware transportation or by secure software and data migration whereby all software and database data is securely migrated in an encrypted format from one location to another.
The following sub sections provide details of the suggested project implementation stages for the transition plan. The plan is subject to decision on the re-use of existing HSMs, or the export/import of existing CA private keys and other project implementation considerations that will emerge during the Preliminary Analysis & Requirement Measurement stage of the project (stage I):
The most substantial difference between Digi-CA™ [35] and other Traditional CA [13]s is the flexibility and capabilities that are central to the design of the PKI system. This capability of transferring from a different service provider is a powerful capability that is simply not available from alternative vendor.
Digi-CA™ allows for easy migration from one data centre, or system, in an almost seamless manner. The transfer can be accomplished either physically through hardware transportation or by secure software and data migration whereby all software and database data is securely migrated in an encrypted format from one location to another.
The following sub sections provide details of the suggested project implementation stages for the transition plan. The plan is subject to decision on the re-use of existing HSMs, or the export/import of existing CA private keys and other project implementation considerations that will emerge during the Preliminary Analysis & Requirement Measurement stage of the project (stage I):
Digi-CA™ [35] is probably the most modern Certificate Authority [CA] system currently available in the market. It is modern because it leverages the many advances in open source technology including Linux, SQL and PHP.
Unlike Traditional CA [13]s, the Digi-CA™ system can create multiple instances of unique CAs in a single Digi-CAtrade; system. The Digi-CAtrade; model imposes delegation of trust downwards from CAs to their Subordinate Certification Authorities [Sub-CAs].
The same Digi-CAtrade; system also enables any CA or Sub-CA to be signed or cross signed by an external third party CA. And any number of CAs can have any number of cross signed Sub-CAs. As a result of this design principal, the Digi-CAtrade; model for trust levels increases towards the highest authority. This type of arrangement facilitates easy deployment and scalability of any PKI requirement from the smallest to the largest.
The following provides a high level overview of a typical Digi-CAtrade; Server installation at a Trust Centre [42]:
The Digi-CAST2™ [36] Team will install the Digi-CA™ PKI software and to do this the first data centre must be constructed 100%. This must include all power, cabling, fire detection, fire depressant and that the air conditioning is installed and fully tested. The air conditioning system testing is very important, as it can cause water issues if not fully tested.
The Trust Centre must then be cleaned to medical/hospital standards before any hardware is installed. The construction on the second disaster recovery data centre (if required) should start at the same time, or no more than two weeks after the first data centre. It is not required that this Disaster Recovery data centre is completed before the Digi-CAST2™ Team arrive at the Trust Centre, however it must be finished no later than one week after the Digi-CAST2™ Team arrive on site and again must be 100% finished and cleaned in that time.
Nothing will happen with the Digi-CA™ PKI software installation until the Trust Centre completion and cleaning date is confirmed. Once this date is confirmed and the hardwre is ordered, the Partner [44] should be capable fo getting all the servers, switches, network and server software, HSMs, etc delivered within 2-3 weeks of the contract being signed.
After the contract is signed the Trust Centre should be ready so that the installation of the IT infrastructure can be completed within 1 week. By the beginnning of week 4, the entire of the main Trust Centre is active and ready for the installation of the Digi-CA™ software.
Week 5 the Disaster Recovery data centre should be completed and the the Digi-CAST2 Installations Team will then arrive to begin work on the Trust Centre whilst the Digi-Trust™ Partner [44] to complete the second data centre IT infrastructutre totally and ready in one week so that by week 6, the second week for the the Digi-CAST2 Installations Team on site, they can begin the configuration of this Disaster Recovery Digi-CA™.
In week 7, after the contract is signed, the Digi-CAST2 Installations Team will be finished and can seek to have the User Acceptance Testing [UAT] sign off, to officially complete the installation process.
![]() [1] The Digi-CA™ Administrators Master Console is the central core of the entire CA system. From this Administrators Master Console the Administration of the CA is implemented and managed. The Administrators Master Console creates the Root CA, CA, Intermediate and Subordinate or Sub-CAs, the RAs and the Control Centres or LRAs.
[1] The Digi-CA™ Administrators Master Console is the central core of the entire CA system. From this Administrators Master Console the Administration of the CA is implemented and managed. The Administrators Master Console creates the Root CA, CA, Intermediate and Subordinate or Sub-CAs, the RAs and the Control Centres or LRAs.
The Digi-CA™ system model is a hierarchical trust model, in which, each entity implicitly trusts the entity above it. This model imposes the delegation of trust downwards from Root CAs to its Subordinate CAs. As a result, inherent in the design of the Digi-CA™ is the fact that the levels of trust increase as you go upwards to the higher authority. By its very design, this type of system architecture facilitates easy deployment of a large scale PKI [10]. The Administrators Master Console, its function and detailed instructions on how to use it are further described in Section 5 of this on line manual.
Read the on line Training Manual [45] for the CA AMC.
The Digi-CA™ RA Management Console is the primary management interface for a specific CA or Sub-CA. The RA Management Console provides an interface to access and manage RAs and LRAs, that are created through the CA Administration Management Console. Each RA or LRA can interface multiple CAs to allow the issuance of different types of digital Certificates through different CAs from a single central and easily manageable location. The remainder of the functions of the RA Management Console its function and detailed instructions on how to use it are further described in Section 6 of this on line manual.
Read the on line Training Manual [46] for the RA MC.
The Digi-CA™ Control Centre is more commonly known in the PKI [10] industry as an LRA and is the RA Operator interface for accessing the RA with limited features provided. For the remainder of this document and to avoid confusion, the LRA is referred too as the Control Centre. The Control Centre is a ‘stripped down’ version of the RA Console. The Control Centre is used to manage individual Certificate life cycle functions such as issuing, revoking, suspending and renewing Certificates. The remainder of the functions of the Control Centre, its function and detailed instructions on how to use it are further described in Section 5 of this on line manual.
Read the on line Training Manual [47] for the LRA Control Centre.
Depending on the configuration, policy and distribution of your Digi-CA™, some service may be publicly available. These public services are typically to enable basic end user requirements for Digital Certificates and the following sub sections describe the four main functions:
Read the on line Training Manual [48] for the RA RS.
![]() [49] The following table sets out the principal technical specifications of the Digi-CA™:
[49] The following table sets out the principal technical specifications of the Digi-CA™:
![]() [49] The Digi-CA™ PKI [10] System software suite is a multi application component based PKI system for managing cryptographic keys, Digital [X.509] Certificates and supplemental PKI related services. Each application component provides a series of defined functionalities to other PKI application components of the system, as well as to administering and operating parties, and to end entities, to whom certificates are issued. This system is built with the following modules:
[49] The Digi-CA™ PKI [10] System software suite is a multi application component based PKI system for managing cryptographic keys, Digital [X.509] Certificates and supplemental PKI related services. Each application component provides a series of defined functionalities to other PKI application components of the system, as well as to administering and operating parties, and to end entities, to whom certificates are issued. This system is built with the following modules:
All Digi-CA™ components providing core functionalities were developed using C programming language and the software operates under Unix/Linux operating system environment, which has proven to be a solid, reliable – and if not the best - platform family choice for server side applications.
Diagram below illustrates the overall logical and high level hardware architecture design of a complex PKI infrastructure that Digi-CA™ can be deployed in. This includes multi-server based system component distribution, replication and failover of various PKI services and load balancing.
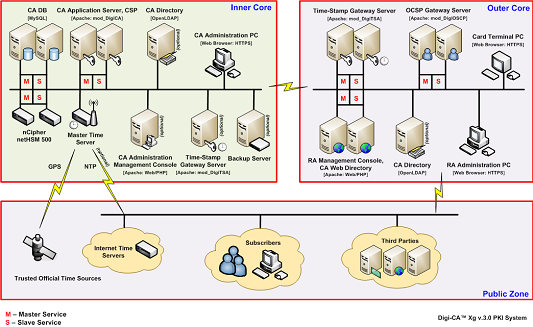
![]() [49] Whilst Digi-CA™ software can meet most complex requirements, in many scenarios it is often required to operate all PKI [10] related services on a single dedicated server hardware. Digi-CA™ can easily meet this requirement and the diagram below illustrates overall logical and high level hardware architecture design of the basic infrastructure utilizing a single server to operate all Digi-CA™ PKI services. This unique feature of Digi-CA™ software suite provides not only a flexible range of possible configuration variations but allows organizations to slowly build their own PKI infrastructure from a very small environment, thus carefully control their expenditure related to purchasing and maintenance of hardware devices.
[49] Whilst Digi-CA™ software can meet most complex requirements, in many scenarios it is often required to operate all PKI [10] related services on a single dedicated server hardware. Digi-CA™ can easily meet this requirement and the diagram below illustrates overall logical and high level hardware architecture design of the basic infrastructure utilizing a single server to operate all Digi-CA™ PKI services. This unique feature of Digi-CA™ software suite provides not only a flexible range of possible configuration variations but allows organizations to slowly build their own PKI infrastructure from a very small environment, thus carefully control their expenditure related to purchasing and maintenance of hardware devices.
Digi-CA™ PKI System provides a wide range of PKI related functionalities and introduces a variety of services and features including:
Production speed:
Key length:
Certificate validity:
Key storage:
Cryptographic Ciphers:
Signature Algorithms:
Entropy:
![]() [49] The success or failure of any project can usually be traced back to the original plans. As explained, the Digi-CAST™ methodology [14] is a unique approach to a CA project and its purpose is to ensure the successful delivery of Digi-CA™, every time.
[49] The success or failure of any project can usually be traced back to the original plans. As explained, the Digi-CAST™ methodology [14] is a unique approach to a CA project and its purpose is to ensure the successful delivery of Digi-CA™, every time.
Simply buying Digi-CA™ (or any Managed CA [20]) is not a guarantee that your environment and your project will succeed. To achieve success, the organization must actively participate in the project from the outset. To do this, you must gain a clear understanding of the Digital Certificate [3] technology and the functions, uses and capabilities of a Certificate Authority [2].
If you have not already done so, download the Digi-CA™ Manual [16] for further information.
The simplest way to select the correct Digi-CA™ for your organization is to decide how many users you have (or in some cases the number of physical devices you need to identify). This should include employees, customers, partners or suppliers and the individual people that work in each of these areas that you wish to issue a Digital Certificate [Digi-ID™ [30]] too.
Environment Requirement Users Recommended Digi-CA™
Environment B Online transaction and document signing [50] for application forms and business processes 40,000 Digi-CA™ Server Xs
Environment C Device authentication 100,000 Digi-CA™ Server Xp
Environment D Manufacturer or Large Software House with fail over Unlimited Digi-CA™ Server Xp
Environment E National Security requirement for foreign delegates 1,000 Digi-CA™ Server Xg
(customised)
Environment F National Identity Card and/or Smart Passport 25,000,000 Digi-CA™ Server Xg
(customised)
Environment G Digi-CA™ Xg Trust Centre Unlimited Digi-CA™ Server Xg
Another alternative is to look at the level of security that you wish to achieve. If the security is relating to corporate secrets, national security or can be regarded as critical, regardless of cost, then Digi-CA™ Xg may be the only option for you. The Digi-CAST1™ Team [36] of professional advisors will guide you toward the optimum solution.
The most important benefit of Digi-CA™ is that every aspect of the final solution can be tailored to meet your precise user, security and policy requirements.
The most important benefit of Digi-CA™ is that every aspect of the final solution can be tailored to meet your precise user, security and policy requirements.
The following table can be used as a guide to assist in choosing the best Digi-CA™ Server for your environment.
![]() [49] You should clearly identify if your user group is open or closed, what you want to use your Certificates for and whether you have the staff required to run and operate the Digi-CA™. If, having downloaded and read the Digi-CA™ Manual [16] that advises you on how to select your Digi-CA™ and you are still not clear, then contact the Digi-CAST1™ Team [36] and seek their advice before proceeding further.
[49] You should clearly identify if your user group is open or closed, what you want to use your Certificates for and whether you have the staff required to run and operate the Digi-CA™. If, having downloaded and read the Digi-CA™ Manual [16] that advises you on how to select your Digi-CA™ and you are still not clear, then contact the Digi-CAST1™ Team [36] and seek their advice before proceeding further.
Using the authentication and validation Certificate Policies from your Traditional CA, Digi-CA™ can migrate users automatically without requiring any IT resources or Administrators’ time.
The Digi-CA™ is probably the most flexible and capable CA system available in the market today. Unlike the other Traditional CAs, Digi-CA™ takes advantage of the many advances in technology over the past seven years and you benefit by getting the flexible, cost effective and easily integrated CA system you need.
The Digi-CA™ still uses Unix in its Certificate Engine core but by using Open Standard Architecture in other modules, the Digi-CAST2™ Team customisation and upgrade costs are substantially less than those normally associated with the complex and costly modifications of the less flexible Unix Traditional CAs.
This section explains the design principles and also gives typical examples of previous customizations . The most important feature of Digi-CA™ is that your precise requirements can be delivered, exactly as you require.
In the larger or more complex environment, the organization may require a workflow process to control the use of the Digi-CA™ usage from a cost, security or for general management reasons. The following is an example of a customization currently in use by a Digi-Sign customer for issuing Digi-SSLs™:
This type of customization is not unusual but it does add to the initial cost of deploying a Digi-CA™ system.
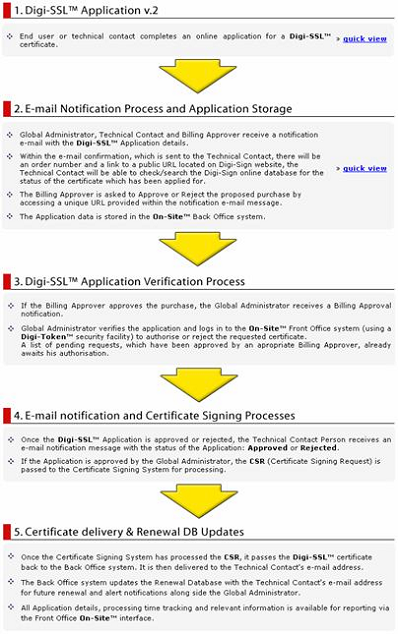
Every aspect of the Digi-CA™ can be automated. Examples of this would be where the Digi-IDs™ are being used to replace Usernames and Passwords for login to a secure website, to replace hardware tokens like SecurID®, to issue Digi-IDs™ for secure email [3] on a closed network or to replace an existing Traditional CA with Digi-CA™.
Using the Digi-CA™ flexible design technology and capabilities, it is possible to use existing LDAPs or other databases such as Oracle®, Active Directory® or any other SQL or flat file format to automate the Digi-ID™ [30] issuing, renewal, suspension and revocation processes.
Read more on why you should choose Digi-Sign [51]
![]() [49] The entire Digi-CA™ system and all of the interfaces used by the Administrators and users can be completely customized on request. Typical reasons for the graphical changes are for integrating Digi-CA™ into a larger application to make a complete package or the simpler integration of the Digi-CA™ into the organization’s web systems or extranet.
[49] The entire Digi-CA™ system and all of the interfaces used by the Administrators and users can be completely customized on request. Typical reasons for the graphical changes are for integrating Digi-CA™ into a larger application to make a complete package or the simpler integration of the Digi-CA™ into the organization’s web systems or extranet.
The specification of the Digi-CA™ at the time of going to print is available in Appendix IV. All specification updates and technical help files are updated using the online support section of the Digi-Sign website located at www.digi-sign.com [29].
Digi-CA™ offers the capability to completely localise all interfaces, help files and user screens into your local language(s). This is particularly important to organisations where English is not used. It is also possible to have multiple interfaces with multiple languages for the same system. The following two samples show the Digi-CA™ Control Centre screen in Chinese and the user enrollment screen where users can apply for a Digi-ID™ [30] in Turkish.
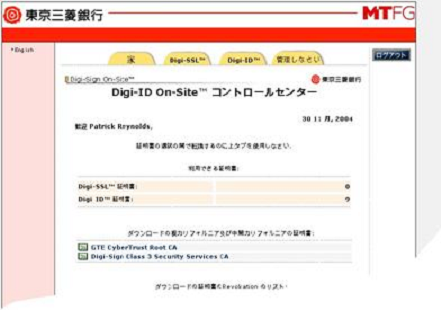
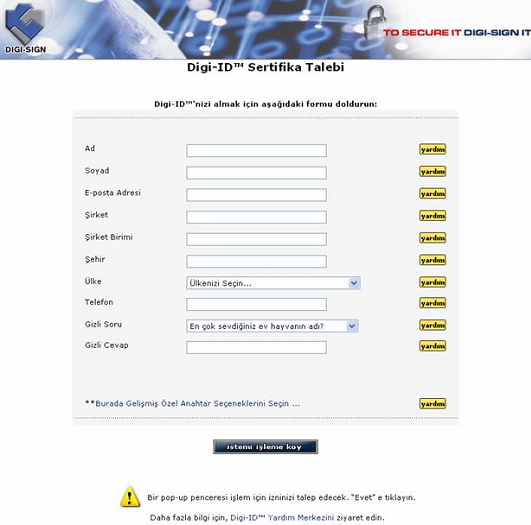
Note: Sample Only – Grammar & Diction not checked
The importance of the capability to produce the Digi-CA™ in the local language(s) cannot be over stated. It will result in faster training of the RA personnel and will significantly reduce the Help Desk Support calls (where users are seeking help to with translations from English rather than actual technical support related issues).
It is also possible to have a single Digi-CA™ configured in multiple languages so that different Digi-RAs™ in different countries can use the same Digi-CA™ Control Centre in their native language. Similarly, the users requesting Digi-IDs™ can do so from the same system but again in their native language.
To have your Digi-CA™ localized in your language, the system files and instructions are available in Appendix I.
![]() [49] The Digi-CA™ RA/API system is a highly customisable way to issue and manage x.509 Certificates issued for digital signature [3], secure email [3], two factor authentication [4] and other purposes. It:
[49] The Digi-CA™ RA/API system is a highly customisable way to issue and manage x.509 Certificates issued for digital signature [3], secure email [3], two factor authentication [4] and other purposes. It:
The Digi-CA™ RA/API system is account based, therefore in order to be able to implement and use the system, the RA API account needs to be setup first on the Digi-CA™ Certificate Engine core system. Before implementing the RA API you must contact the Digi-CAST™ [14] Team to ensure you have the latest version and release notes.
The entire RA/API system is based on a flat and secure communication between the RA API and the Digi-CA™ Certificate Engine Core system. It is achieved using the HTTP ‘POST’ method secured with an SSL/TLS layer on top of a standard TCP/IP connection.
Depending on the specific action that needs to be completed by the Administrator, i.e.: Digi-ID™ [30] request, Digi-ID™ approval, Digi-ID™ suspension, Digi-ID™ revocation or other request, a different URL will be used for each individual action.
Relevant points below are an overview of the steps involved in the Digi-CA™ RA operations using the RA/API.
![]() [49] The user will browse to a fully customized Digi-ID™ Application Form Enrolment page. They will complete the details in the web form and click the ‘submit’ button. Depending on the chosen Certificate delivery method (Process/Package), a VB script or Java applet on the webpage can then initiate the chosen Cryptographic Service Provider [CSP] engine to generate the Private Key and Certification request (PKCS#10), before submitting all data (with the exception of the Private Key if the Process Method is chosen) to the Digi-CA™ Certificate Engine core system.
[49] The user will browse to a fully customized Digi-ID™ Application Form Enrolment page. They will complete the details in the web form and click the ‘submit’ button. Depending on the chosen Certificate delivery method (Process/Package), a VB script or Java applet on the webpage can then initiate the chosen Cryptographic Service Provider [CSP] engine to generate the Private Key and Certification request (PKCS#10), before submitting all data (with the exception of the Private Key if the Process Method is chosen) to the Digi-CA™ Certificate Engine core system.
You will need to decide the type and order of the attributes that will appear in the "Subject" field of your Digi-ID™ [30] Certificate. You may have multiple attributes of the same type (e.g. multiple ‘OU’s are common). You will also need to consider what attributes are required and which of these, if any, are optional. These settings may also be overwritten by the Digi-Policy™ applied on the Digi-CA™ Certificate Engine Core system for the specific RA API. The following table is a list of the common attribute types that are currently recognized by the Digi-CA™ Certificate Engine core system:
|
|
|
|
|
|
|
|
|
|
CN |
|
1 |
64 |
|
|
|
|
SN |
|
1 |
64 |
|
|
|
|
|
|
1 |
64 |
|
|
|
|
C |
|
2 |
2 |
|
|
|
|
L |
|
1 |
|
|
|
|
|
S |
|
1 |
|
|
|
|
|
|
|
1 |
|
|
|
|
|
O |
|
1 |
64 |
|
|
|
|
OU |
|
1 |
64 |
|
|
|
|
T |
|
1 |
64 |
|
|
|
|
|
|
1 |
|
|
|
|
|
|
|
1 |
40 |
|
|
|
|
|
|
1 |
40 |
|
|
|
|
|
|
1 |
32 |
|
|
|
G |
|
1 |
64 |
|
|
|
|
I |
|
1 |
64 |
|
|
|
|
E |
|
1 |
|
|
|
![]() [49] The type of Digi-CA™ Server you choose for your environment will dictate what information you need to install it and if you will need assistance from the Digi-CAST2™ Installations Team [36].
[49] The type of Digi-CA™ Server you choose for your environment will dictate what information you need to install it and if you will need assistance from the Digi-CAST2™ Installations Team [36].
The basic requirements for installing any Digi-CA™ Server are very similar and the four main components are detailed for each case:
Before proceeding with any installation of Digi-CA™, it is strongly recommended that a thorough study of the download Digi-CA™ Manual [18] Manual is undertaken. Ultimately, Digi-CA™ is software, however, all Certificate Authorities [2] need careful planning and decision making by informed personnel if the project is to be a success.
Careful consideration should also be given to using the Digi-CAST1™ [36] professional services and from the advice received whether it is recommended that Digi-CAST2™ Installation Team support.
Digi-CA™ Server Xs is Managed CA [20] for installation on a single server and comes complete with all the different sub-systems designed to run and operate efficiently on that single machine.
The basic Digi-CA™ Server Xs software is supplied on a DVD, or as a downloadable binary file inside a .zip file from the www.digi-sign.com [29] website. Subject to ordering and purchasing, the version of Digi-CA™ Server Xs you receive may be modified to meet your specific requirements. These modifications will result in a different install sequence in some cases. To ensure the installation instructions are compatible with the customized version of your Digi-CA™ software, the specific installation guide is included in the software delivered. Once received, install it by using the ‘Digi-CA Install Guide.doc’ supplied with the specific software on the DVD, or in the .zip file.
If a secure VPN connection to the single server can be provided, it is possible that the installation of the software can be carried out virtually by the Digi-CAST2™ Installation Team if required. The benefit of this is that it reduces the cost of travel and accommodation. When examining each of the following four sub sections you can consult with the Digi-CAST2™ Installations Team, at any time, to check configurations and access for you.
![]() [49] These are the minimum suitable conditions for the correct operation of the single server Digi-CA™ Server Xs:
[49] These are the minimum suitable conditions for the correct operation of the single server Digi-CA™ Server Xs:
These are the minimum equipment specification for the correct operation of the single server Digi-CA™ Server Xs:
Digi-CA™ Server Xs is supplied complete and ready for total install on the server but it must have a Unix or Linux Operating System [OS] pre-configured.
During the installation, the Digi-CA™ Server will use versions of the following software that will be hardened and modified by the Digi-CAST2™ Team [36] during their installation work:
The previous list is provided for information purposes only.
These are the minimum requirements for the correct installation of the single server Digi-CA™ Server Xs:
Digi-CA™ Server Xs can be installed on any Unix or Linux platform once it is compiled in advance. The Digi-CAST1™ Team will advise you on the best Operating System [OS] for your environment and here is a suggested list:
![]() [49] Digi-CA™ Server Xp is Managed CA [20] for installation on two or more servers and comes complete with all the different sub-systems designed to run and operate efficiently on these machines. Customizations and certain specific requirements can be facilitated in this class of the Digi-CA™ software and HSM hardware can also be included in the design of the CA network as required.
[49] Digi-CA™ Server Xp is Managed CA [20] for installation on two or more servers and comes complete with all the different sub-systems designed to run and operate efficiently on these machines. Customizations and certain specific requirements can be facilitated in this class of the Digi-CA™ software and HSM hardware can also be included in the design of the CA network as required.
The basic Digi-CA™ Server Xp software is supplied on a DVD, or as a downloadable binary file inside a .zip file from the www.digi-sign.com [29] website. Subject to ordering and purchasing, the version of Digi-CA™ Server Xs you receive may be modified to meet your specific requirements. These modifications will result in a different install sequence in some cases. To ensure the installation instructions are compatible with the customized version of your Digi-CA™ software, the specific installation guide is included in the software delivered. Once received, install it by using the ‘Digi-CA Install Guide.doc’ supplied with the specific software on the DVD, or in the .zip file.
As with Digi-CA™ Server Xs, if a secure VPN connection to the server environment can be provided, it is possible that the installation of the software can be carried out virtually by the Digi-CAST2™ Installation Team [36] if required. The benefit of this is that it reduces the cost of travel and accommodation. When examining each of the following four sub sections you can consult with the Digi-CAST2™ Installations Team, at any time, to check configurations and access for you.
The minimum suitable conditions for the correct operation of the dual server Digi-CA™ Server Xp are the same as those for [55].
These are the minimum equipment specification for the correct operation of the dual server Digi-CA™ Server Xp are the same as the specifications for [56] except 2 x Servers: Dell®/HP®/IBM®, are required.
Digi-CA™ Server Xp is supplied complete and ready for total install on the server but it must have a Unix or Linux Operating System [OS] pre-configured.
During the installation, the Digi-CA™ will use versions of the same software that is used by [55] will be hardened and modified by the Digi-CAST2™ Team during their installation work.
The minimum requirements for the correct installation of the dual server Digi-CA™ Server Xp are the same as those for [57].
As with Digi-CA™ Server Xs [58], Digi-CA™ Server Xp can be installed on any Unix or Linux platform once it is compiled in advance. The Digi-CAST1™ Team will advise you on the best Operating System [OS] for your environment.
![]() [49] The Digi-CA™ Server Xg is completely customizable and can be installed across many servers, even if they are in different locations. As stated, Digi-CA™ Server Xg customisation, configuration and testing is conducted off site after detailed requirements are documented and agreed with the customer. This off site work can take several weeks, or months, depending on the level and scale of the customisations required.
[49] The Digi-CA™ Server Xg is completely customizable and can be installed across many servers, even if they are in different locations. As stated, Digi-CA™ Server Xg customisation, configuration and testing is conducted off site after detailed requirements are documented and agreed with the customer. This off site work can take several weeks, or months, depending on the level and scale of the customisations required.
As an example, when Digi-CA™ Server Xg is used to build a Trust Centre [32], a minimum of four servers are required and if the correct internet connection and a VPN can be provided to the servers, it is possible that much of the preparation and network testing prior to the installation of the software can be carried out virtually. However, the Digi-CA™ Server Xg will require at least one site visit from a Digi-CAST2™ Team Member [36] to conduct certain specialist tasks.
The benefit of using the VPN connection as much as possible during this preparatory work is that it reduces the cost of travel and accommodation. When examining each of the following three sub sections you can consult with the Digi-CAST2™ Team at any time to check configurations and access for you.
These are the minimum suitable conditions for the correct operation of the multiple server Digi-CA™ Server Xg:
These are the minimum equipment specification for the correct operation of the dual server Digi-CA™ Server Xp are the same as the specifications for [56] except 4 x Servers: Dell®/HP®/IBM®, are required and we also recommend using at least one HSM (nCipher, Utimaco, etc).
Digi-CA™ Server Xg is supplied complete and ready for total install on the server but it must have a Unix or Linux Operating System [OS] pre-configured.
During the installation, the Digi-CA™ will use versions of the same software that is used by [55] will be hardened and modified by the Digi-CAST2™ Team [36] during their installation work.
The minimum requirements for the correct installation of the Digi-CA™ Server Xg are the same as those for [57].
![]() [49] The Digi-CA™ PKI [10] System supports a variety of Unix and Linux operating systems. It was also designed to use various third party software libraries that are required to be present on your operating system prior to the beginning of the installation of any version of Digi-CA™.
[49] The Digi-CA™ PKI [10] System supports a variety of Unix and Linux operating systems. It was also designed to use various third party software libraries that are required to be present on your operating system prior to the beginning of the installation of any version of Digi-CA™.
The support and ongoing development of third party software applications and libraries that are necessary to install and operate Digi-CA™ software is not part of the system or license provided. However, for your reference, you can find a set of stable software applications and libraries provided as part of the distribution of the Digi-CA™ PKI System. A list of these applications and libraries and a set of quick installation guides for each of the necessary applications or libraries is included in this sub section.
![]() [49] As can be seen from the extensive documentation relating to the Key Ceremony [60], at the heart of every Digi-CA™ is at least one Root CA. Every Digi-CA™ Certificate is made from a Public and a Private Key. After the Root Key Ceremony procedure has produced the unique pair of Public and Private Root Keys is generated and depending on the Certificate Practice Statement [61] [Certificate Practice Statement [61]] and Certificate Policy [CP], the generation of the Root Keys may require notarization, legal representation, witnesses and ‘Key Holders’ to be present. This process is best explained with some examples and for further details review the Root Key Ceremony [60].
[49] As can be seen from the extensive documentation relating to the Key Ceremony [60], at the heart of every Digi-CA™ is at least one Root CA. Every Digi-CA™ Certificate is made from a Public and a Private Key. After the Root Key Ceremony procedure has produced the unique pair of Public and Private Root Keys is generated and depending on the Certificate Practice Statement [61] [Certificate Practice Statement [61]] and Certificate Policy [CP], the generation of the Root Keys may require notarization, legal representation, witnesses and ‘Key Holders’ to be present. This process is best explained with some examples and for further details review the Root Key Ceremony [60].
The Root Certificate is only ever used to sign the Intermediate Root Key(s). After signing this Key(s) the Root Key is 3-DES encrypted and split into a minimum of 4 Key shares that are each stored on 3-DES encrypted smartcard and signed with RSA SHA-1. All Key shares will have a unique password and should be stored separately in different secure locations (bank vault, safety deposit box, attorney’s office, etc). A Key generation log is kept in the system and in a separate physical log.
Important Note: the Root Certificate should not exceed a 25-Year life duration.
In order to create Digi-IDs™ from the system, at least one self-signed Digi-CA™ Root Certificate must be generated. There is a possibility in the system, depending on ordered options, to create any number of Digi-CA™ Root Certificates and Digi-CA™ Intermediate Roots with different policies and validity. The figure below represents a theoretical relationship between Digi-CA™ CA Certificates. Please consult Digi-CAST1™ [36] before setting up your specific schema.
The Intermediate CA Certificate is protected by 3-DES encryption and all key shares have unique passwords.
Important Note: the Root Certificate should not exceed a 25-Year life duration.
The Digi-CA™ PKI [10] System provides the ability to operate a Sub-CA that can be signed by a publicly recognized CA. This enables the Digi-CA™ to issue and manage Digital Certificates [3] for S/MIME and SSL, that are globally trusted throughout the Internet Community. To get a globally Trusted Root [TRoot] to sign the Sub-CA, consult the Digi-CAST™ [14] Team leader for your project.
The following pages are intended for the Network Engineer or Administrator for the Digi-CA™ system that is responsible for preparing the network and servers, prior to installation.
To avoid delays with the install of your Digi-CA™ system and to avoid the postponement or complete cancellation of your installation, follow the instructions on each of these pages very carefully.
If in doubt, or need technical assistance, email digi-cast@digi-sign.com [62] to contact a member of the Digi-CAST™ [36].
![]() [63] Usually a stable and recent enough Sendmail software is provided for your convenience by the Operating System Vendor and we recommend using the release that the Vendor included in its Operating System distribution. For further information about Sendmail or to download its most recent release, visit the Sendmail website on www.sendmail.org [64].
[63] Usually a stable and recent enough Sendmail software is provided for your convenience by the Operating System Vendor and we recommend using the release that the Vendor included in its Operating System distribution. For further information about Sendmail or to download its most recent release, visit the Sendmail website on www.sendmail.org [64].
Usually a stable and recent enough GCC compiler is provided for your convenience by the Operating System Vendor and we recommend using the release that the Vendor included in its Operating System distribution. For further information about the GNU C Compiler or to download its most recent release, visit the GNU GCC website on gcc.gnu.org.
OpenSSL 0.9.8c compiled from source code distribution with necessary patches as per the list below.
Patch Name Version Comments
Time-Stamping [65] 20060923-0.9.8c required for Time-Stamping
nCipher CHIL 0.9.8a to support nCipher HSM
Before you compile your OpenSSL toolkit, you will need to apply the Time-Stamping patch and optionally a Cryptographic Hardware Interface Library patch for interfacing nCipher HSM devices. Both patches are provided with the source distribution of Digi-CA™ and you may find them in the OpenSSL/patches sub-directory of your Digi-CA™ source distribution package. Visit OpenSSL website on www.openssl.org [66] to download the OpenSSL cryptographic toolkit. When configuring and compiling this toolkit, ensure you compile its libraries as dynamically shared. To perform a quick installation, use the Quick Installation guide provided below.
The Quick Installation Guide [QIG] for OpenSSL 0.9.8c suggests that you change working directory to the location where you saved the OpenSSL toolkit source distribution release. For the purpose of this installation guide, we will assume you have saved the OpenSSL toolkit in /usr/local/src directory.
Using tar, unpack files from the archive:
Change working directory:
Using patch, apply patch to enable Time-Stamping feature:
Optionally, apply patch for Cryptographic Hardware Interface Library:
Prepare the installation:
Compile, test and install:
![]() [63] The recommended URL syntax based Network Communication Tool is cURL 7.16.1 and this should be compiled from source code distribution with SSL support enabled. Visit the cURL website on curl.haxx.se to download the cURL source distribution.
[63] The recommended URL syntax based Network Communication Tool is cURL 7.16.1 and this should be compiled from source code distribution with SSL support enabled. Visit the cURL website on curl.haxx.se to download the cURL source distribution.
Change working directory to the location where you saved the cURL source distribution release. For the purpose of this installation guide, we will assume you have saved the cURL in /usr/local/src directory.
Change working directory:
Using tar, unpack files from the archive:
Change working directory:
Prepare the installation:
Compile, test and install:
stunnel 4.20 compiled from source code distribution with SSL support enabled. Visit the sTunnel website on www.stunnel.org [67] to download the sTunnel source distribution.
Change working directory to the location where you saved the sTunnel source distribution release. For the purpose of this installation guide, we will assume you have saved the sTunnel in /usr/local/src directory.
Change working directory:
Using tar, unpack files from the archive:
Change working directory:
Prepare the installation:
Compile, test and install:
The recommended Hashing & Encryption Tools and Libraries are from libmcrypt 2.5.8 compiled from source code distribution. Visit the mCrypt website on mcrypt.sourceforge.net to download the mCrypt library source distribution.
Change working directory to the location where you saved the mCrypt library source distribution release. For the purpose of this installation guide, we will assume you have saved the mCrypt library in /usr/local/src directory.
Change working directory:
Using tar, unpack files from the archive:
Change working directory:
Prepare the installation:
Compile, test and install:
![]() [63] GNU mHash 0.9.9 compiled from source code distribution. Visit the mHash website on mhash.sourceforge.net to download the mHash source distribution.
[63] GNU mHash 0.9.9 compiled from source code distribution. Visit the mHash website on mhash.sourceforge.net to download the mHash source distribution.
Change working directory to the location where you saved the mHash source distribution release. For the purpose of this installation guide, we will assume you have saved the mHash in /usr/local/src directory.
Using tar, unpack files from the archive:
Change working directory:
Prepare the installation:
Compile, test and install:
mCrypt 2.6.6 compiled from source code distribution. Visit the mCrypt website on mcrypt.sourceforge.net to download the mCrypt toolkit source distribution.
Change working directory to the location where you saved the mCrypt toolkit source distribution release. For the purpose of this installation guide, we will assume you have saved the mCrypt toolkit in /usr/local/src directory.
Change working directory:
Using tar, unpack files from the archive:
Change working directory:
Prepare the installation:
Compile, test and install:
Apache 2.2.6 Web Server is compiled from source code distribution with SSL support enabled. Visit the Apache website on www.apache.org [68] to download the Apache web server source distribution.
Change working directory to the location where you saved the Apache source distribution release. For the purpose of this installation guide, we will assume you have saved the Apache source distribution in /usr/local/src directory.
Change working directory:
Using tar, unpack files from the archive:
Change working directory:
Prepare the installation:
Compile and install:
![]() [63] MySQL 5.0.37 SQL Database Server and Client is compiled from source code distribution with SSL support enabled. Visit the MySQL website on www.mysql.org [69] to download the MySQL database server source distribution.
[63] MySQL 5.0.37 SQL Database Server and Client is compiled from source code distribution with SSL support enabled. Visit the MySQL website on www.mysql.org [69] to download the MySQL database server source distribution.
Change working directory to the location where you saved the MySQL source distribution release. For the purpose of this installation guide, we will assume you have saved the MySQL source distribution in /usr/local/src directory.
Using tar, unpack files from the archive:
Change working directory:
As super user, add new user and group:
Prepare the installation:
Compile and install:
Copy the recommended MySQL configuration file to its destination folder within your operating system:
Change working directory:
Change ownership of the working directory:
Install default databases:
Change ownership of the working directory:
Before you compile your PHP package, you will need to apply the DigiCA™ Cryptographic patch, that will enable the PHP language with additional cryptography related features required by Digi-CA™. The patch is provided with the source distribution of Digi-CA™ and you may find it in the PHP/patches sub-directory of your Digi-CA™ source distribution directory tree. Visit PHP website on www.php.net [71] to download the PHP package. To perform a quick installation, use the Quick Installation guide provided below.
![]() [63] Change working directory to the location where you saved the PHP source distribution release. For the purpose of this installation guide, we will assume you have saved the PHP source distribution release in /usr/local/src directory.
[63] Change working directory to the location where you saved the PHP source distribution release. For the purpose of this installation guide, we will assume you have saved the PHP source distribution release in /usr/local/src directory.
Using tar, unpack files from the archive:
Patch PHP source with Digi-CA™ Cryptographic Patch:
Change working directory:
Prepare the installation:
Compile, test and install:
For the PHP PEAR DB 1.7.13 and LOG 1.9.11 packages visit PHP PEAR website on pear.php.net to download the PHP PEAR DB and LOG packages. To perform a quick installation, use the Quick Installation guide provided below.
Links:
[1] https://www.digi-sign.com/order/digi-ca-admin/accept.php
[2] http://www2.digi-sign.com/certificate+authority
[3] http://www2.digi-sign.com/digital+certificate
[4] http://www2.digi-sign.com/two+factor+authentication
[5] http://www2.digi-sign.com/id+card
[6] http://www2.digi-sign.com/electronic+identification
[7] http://www2.digi-sign.com/digi-ca/administrator/certificate+authority+console#control-centre
[8] http://www2.digi-sign.com/digi-ca/administrator/certificate+authority+console#ra-mc
[9] http://www2.digi-sign.com/digi-ca/administrator/certificate+authority+console#ca-amc
[10] http://www2.digi-sign.com/public+key+infrastructure
[11] http://www2.digi-sign.com/digi-ca/time+stamp
[12] http://www2.digi-sign.com/digi-ca/administrator/online+certificate+status+protocol
[13] http://www2.digi-sign.com/certificate+authority/traditional+ca
[14] http://www2.digi-sign.com/digi-cast
[15] http://www2.digi-sign.com/compliance/introduction
[16] https://www.digi-sign.com/downloads/download.php?id=digi-ca-pdf alt=
[17] http://www2.digi-sign.com/demos/digi-ca
[18] https://www.digi-sign.com/downloads/download.php?id=digi-ca-pdf
[19] http://www2.digi-sign.com/digi-ca/managed+ca
[20] http://www2.digi-sign.com/digi-ca/software+ca
[21] http://www2.digi-sign.com/e+passport
[22] http://www2.digi-sign.com/ssl+certificate
[23] http://www2.digi-sign.com/digi-ca/administrator/digi-ca+xs+xp
[24] http://www2.digi-sign.com/digi-ca/administrator/digi-ca+xg
[25] http://www2.digi-sign.com/digi-cast/1
[26] http://www2.digi-sign.com/digi-cast/2
[27] http://www2.digi-sign.com/digi-cast/3
[28] http://www2.digi-sign.com/digi-cast/4
[29] http://www.digi-sign.com
[30] http://www2.digi-sign.com/digi-id
[31] http://www2.digi-sign.com/digi-ssl
[32] http://www2.digi-sign.com/trust+centre
[33] http://www2.digi-sign.com/digi-ca/administrator/certificate+authority+console
[34] http://www2.digi-sign.com/digi-ca/administrator/certificate+authority+console#ra-rs
[35] http://www2.digi-sign.com/digi-ca
[36] http://www2.digi-sign.com/service/digi-cast
[37] http://www2.digi-sign.com/digi-ca/service
[38] http://www2.digi-sign.com/digi-ca/server
[39] http://www2.digi-sign.com/digi-ca/shared
[40] http://www2.digi-sign.com/digi-ca/total+trust+management
[41] http://www2.digi-sign.com/digi-tasc
[42] http://www2.digi-sign.com/en/digi-trust/trusted+services+provider
[43] http://www2.digi-sign.com/books
[44] http://www2.digi-sign.com/en/about/third+party
[45] http://www2.digi-sign.com/training/digi-ca/server/ca+amc
[46] http://www2.digi-sign.com/training/digi-ca/server/ra+mc
[47] http://www2.digi-sign.com/training/digi-ca/server/lra
[48] http://www2.digi-sign.com/training/digi-ca/server/ra+rs
[49] https://www.digi-sign.com/downloads/download.php?id=digi-ca-admin-pdf
[50] http://www2.digi-sign.com/digital+document
[51] http://www2.digi-sign.com/about/choosing+digi-sign
[52] http://www2.digi-sign.com/compliance/list+standards
[53] http://www2.digi-sign.com/demos/digi-ca+presentation
[54] http://www2.digi-sign.com/support/knowledgebase
[55] http://www2.digi-sign.com/digi-ca/administrator/certificate+authority+environment
[56] http://www2.digi-sign.com/digi-ca/administrator/certificate+authority+environment#equipment
[57] http://www2.digi-sign.com/digi-ca/administrator/certificate+authority+environment#network
[58] http://www2.digi-sign.com/digi-ca/administrator/certificate+authority+environment#os alt=
[59] http://www2.digi-sign.com/digi-ca/administrator/certificate+authority+environment#os
[60] http://www2.digi-sign.com/key+ceremony
[61] http://www2.digi-sign.com/repository/certificate+practice+statement
[62] mailto:digi-cast@digi-sign.com
[63] http://www2.digi-sign.com/downloads/digi-ca admin
[64] http://www.sendmail.org
[65] http://www2.digi-sign.com/digi-ca/administrator/time+stamp
[66] http://www.openssl.org
[67] http://www.stunnel.org
[68] http://www.apache.org
[69] http://www.mysql.org
[70] http://www.perl.org
[71] http://www.php.net